Threat actors known for keeping a low profile do so by ceasing operations for prolonged periods in between to evade attracting any attention as well as constantly refining their toolsets to fly below the radar of many detection technologies.
One such group is FIN8, a financially motivated threat actor that’s back in action after a year-and-a-half hiatus with a powerful version of a backdoor with upgraded capabilities including screen capturing, proxy tunneling, credential theft, and fileless execution.
First documented in 2016 by FireEye, FIN8 is known for its attacks against the retail, hospitality, and entertainment industries while making use of a wide array of techniques such as spear-phishing and malicious tools like PUNCHTRACK and BADHATCH to steal payment card data from point-of-sale (POS) systems.
“The FIN8 group is known for taking long breaks to improve TTPs and increase their rate of success,” Bitdefender researchers said in a report published today. “The BADHATCH malware is a mature, highly advanced backdoor that uses several evasion and defense techniques. The new backdoor also attempts to evade security monitoring by using TLS encryption to conceal Powershell commands.”
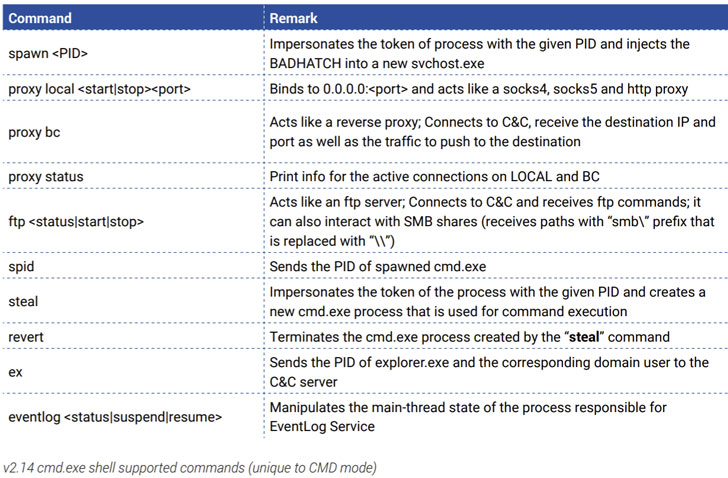
BADHATCH, since its discovery in 2019, has been deployed as an implant capable of running attacker-supplied commands retrieved from a remote server, in addition to injecting malicious DLLs in a current process, gathering system information, and exfiltrating data to the server.
Noting that at least three different variants of the backdoor (v2.12 to 2.14) have been spotted since April 2020, the researchers said the latest version of BADHATCH abuses a legitimate service called sslp.io to thwart detection during the deployment process, using it to download a PowerShell script, which in turn executes the shellcode containing the BADHATCH DLL.
The PowerShell script, besides taking responsibility for achieving persistence, also takes care of privilege escalation to ensure that all commands post the script’s execution are run as the SYSTEM user.
Furthermore, a second evasion technique adopted by FIN8 involves passing off communications with the command-and-control (C2) server that masquerade as legitimate HTTP requests.
According to Bitdefender, the new wave of attacks is said to have taken place over the past year and directed against insurance, retail, technology, and chemical industries in the U.S., Canada, South Africa, Puerto Rico, Panama, and Italy.
“Like most persistent and skilled cyber-crime actors, FIN8 operators are constantly refining their tools and tactics to avoid detection,” the researchers concluded, urging businesses to “separate the POS network from the ones used by employees or guests” and filter out emails containing malicious or suspicious attachments.