In 1982, when SMTP was first specified, it did not contain any mechanism for providing security at the transport level to secure communications between mail transfer agents.
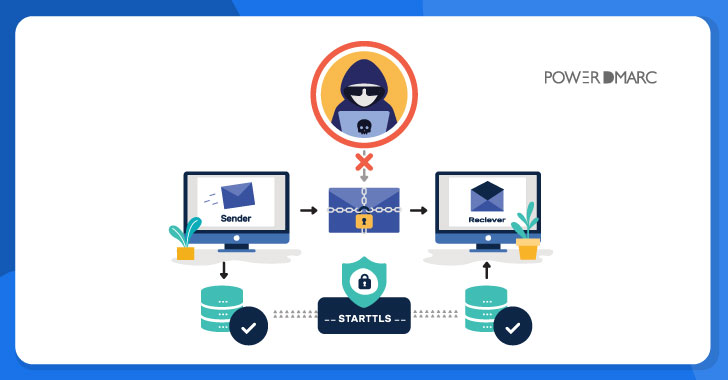
Later, in 1999, the STARTTLS command was added to SMTP that in turn supported the encryption of emails in between the servers, providing the ability to convert a non-secure connection into a secure one that is encrypted using TLS protocol.
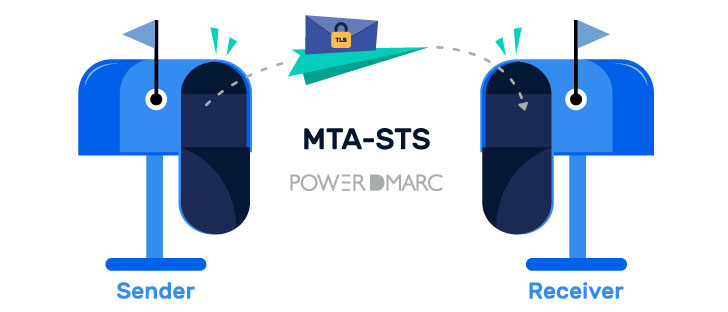
However, encryption is optional in SMTP, which implies that emails can be sent in plaintext. Mail Transfer Agent-Strict Transport Security (MTA-STS) is a relatively new standard that enables mail service providers the ability to enforce Transport Layer Security (TLS) to secure SMTP connections and to specify whether the sending SMTP servers should refuse to deliver emails to MX hosts that that does not offer TLS with a reliable server certificate. It has been proven to successfully mitigate TLS downgrade attacks and Man-in-the-Middle (MitM) attacks.
SMTP TLS Reporting (TLS-RPT) is a standard that enables reporting issues in TLS connectivity experienced by applications that send emails and detect misconfigurations. It enables the reporting of email delivery issues that take place when an email isn’t encrypted with TLS. In September 2018, the standard was first documented in RFC 8460.
Why Do Your Emails Require Encryption in Transit?
The primary goal is to improve transport-level security during SMTP communication, ensuring the privacy of email traffic. Moreover, encryption of inbound messages addressed to your domain enhances information security, using cryptography to safeguard electronic information.
Furthermore, cryptographic attacks such as Man-in-the-Middle (MitM) SMTP Downgrade attacks, as well as DNS spoofing attacks, have been gaining popularity in recent times and have become a common practice among cybercriminals, which can be evaded by enforcing TLS encryption and extending support to secure protocols.
How Is a MITM Attack Launched?
Since encryption had to be retrofitted into SMTP protocol, the upgrade for encrypted delivery has to rely on a STARTTLS command. A MITM attacker can easily exploit this feature by performing an SMTP downgrade attack on the SMTP connection by tampering with the upgrade command by replacing or deleting it, forcing the client to fall back to sending the email in plaintext.
After intercepting the communication, a MITM attacker can easily steal the decrypted information and access the email’s content. This is because SMTP is the industry standard for mail transfer. It uses opportunistic encryption, which implies that encryption is optional and emails can still be delivered in cleartext.
MITM attacks can also be launched in the form of a DNS Spoofing Attack:
As DNS is an unencrypted system, a cybercriminal can replace the MX records in the DNS query response with a mail server that they have access to and are in control of, thereby easily diverting the DNS traffic flowing through the network.
The mail transfer agent, in that case, delivers the email to the server of the attacker, enabling him to access and tamper with the email content. The email can be subsequently forwarded to the intended recipient’s server without being detected.
When you deploy MTA-STS, the MX addresses are fetched over DNS and compared to those found in the MTA-STS policy file, which is served over an HTTPS secured connection, thereby mitigating DNS spoofing attacks.
