A “persistent attacker group” with alleged ties to Hezbollah has retooled its malware arsenal with a new version of a remote access Trojan (RAT) to break into companies worldwide and extract valuable information.
In a new report published by the ClearSky research team on Thursday, the Israeli cybersecurity firm said it identified at least 250 public-facing web servers since early 2020 that have been hacked by the threat actor to gather intelligence and steal the company’s databases.
The orchestrated intrusions hit a slew of companies located in the U.S., the U.K., Egypt, Jordan, Lebanon, Saudi Arabia, Israel, and the Palestinian Authority, with a majority of the victims representing telecom operators (Etisalat, Mobily, Vodafone Egypt), internet service providers (SaudiNet, TE Data), and hosting and infrastructure service providers (Secured Servers LLC, iomart).
First documented in 2015, Volatile Cedar (or Lebanese Cedar) has been known to penetrate a large number of targets using various attack techniques, including a custom-made malware implant codenamed Explosive.
Volatile Cedar has been previously suspected of Lebanese origins — specifically Hezbollah’s cyber unit — in connection with a cyberespionage campaign in 2015 that targeted military suppliers, telecom companies, media outlets, and universities.
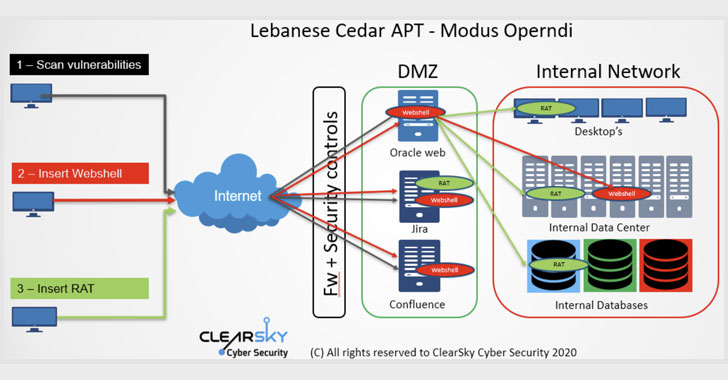
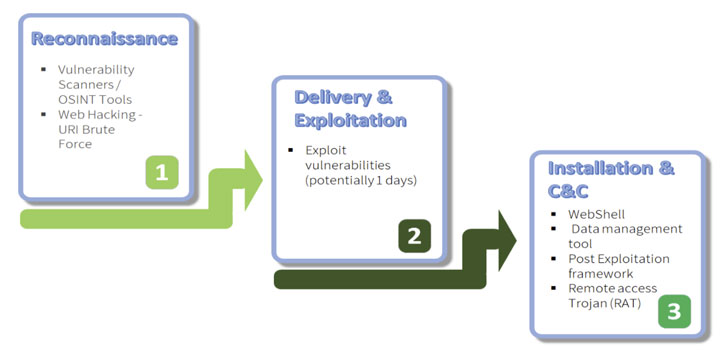
The 2020 attacks were no different. The hacking activity uncovered by ClearSky matched operations attributed to Hezbollah based on code overlaps between the 2015 and 2020 variants of the Explosive RAT, which is deployed onto victims’ networks by exploiting known 1-day vulnerabilities in unpatched Oracle and Atlassian web servers.
Using the three flaws in the servers (CVE-2019-3396, CVE-2019-11581, and CVE-2012-3152) as an attack vector to gain an initial foothold, the attackers then injected a web shell and a JSP file browser, both of which were used to move laterally across the network, fetch additional malware, and download the Explosive RAT, which comes with capabilities to record keystrokes, capture screenshots, and execute arbitrary commands.
“The web shell is used to carry out various espionage operations over the attacked web server, including potential asset location for further attacks, file installation server configuration and more,” the researchers noted, but not before obtaining escalated privileges to carry out the tasks and transmit the results to a command-and-control (C2) server.
In the five years since the Explosive RAT was first seen, ClearSky said new anti-debugging features were added to the implant in its latest iteration (V4), with the communications between the compromised machine and the C2 server now encrypted.
While it’s not surprising for threat actors to keep a low profile, the fact that Lebanese Cedar managed to stay hidden since 2015 without attracting any attention whatsoever implies the group may have ceased operations for prolonged periods in between to avoid detection.
ClearSky noted that the group’s use of web shell as its primary hacking tool could have been instrumental in leading researchers to a “dead-end in terms of attribution.”
“Lebanese Cedar has shifted its focus significantly. Initially they attacked computers as an initial point of access, then progressed to the victim’s network then further progressing (sic) to targeting vulnerable, public facing web servers,” the researchers added.