An evolving phishing campaign observed at least since May 2020 has been found to target high-ranking company executives across manufacturing, real estate, finance, government, and technological sectors with the goal of obtaining sensitive information.
The campaign hinges on a social engineering trick that involves sending emails to potential victims containing fake Office 365 password expiration notifications as lures. The messages also include an embedded link to retain the same password that, when clicked, redirects users to a phishing page for credential harvesting.
“The attackers target high profile employees who may not be as technically or cybersecurity savvy, and may be more likely to be deceived into clicking on malicious links,” Trend Micro researchers said in a Monday analysis.
“By selectively targeting C-level employees, the attacker significantly increases the value of obtained credentials as they could lead to further access to sensitive personal and organizational information, and used in other attacks.”
According to the researchers, the targeted email addresses were mostly collected from LinkedIn, while noting that the attackers could have purchased such target lists from marketing websites that offer CEO/CFO email and social media profile data.
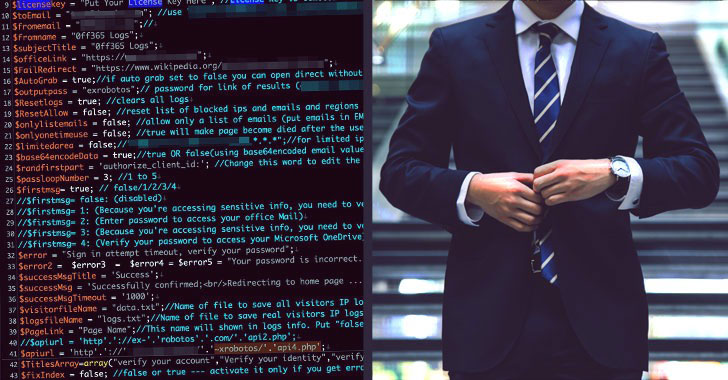
The Office 365 phishing kit, currently in its fourth iteration (V4), is said to have been originally released in July 2019, with additional features added to detect bot scanning or crawling attempts and provide alternative content when bots are detected. Interestingly, the alleged developer behind the malware announced V4’s availability on their “business” Facebook page in mid-2020.
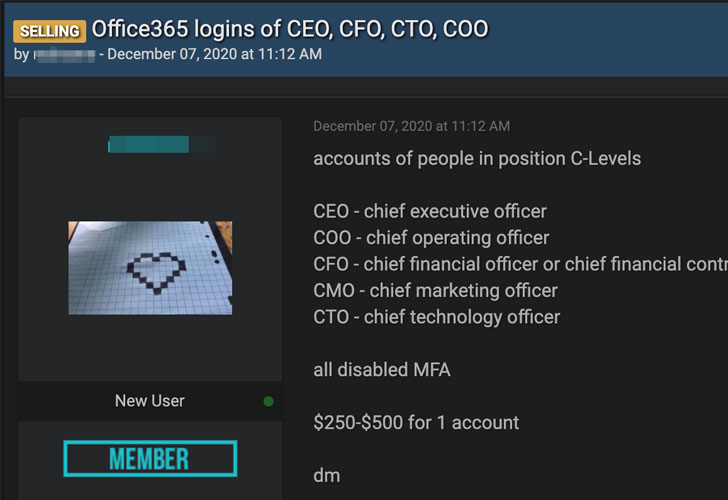
Aside from selling the phishing kit, the actor has also been found to peddle account credentials of CEOs, chief financial officers (CFOs), finance department members, and other high-profile executives on social media pages.
What’s more, Trend Micro’s investigation unearthed a possible link to a user handle on underground forums that was spotted selling a credential harvester tool as well as stolen C-Level account passwords anywhere between $250 to $500, echoing previous reports late last year.
The researchers uncovered at least eight compromised phishing sites hosting the V4 phishing kit, raising the possibility that they were used by different actors for a wide range of phishing campaigns directed against CEOs, presidents, board members, and founders of companies located in the U.S., the U.K., Canada, Hungary, the Netherlands, and Israel.
“While organizations are aware and wary of the information they include in public-facing websites and platforms, their respective employees should be constantly reminded to be mindful of the details they disclose on personal pages,” the researchers concluded. “These can be easily used against them for attacks using social engineering techniques.”