It’s no secret that sysadmins have plenty on their plates. Managing, troubleshooting, and updating software or hardware is a tedious task. Additionally, admins must grapple with complex webs of permissions and security. This can quickly become overwhelming without the right tools.
If you’re a sysadmin seeking to simplify your workflows, you’re in luck. We’ve gathered some excellent software picks to help tackle different duties more efficiently.
Thankfully, these free tools are also respectful of tight budgets—without sacrificing core functionality.
Whether you are part of an organization with many members or numerous resources, keeping track of permissions can be challenging. Changes in responsibilities, titles, or even employment statuses can influence one’s access to proprietary data. Each user has unique privileges.
We not only need to visualize these but manage them on a case-by-case basis. Previously, this would require a deep, tedious dive into file systems, shares, and AD groups.
SolarWinds Permissions Analyzer streamlines this process. Once the software has system access, you may inspect user permissions using the search bars. This lets you cross-reference specific users with key file groups—showing read access, write or modify access, delete or create capabilities, and even full control.
How does Permissions Analyzer (PA) check this?
- The tool performs a user search
- PA reads NTFS rights and calculates NTFS permissions
- PA then reads membership information for any pertinent groups
- PA searches for local group membership information
- The program reads share rights, calculating share permissions
- Finally, results are merged and finalized
This process is incredibly quick. Referring to the figure above, the way SolarWinds displays this information is its bread and butter. Permissions Analyzer organizes the output into a hierarchical table—including expandable categories based on inheritance. For instance, you can see if group membership impacts specific permissions statuses.
This information is shown in concert with NTFS, Shares, and Total permissions. The GUI allows for quick consumption using iconography and color (partially adopting the traffic light scheme). Therefore, PA excels where alternatives fall short: simplicity and usability.
Note that SolarWinds Permissions Analyzer is an investigative tool. It doesn’t allow you to edit permissions within the app; however, it provides rapid visibility into your permissions structure.
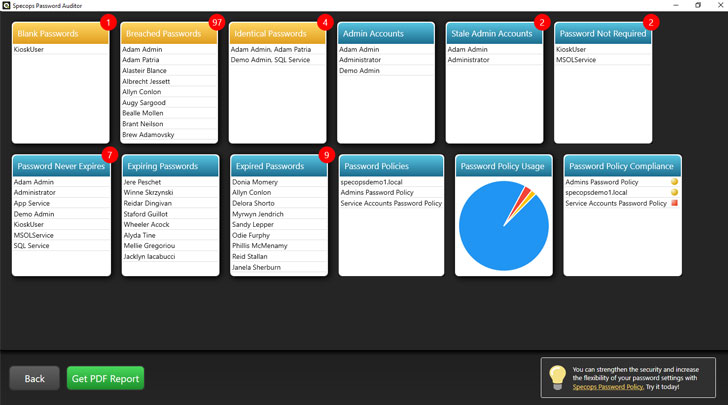
Active Directory password security is vitally important, yet many organizations routinely fail short. Teams can institute password policies—both broad and fine-grained. But, are these efforts adequate? Specops Password Auditor can answer that question and more for you.
Password Auditor does what its namesake implies by scanning all user accounts within your environment to detect leaked passwords. Specops maintains a dictionary of compromised passwords; should any user passwords match, Password Auditor highlights them within the tool.
The central dashboard displays the following in a unified view:
- Breached passwords (and their corresponding users)
- Identical passwords (and matching users)
- Admin account names and stale variants
- Accounts with expired passwords
- Various password policies according to users, roles, and security
- Password policy usage and compliance (pass, caution, fail)
This breakdown is easier to read at a glance than most others out there—including some paid options. It’s also a great supplement to Azure AD Password Protection. While that functionally applies password policies to domain controllers, Password Auditor determines if these policies are ultimately working properly.
Are dormant accounts causing issues? Perhaps password length and complexity aren’t up to snuff. Password Auditor can shed light on these issues.
Like SolarWinds Permissions Analyzer, Specops’ tool conducts a scan of your users and policies. This process is quick and easy to monitor. Password Auditor automatically compiles a report of its findings, which is available as a downloadable PDF. You may also export to CSV.
Next, you can measure your policies against standards set by NIST, PCI, Microsoft, and SANS. It’s even easy to test your policies against brute-force attacks. This promotes adherence to best practices.
