Cybersecurity researchers have unearthed a fourth new malware strain—designed to spread the malware onto other computers in victims’ networks—which was deployed as part of the SolarWinds supply chain attack disclosed late last year.
Dubbed “Raindrop” by Broadcom-owned Symantec, the malware joins the likes of other malicious implants such as Sunspot, Sunburst (or Solorigate), and Teardrop that were stealthily delivered to enterprise networks.
The latest finding comes amid a continued probe into the breach, suspected to be of Russian origin, that has claimed a number of U.S. government agencies and private sector companies.
“The discovery of Raindrop is a significant step in our investigation of the SolarWinds attacks as it provides further insights into post-compromise activity at organizations of interest to the attackers,” Symantec researchers said.
The cybersecurity firm said it discovered only four samples of Raindrop to date that were used to deliver the Cobalt Strike Beacon — an in-memory backdoor capable of command execution, keylogging, file transfer, privilege escalation, port scanning, and lateral movement.
Symantec, last month, had uncovered more than 2,000 systems belonging to 100 customers that received the trojanized SolarWinds Orion updates, with select targets infected with a second-stage payload called Teardrop that’s also used to install the Cobalt Strike Beacon.
“The way Teardrop is built, it could have dropped anything; in this case, it dropped Beacon, a payload included with Cobalt Strike,” Check Point researchers said, noting that it was possibly done to “make attribution harder.”
“While Teardrop was used on computers that had been infected by the original Sunburst Trojan, Raindrop appeared elsewhere on the network, being used by the attackers to move laterally and deploy payloads on other computers.”
It’s worth noting that the attackers used the Sunspot malware exclusively against SolarWinds in September 2019 to compromise its build environment and inject the Sunburst Trojan into its Orion network monitoring platform. The tainted software was then delivered to 18,000 of the company’s customers.
Microsoft’s analysis of the Solorigate modus operandi last month found that the operators carefully chose their targets, opting to escalate the attacks only in a handful of cases by deploying Teardrop based on intel amassed during an initial reconnaissance of the target environment for high-value accounts and assets.
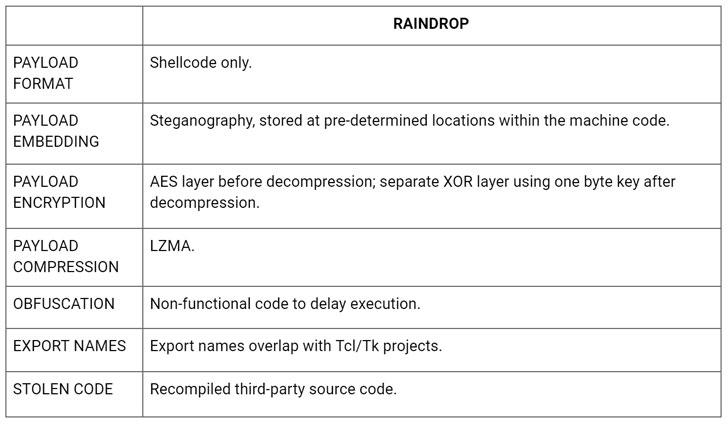
Now Raindrop (“bproxy.dll”) joins the mix. While both Teardrop and Raindrop act as a dropper for the Cobalt Strike Beacon, they also differ in a number of ways.
For a start, Teardrop is delivered directly by the initial Sunburst backdoor, whereas Raindrop seems to have been deployed with the goal of spreading across the victims’ network. What’s more, the malware shows up on networks where at least one computer has already been compromised by Sunburst, with no indication that Sunburst triggered its installation.
The two malware strains also use different packers and Cobalt Strike configurations.
Symantec did not identify the organizations impacted by Raindrop but said the samples were found in a victim system that was running computer access and management software and on a machine that was found to execute PowerShell commands to infect additional computers in the organization with the same malware.