New research into 5G architecture has uncovered a security flaw in its network slicing and virtualized network functions that could be exploited to allow data access and denial of service attacks between different network slices on a mobile operator’s 5G network.
AdaptiveMobile shared its findings with the GSM Association (GSMA) on February 4, 2021, following which the weaknesses were collectively designated as CVD-2021-0047.
5G is an evolution of current 4G architectures and is based on what’s called a service-based architecture (SBA) that provides a modular framework to deploy a set of interconnected network functions, allowing consumers to discover and authorize their access to a plethora of services.
The network functions are also responsible for registering subscribers, managing sessions and subscriber profiles, storing subscriber data, and connecting the users (UE or user equipment) to the internet via a base station (gNB). What’s more, each network function of the SBA can offer a specific service but at the same time can also request a service from another network function.
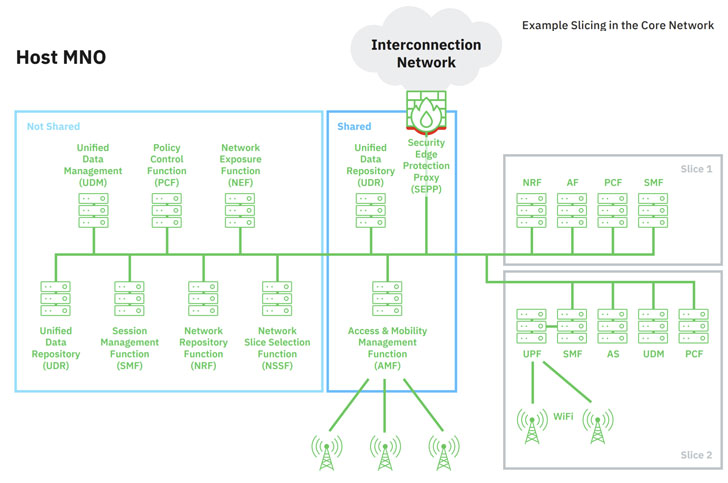
One of the ways the core SBA of the 5G network is orchestrated is through a slicing model. As the name indicates, the idea is to “slice” the original network architecture in multiple logical and independent virtual networks that are configured to meet a specific business purpose, which, in turn, dictates the quality of service (QoS) requirements necessary for that slice.
Additionally, each slice in the core network consists of a logical group of network functions (NFs) that can be exclusively assigned to that slice or be shared among different slices.
Put differently, by creating separate slices that prioritize certain characteristics (e.g., large bandwidths), it enables a network operator to carve out solutions that are customized to particular industries.
For instance, a mobile broadband slice can be used to facilitate entertainment and Internet-related services, an Internet of Things (IoT) slice can be used to offer services tailored to retail and manufacturing sectors, while a standalone low latency slice can be designated for mission-critical needs such as healthcare and infrastructure.
“The 5G SBA offers many security features which includes lessons learned from previous generations of network technologies,” AdaptiveMobile said in a security analysis of 5G core network slicing. “But on the other hand, 5G SBA is a completely new network concept that opens the network up to new partners and services. These all lead to new security challenges.”
According to the mobile network security firm, this architecture not only poses fresh security concerns that stem from a need to support legacy functions but also from a “massive increase in protocol complexity” as a consequence of migrating from 4G to 5G and in the process opening the door to a multitude of attacks, including —
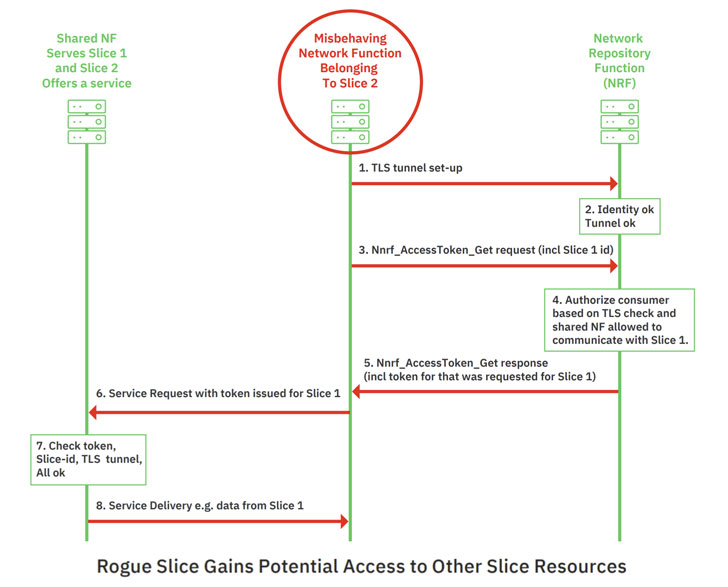
- Malicious access to a slice by brute-forcing its slice differentiator, an optional value set by the network operator for distinguishing between slices of the same type, thereby allowing a rogue slice to gain unauthorized information from a second slice like Access and Mobility Management Function (AMF), which maintains knowledge of a user equipment’s location.
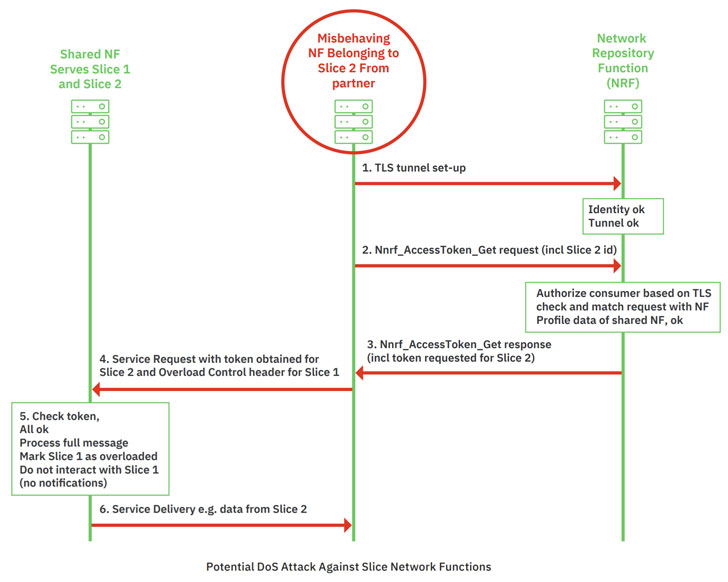
- Denial-of-service (DoS) against another network function by taking advantage of a compromised slice.
The attacks hinge on a design quirk that there are no checks to ensure that the slice identity in the signaling layer request matches that used in the transport layer, thus permitting an adversary connected to the 5G operator’s SBA through a rogue network function to get hold of the core network as well as the network slices.
It’s worth noting that the signaling layer is the telecommunication-specific application layer used for exchanging signaling messages between network functions that are located in different slices.
As countermeasures, AdaptiveMobile recommends partitioning the network into different security zones by applying signaling security filters between different slices, the core network, and external partners, and shared and not-shared network functions network, in addition to deploying a signaling layer protection solution to safeguard against data leakage attacks that leverage the missing correlation between layers.
While the current 5G architecture doesn’t support such a protection node, the study suggests enhancing the Service Communication Proxy (SCP) to validate the correctness of message formats, match the information between layers and protocols, and provide load-related functionality to prevent DoS attacks.
“This kind of filtering and validation approach allows division of the network into security zones and safeguarding of the 5G core network,” the researchers said. “Cross-correlation of attack information between those security network functions maximizes the protection against sophisticated attackers and allows better mitigations and faster detection while minimizing false alarms.”