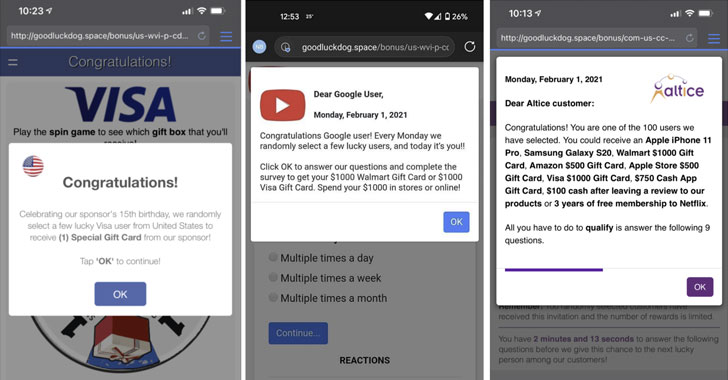
A malvertising group known as “ScamClub” exploited a zero-day vulnerability in WebKit-based browsers to inject malicious payloads that redirected users to fraudulent websites gift card scams.
The attacks, first spotted by ad security firm Confiant in late June 2020, leveraged a bug (CVE-2021–1801) that allowed malicious parties to bypass the iframe sandboxing policy in the browser engine that powers Safari and Google Chrome for iOS and run malicious code.
Specifically, the technique exploited the manner how WebKit handles JavaScript event listeners, thus making it possible to break out of the sandbox associated with an ad’s inline frame element despite the presence of “allow-top-navigation-by-user-activation” attribute that explicitly forbids any redirection unless the click event occurs inside the iframe.
To test this hypothesis, the researchers set about creating a simple HTML file containing a cross-origin sandboxed iframe and a button outside it that triggered an event to access the iframe and redirect the clicks to rogue websites.
“The […] button is outside of the sandboxed frame after all,” Confiant researcher Eliya Stein said. “However, if it does redirect, that means we have a browser security bug on our hands, which turned out to be the case when tested on WebKit based browsers, namely Safari on desktop and iOS.”
Following responsible disclosure to Apple on June 23, 2020, the tech giant patched WebKit on December 2, 2020, and subsequently addressed the issue “with improved iframe sandbox enforcement” as part of security updates released earlier this month for iOS 14.4 and macOS Big Sur.
Confiant said the operators of ScamClub have delivered more than 50 million malicious impressions over the last 90 days, with as many as 16MM impacted ads being served in a single day.
“On the tactics side, this attacker historically favors what we refer to as a ‘bombardment’ strategy,” Stein elaborated.
“Instead of trying to fly under the radar, they flood the ad tech ecosystem with tons of horrendous demand well aware that the majority of it will be blocked by some kind of gatekeeping, but they do this at incredibly high volumes in the hopes that the small percentage that slips through will do significant damage.”
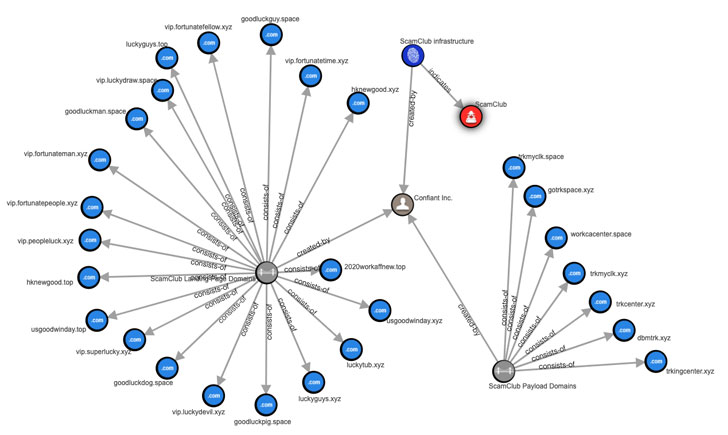
Confiant has also published a list of websites used by the ScamClub group to run its recent scam campaign.