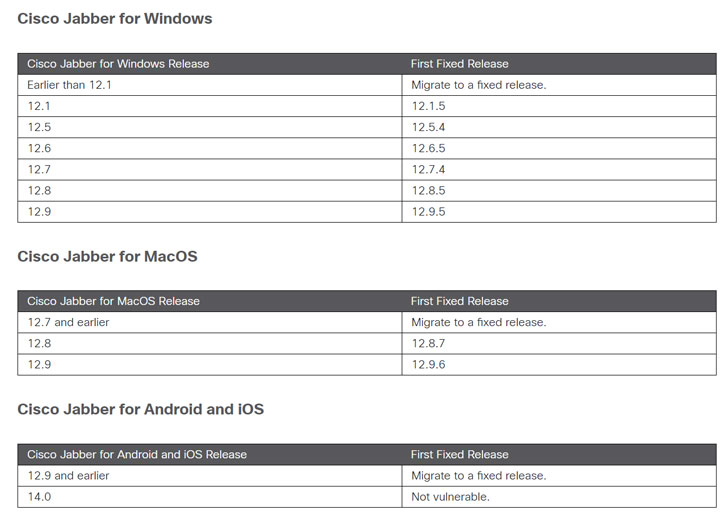
Cisco on Wednesday released software updates to address multiple vulnerabilities affecting its Jabber messaging clients across Windows, macOS, Android, and iOS.
Successful exploitation of the flaws could permit an “attacker to execute arbitrary programs on the underlying operating system with elevated privileges, access sensitive information, intercept protected network traffic, or cause a denial of service (DoS) condition,” the networking major said in an advisory.
The issues concern a total of five security vulnerabilities, three of which (CVE-2021-1411, CVE-2021-1417, and CVE-2021-1418) were reported to the company by Olav Sortland Thoresen of Watchcom, with two others (CVE-2021-1469 and CVE-2021-1471) uncovered during internal security testing.
Cisco notes that the flaws are not dependent on one another, and that exploitation of any one of the vulnerabilities doesn’t hinge on the exploitation of another. But in order to do this, an attacker needs to be authenticated to an Extensible Messaging and Presence Protocol (XMPP) server running the vulnerable software, as well as be able to send XMPP messages.
CVE-2021-1411, which concerns an arbitrary program execution vulnerability in its Windows app, is also the most critical, with a CVSS score of 9.9 out of a maximum of 10. According to Cisco, the flaw is due to improper validation of message content, thus making it possible for an attacker to send specially-crafted XMPP messages to the vulnerable client and execute arbitrary code with the same privileges as that of the user account running the software.
Besides CVE-2021-1411, four other Jabber flaws have also been fixed by Cisco, counting —
- CVE-2021-1469 (Windows) – An issue with improper validation of message content that could result in arbitrary code execution.
- CVE-2021-1417 (Windows) – A failure to validate message content that could be leveraged to leak sensitive information, which can then fuel further attacks.
- CVE-2021-1471 (Windows, macOS, Android, iOS) – A certificate validation vulnerability that could be abused to intercept network requests and even modify connections between the Jabber client and a server
- CVE-2021-1418 (Windows, macOS, Android, iOS) – An issue arising from improper validation of message content that could be exploited by sending crafted XMPP messages to cause a denial-of-service (DoS) condition.
This is far from the first time Norwegian cybersecurity firm Watchcom has uncovered flaws in Jabber clients. In September 2020, Cisco resolved four flaws in its Windows app that could permit an authenticated, remote attacker to execute arbitrary code. But after three of the four vulnerabilities were not “sufficiently mitigated,” the company ended up releasing the second round of patches in December.
In addition to the fix for Jabber, Cisco has also published 37 other advisories that go into detail about security updates for a number of medium and high severity security issues affecting various Cisco products.