Cybersecurity researchers took the wraps off an ongoing surveillance campaign directed against Colombian government institutions and private companies in the energy and metallurgical industries.
In a report published by ESET on Tuesday, the Slovak internet security company said the attacks — dubbed “Operation Spalax” — began in 2020, with the modus operandi sharing some similarities to an APT group targeting the country since at least April 2018, but also different in other ways.
The overlaps come in the form of phishing emails, which have similar topics and pretend to come from some of the same entities that were used in a February 2019 operation disclosed by QiAnXin researchers, and subdomain names used for command-and-control (C2) servers.
However, the two campaigns diverge in the attachments used for phishing emails, the remote access trojans (RATs) deployed, and the C2 infrastructure employed to fetch the malware dropped.
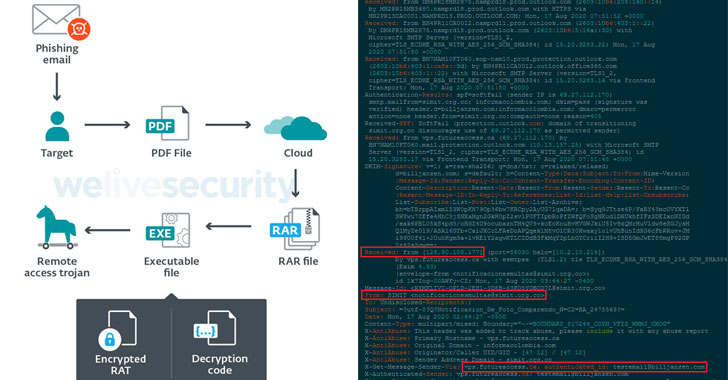
The attack chain begins with the targets receiving phishing emails that lead to the download of malicious files, which are RAR archives hosted on OneDrive or MediaFire containing various droppers responsible for decrypting and running RATs such as Remcos, njRAT, and AsyncRAT on a victimized computer.
The phishing emails cover a wide range of topics, including those about driving infractions, attend court hearings, and take mandatory COVID-19 tests, thus increasing the likelihood that unsuspecting users will open the messages.
In an alternate scenario observed by ESET, the attackers were also found to use heavily obfuscated AutoIt droppers that used shellcode to decrypt the payload and another to inject it into an already running process.
The RATs not only come with capabilities for remote control but also to spy on targets by capturing keystrokes, recording screenshots, stealing clipboard data, exfiltrating sensitive documents, and even downloading and executing other malware.
ESET’s analysis also revealed a scalable C2 architecture operated using a Dynamic DNS service that allowed them to dynamically assign a domain name to an IP address from a pool of 70 different domain names and 24 IP addresses in the second half of 2020 alone.
“Targeted malware attacks against Colombian entities have been scaled up since the campaigns that were described last year,” the researchers concluded. “The landscape has changed from a campaign that had a handful of C2 servers and domain names to a campaign with very large and fast-changing infrastructure with hundreds of domain names used since 2019.”