Worried about potential tampering? Specops Password Auditor is a read-only program.
For lovers of the now-deprecated Microsoft Message Analyzer, Wireshark has emerged as a popular replacement. The multi-platform tool supports an expansive list of operating systems:
- Windows 8+ and Windows Server 2012(R)+
- macOS 10.12+
- Over a dozen versions of UNIX, Linux, and BSD
Wireshark can inspect hundreds of network protocols, and even when that list is continually evolving. Accordingly, Wireshark can capture data whether you’re online or offline, allowing for uninterrupted inspection. Wireshark also supports over 20 capture file formats.
You may retrospectively parse logs using your preferred interface—whether that be the GUI or the TShark terminal utility. Files compressed using gzip can be uncompressed on the fly, which saves time.
Want to inspect the packets traveling throughout your network? Simply take advantage of the three-pane browser view, which keeps data well organized. Layouts also feature collapsible sections—letting you reveal additional details on demand or keep the interface uncluttered.
What else does Wireshark offer?
- Numerous display filters
- VoIP analysis
- Real-time data reads over ethernet, IEEE, Bluetooth, USB, token ring, and more
- Decryption for IPsec, Kerberos, SNMP, ISAKMP, SSL/TLS, WEP, WPA, and WPA2
- Customizable coloring rules
- Easy data export via XML, PostScript, CSV, or plain text
Wireshark remains open source to this day, and the developers maintain high-quality documentation on Wireshark’s website and GitHub pages.
Even when your password policy is sound, it’s important to keep passwords from becoming stale. This can prevent hackers from gaining repeat access to a compromised account over the long term.
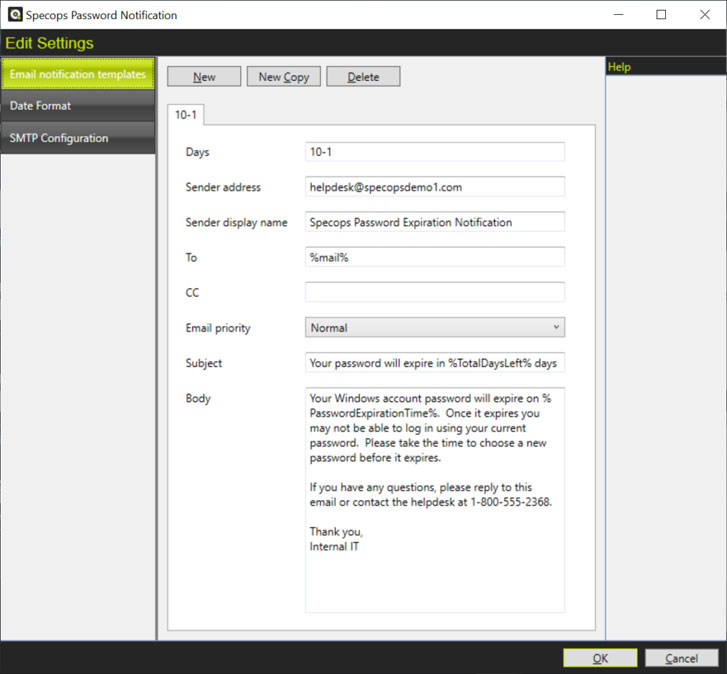
Unanticipated expiry can also separate users from vital resources. Accordingly, companies enforcing periodic password expiry should look no further than Specops Password Notification.
Password Notification’s premise is pretty simple: prevent a lockout, thwart unwanted access, and keep users connected from afar. Additionally, the goal is to lessen the burden on help desk technicians and universally prevent frustration. How exactly does the tool work?
- The pwdLastSet attribute is compared to the maximum password age. This age is outlined in a given domain policy or fine-grained password policy
- Users impacted by relevant GPOs are sent notification emails when their password nears expiry. This warning period, message, and subject are customizable
- IT admins can communicate with all users—even those on remote networks or VPNs
Regular Windows users don’t receive these alerts when they’re off the network.
How else can you tailor emails in Password Notification? Email frequency is adjustable, as are recipients (including multiple contacts). You can also set priority levels that change dynamically as deadlines approach. Seamless time zone integrations are also available.
Manual methods might otherwise rely on scripting via PowerShell. Specops’ tool gives users rich functionality out of the box, without the need for heavy configuration.