In what’s a novel supply chain attack, a security researcher managed to breach over 35 major companies’ internal systems, including that of Microsoft, Apple, PayPal, Shopify, Netflix, Yelp, Tesla, and Uber, and achieve remote code execution.
The technique, called dependency confusion or a substitution attack, takes advantage of the fact that a piece of software may include components from a mix of private and public sources.
These external package dependencies, which are fetched from public repositories during a build process, can pose an attack opportunity when an adversary uploads a higher version of a private module to the public feed, causing a client to automatically download the bogus “latest” version without requiring any action from the developer.
“From one-off mistakes made by developers on their own machines, to misconfigured internal or cloud-based build servers, to systemically vulnerable development pipelines, one thing was clear: squatting valid internal package names was a nearly sure-fire method to get into the networks of some of the biggest tech companies out there, gaining remote code execution, and possibly allowing attackers to add backdoors during builds,” security researcher Alex Birsan detailed in a write-up.
Birsan has been collectively awarded over $130,000 in bug bounties for his efforts.
To carry out the attack, Birsan began by collecting names of private internal packages used by major companies off GitHub, posts on various internet forums, and JavaScript files that list a project’s dependencies, and then uploaded rogue libraries using those same names to open-source package hosting services such as npm, PyPI, and RubyGems.
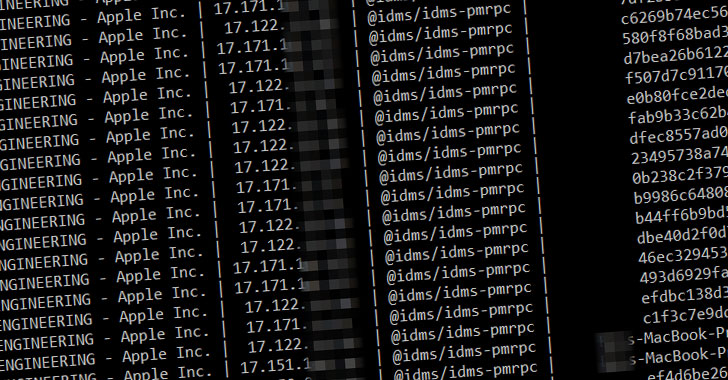
“[Shopify’s] build system automatically installed a Ruby gem named ‘shopify-cloud’ only a few hours after I had uploaded it, and then tried to run the code inside it,” Birsan noted, adding a Node package that he uploaded to npm in August 2020 was executed on multiple machines inside Apple’s network, affecting projects related to the company’s Apple ID authentication system.
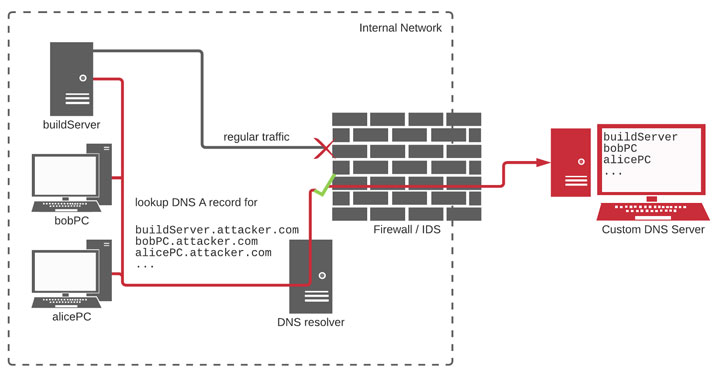
Birsan ultimately used the counterfeit packages to obtain a record of every machine where the packages were installed and exfiltrated the details over DNS for the reason that the “traffic would be less likely to be blocked or detected on the way out.”
The concern that a package with the higher version would be pulled by the app-building process regardless of wherever it’s located hasn’t escaped Microsoft’s notice, which released a new white paper on Tuesday outlining three ways to mitigating risks when using private package feeds.
Chief among its recommendations are as follows —
- Reference one private feed, not multiple
- Protect private packages using controlled scopes, namespaces, or prefixes, and
- Utilize client-side verification features such as version pinning and integrity verification