Researchers have disclosed a new family of Android malware that abuses accessibility services in the device to hijack user credentials and record audio and video.
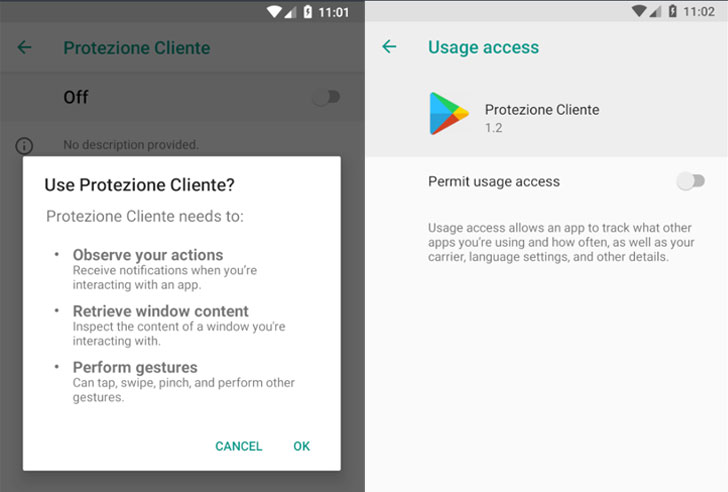
Dubbed “Oscorp” by Italy’s CERT-AGID, the malware “induce(s) the user to install an accessibility service with which [the attackers] can read what is present and what is typed on the screen.”
So named because of the title of the login page of its command-and-control (C2) server, the malicious APK (called “Assistenzaclienti.apk” or “Customer Protection”) is distributed via a domain named “supportoapp[.]com,” which upon installation, requests intrusive permissions to enable the accessibility service and establishes communications with a C2 server to retrieve additional commands.
Furthermore, the malware repeatedly reopens the Settings screen every eight seconds until the user turns on permissions for accessibility and device usage statistics, thus pressurizing the user into granting the extra privileges.
Once the access is provisioned, the malware exploits the permissions to log keystrokes, uninstall apps on the device, make calls, send SMS messages, steal cryptocurrency by redirecting payments made via Blockchain.com Wallet app, and access two-factor authentication codes from the Google Authenticator app.
The attacker-controlled wallet had $584 as of January 9, the researchers said.
In the final step, the malware exfiltrates the captured data — along with system information (e.g., apps installed, phone model, carrier) — to the C2 server, in addition to fetching commands from the server that allows it to launch the Google Authenticator app, steal SMS messages, uninstall apps, launch specific URLs, and record audio and video of the screen through WebRTC.
What’s more, users opening the apps targeted by the malware are displayed a phishing page that asks for their username and password, CERT noted, adding the style of this screen varies from app to app and that it’s designed with an intent to trick the victim into providing the information.
The exact kind of applications singled out by this malware remains unclear, but the researchers said it could be any app that deals with sensitive data, such as those for banking and messaging.
“Android protections prevent malware from doing any kind of damage until the user enables [accessibility] service,” CERT-AGID concluded. “Once enabled, however, a ‘dam’ opens up. In fact, Android has always had a very permissive policy towards app developers, leaving the ultimate decision to trust an app or not to the end user.”