New details have emerged about a vast network of rogue extensions for Chrome and Edge browsers that were found to hijack clicks to links in search results pages to arbitrary URLs, including phishing sites and ads.
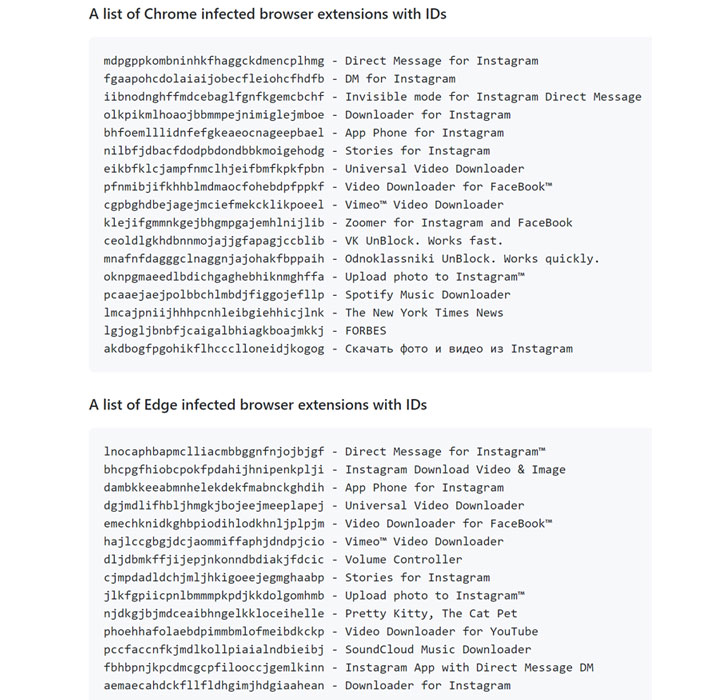
Collectively called “CacheFlow” by Avast, the 28 extensions in question — including Video Downloader for Facebook, Vimeo Video Downloader, Instagram Story Downloader, VK Unblock — made use of a sneaky trick to mask its true purpose: Leverage Cache-Control HTTP header as a covert channel to retrieve commands from an attacker-controlled server.
All the backdoored browser add-ons have been taken down by Google and Microsoft as of December 18, 2020, to prevent more users from downloading them from the official stores.
According to telemetry data gathered by the firm, the top three infected countries were Brazil, Ukraine, and France, followed by Argentina, Spain, Russia, and the U.S.
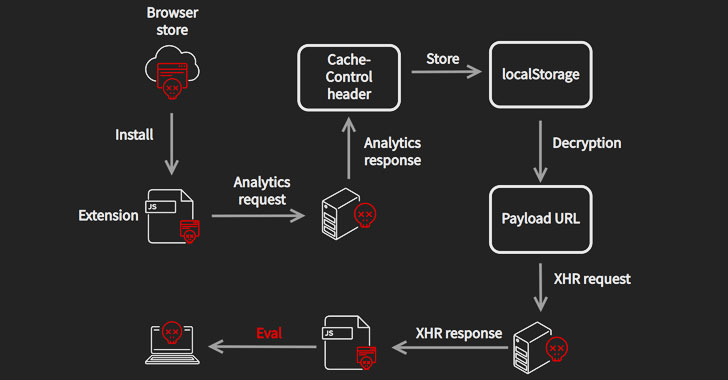
The CacheFlow sequence began when unsuspecting users downloaded one of the extensions in their browsers that, upon installation, sent out analytics requests resembling Google Analytics to a remote server, which then beamed back a specially-crafted Cache-Control header containing hidden commands to fetch a second-stage payload that functioned as a downloader for the final JavaScript payload.
This JavaScript malware amassed birth dates, email addresses, geolocation, and device activity, with a specific focus on collecting the data from Google.
“To retrieve the birthday, CacheFlow made an XHR request to https://myaccount.google.com/birthday and parsed out the birth date from the response,” Avast researchers Jan Vojtěšek and Jan Rubín observed.
In the final step, the payload injected another piece of JavaScript into each tab, using it to hijack clicks leading to legitimate websites, as well as modify search results from Google, Bing, or Yahoo to reroute the victim to a different URL.
That’s not all. The extensions not only avoided infecting users who were likely to be web developers — something that was deduced by computing a weighted score of the extensions installed or by checking if they accessed locally-hosted websites (e.g., .dev, .local, or .localhost) — they were also configured to not exhibit any suspicious behavior during the first three days post-installation.
Avast said the myriad tricks employed by the malware authors to escape detection may have been a crucial factor that allowed it to execute malicious code in the background and stealthily infect millions of victims, with evidence suggesting that the campaign may have been active since at least October 2017.
“We usually trust that the extensions installed from official browser stores are safe,” the researchers said. “But that is not always the case as we recently found.”
“CacheFlow was notable in particular for the way that the malicious extensions would try to hide their command and control traffic in a covert channel using the Cache-Control HTTP header of their analytics requests. We believe this is a new technique.”
The full list of indicators of compromise (IoCs) associated with the campaign can be accessed here.