Apart from enhancing information security and mitigating pervasive monitoring attacks, encrypting messages in transit also solves multiple SMTP security problems.
Achieving Enforced TLS Encryption of Emails with MTA-STS
If you fail to transport your emails over a secure connection, your data could be compromised or even modified and tampered with by a cyber attacker.
Here is where MTA-STS steps in and fixes this issue, enabling safe transit for your emails as well as successfully mitigating cryptographic attacks and enhancing information security by enforcing TLS encryption.
Simply put,MTA-STS enforces the transfer of emails over a TLS encrypted pathway. In case an encrypted connection cannot be established, the email is not delivered at all, instead of being delivered in cleartext.
Furthermore, MTAs fetch and store MTA-STS policy files, which securely serve the MX addresses making it more difficult for attackers to launch a DNS spoofing attack.
MTA-STS offers protection against :
- Downgrade attacks
- Man-In-The-Middle (MITM) attacks
- It solves multiple SMTP security problems, including expired TLS certificates and lack of support for secure protocols.
- DNS Spoofing attacks
Major mail service providers, such as Microsoft, Oath, and Google, support MTA-STS. Google, being the largest industry player, attains center-stage when adopting any protocol, and the adoption of MTA-STS by google indicates the extension of support towards secure protocols and highlights the importance of email encryption in transit.
Troubleshooting Issues in Email Delivery with TLS-RPT
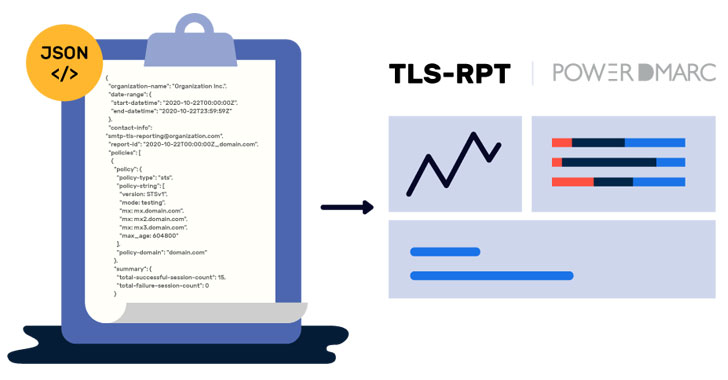
SMTP TLS Reporting provides domain owners with diagnostic reports (in JSON file format) with elaborate details on emails addressed to your domain and face delivery issues or couldn’t be delivered due to a downgrade attack or other issues so that you can fix the problem proactively.
As soon as you enable TLS-RPT, acquiescent Mail Transfer Agents will begin sending diagnostic reports regarding email delivery issues between communicating servers to the designated email domain.
The reports are typically sent once a day, covering and conveying the MTA-STS policies observed by senders, traffic statistics as well as information on failure or issues in email delivery.
The need for deploying TLS-RPT :
- In case an email fails to be sent to your domain due to any issue in delivery, you will get notified.
- TLS-RPT provides enhanced visibility on all your email channels so that you gain better insight on all that is going on in your domain, including messages that are failing to be delivered.
- TLS-RPT provides in-depth diagnostic reports that enable you to identify and get to the root of the email delivery issue and fix it without any delay.
Adopting MTA-STS and TLS-RPT Made Easy and Speedy by PowerDMARC
MTA-STS requires an HTTPS-enabled web server with a valid certificate, DNS records, and constant maintenance. PowerDMARC makes your life a whole lot easier by handling all of that for you, completely in the background- from generating certificates and MTA-STS policy files to policy enforcement, we help you evade the complexities involved in adopting the protocol. Once we help you set it up with just a few clicks, you never even have to think about it again.
With the help of PowerDMARC’s Email Authentication Services, you can deploy Hosted MTA-STS at your organization without the hassle and at a very speedy pace, with the help of which you can enforce emails to be sent to your domain over a TLS encrypted connection, thereby making your connection secure and keeping MITM attacks at bay.
PowerDMARC makes your life easier by making the process of implementation of TLS-RPT easy and speedy, at your fingertips! As soon as you sign up with PowerDMARC and enable SMTP TLS Reporting for your domain, we take the pain of converting the complicated JSON files containing your reports of email delivery issues, into simple, readable documents (per result and per sending source), that you can go through and understand with ease! PowerDMARC’s platform automatically detects and subsequently conveys the issues you are facing in email delivery, so that you can promptly address and resolve them in no time!
PowerDMARC is a single email authentication SaaS platform that combines all email authentication best practices such as DMARC, SPF, DKIM, BIMI, MTA-STS and TLS-RPT, under the same roof. So sign up to get your free DMARC Analyzer today!