Microsoft on Wednesday shared more specifics about the tactics, techniques, and procedures (TTPs) adopted by the attackers behind the SolarWinds hack to stay under the radar and avoid detection, as cybersecurity companies work towards getting a “clearer picture” of one of the most sophisticated attacks in recent history.
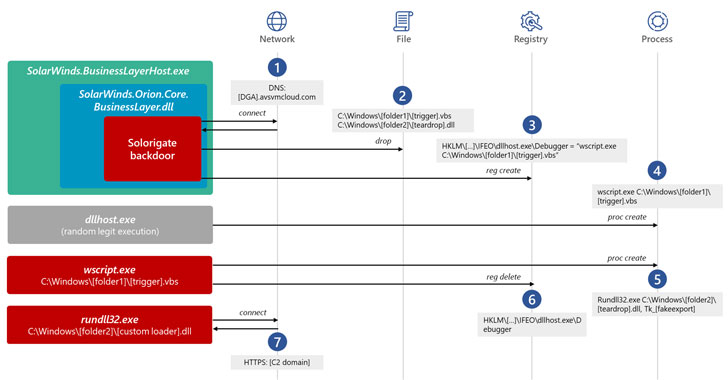
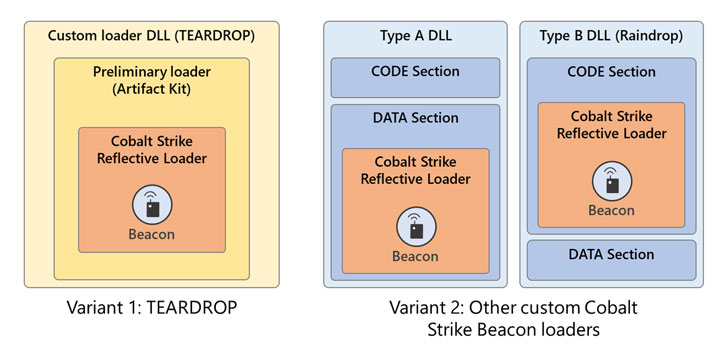
Calling the threat actor “skillful and methodic operators who follow operations security (OpSec) best practices,” the company said the attackers went out of their way to ensure that the initial backdoor (Sunburst aka Solorigate) and the post-compromise implants (Teardrop and Raindrop) are separated as much as possible so as to hinder efforts to spot their malicious activity.
“The attackers behind Solorigate are skilled campaign operators who carefully planned and executed the attack, remaining elusive while maintaining persistence,” researchers from Microsoft 365 Defender Research Team, Microsoft Threat Intelligence Center (MSTIC), and Microsoft Cyber Defense Operations Center (CDOC) said.
While the exact identity of the group tracked as StellarParticle (CrowdStrike), UNC2452 (FireEye), SolarStorm (Palo Alto Unit 42), and Dark Halo (Volexity) remain unknown as yet, the U.S. government earlier this month formally tied the espionage campaign to a group likely of Russian origin.
A Variety of Tactics to Stay Undetected
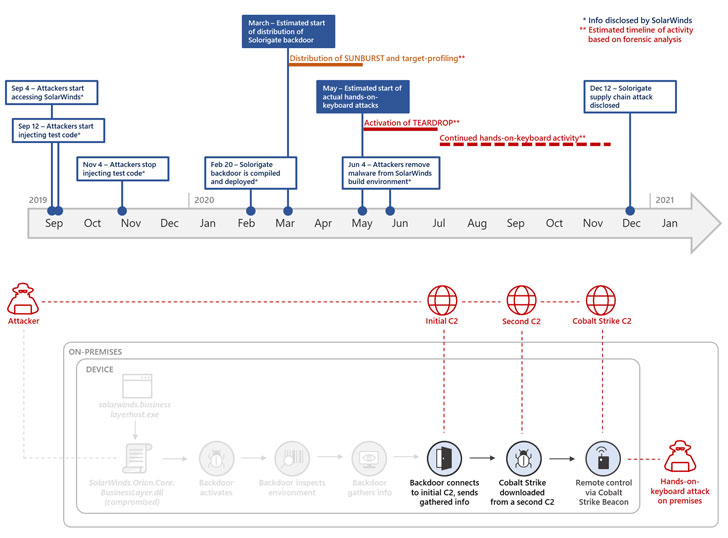
Microsoft’s timeline of the attacks shows that the fully-functional Sunburst DLL backdoor was compiled and deployed onto SolarWinds’ Orion platform on February 20, following which it was distributed in the form of tampered updates sometime in late March.
An almost two-month-long reconnaissance period to profile its targets — something that requires a stealthy persistence to remain undetected and collect valuable information — ultimately paved the way for the deployment of Cobalt Strike implants on selected victim networks in May and the removal of Sunburst from SolarWinds build environment on June 4.
But answers as to how and when the transition from Sunburst to Raindrop occurs has yielded little definitive clues, even if it appears that the attackers deliberately separated the Cobalt Strike loader’s execution from the SolarWinds process as an OpSec measure.
The idea is that in the event the Cobalt Strike implants were discovered on target networks, it wouldn’t reveal the compromised SolarWinds binary and the supply chain attack that led to its deployment in the first place.
The findings also make it clear that, while the hackers relied on an array of attack vectors, the trojanized SolarWinds software formed the core of the espionage operation:
- Methodic avoidance of shared indicators for each compromised host by deploying custom Cobalt Strike DLL implants on each system
- Camouflaging malicious tools and binaries to mimic existing files and programs already present on the compromised machine
- Disabling event logging using AUDITPOL before hands-on keyboard activity and enabling it back once complete
- Creating special firewall rules to minimize outgoing packets for certain protocols before running noisy network enumeration activities that were later removed after the network survey
- Executing lateral movement activities only after disabling security services on targeted hosts
- Allegedly using timestomping to change artifacts’ timestamps and leveraging wiping procedures and tools to prevent discovery of malicious DLL implants
Adopting a Zero Trust Mentality
“This attack was simultaneously sophisticated and ordinary,” Microsoft said. “The actor demonstrated sophistication in the breadth of tactics used to penetrate, expand across, and persist in affected infrastructure, but many of the tactics, techniques, and procedures (TTPs) were individually ordinary.”
To protect against such attacks in the future, the company recommends that organizations adopt a “zero trust mentality” to achieve the least privileged access and minimize risks by enabling multi-factor authentication.
“With Solorigate, the attackers took advantage of broad role assignments, permissions that exceeded role requirements, and in some cases abandoned accounts and applications which should have had no permissions at all,” Alex Weinert, Microsoft’s director of identity security, said.