Cyber attackers are actively setting their sights on unsecured SAP applications in an attempt to steal information and sabotage critical processes, according to new research.
“Observed exploitation could lead in many cases to full control of the unsecured SAP application, bypassing common security and compliance controls, and enabling attackers to steal sensitive information, perform financial fraud or disrupt mission-critical business processes by deploying ransomware or stopping operations,” cybersecurity firm Onapsis and SAP said in a joint report published today.
The Boston-based company said it detected over 300 successful exploitations out of a total of 1,500 attempts targeting previously known vulnerabilities and insecure configurations specific to SAP systems between mid-2020 to March 2021, with multiple brute-force attempts made by adversaries aimed at high-privilege SAP accounts as well as chaining together several flaws to strike SAP applications.
Applications that have been targeted include, but not limited to enterprise resource planning (ERP), supply chain management (SCM), human capital management (HCM), product lifecycle management (PLM), customer relationship management (CRM), and others.
Troublingly, Onapsis report outlines weaponization of SAP vulnerabilities in less than 72 hours from the release of patches, with new unprotected SAP applications provisioned in cloud environments being discovered and compromised in less than 3 hours.
In one case, a day after SAP issued a patch for CVE-2020-6287 (more below) on July 14, 2020, a proof-of-concept exploit emerged in the wild, which was followed by mass scanning activity on July 16 and the release of a fully-functional public exploit on July 17, 2020.
The attack vectors were no less sophisticated. The adversaries were found to adopt a varied set of techniques, tools, and procedures to gain initial access, escalate privileges, drop web shells for arbitrary command execution, create SAP administrator users with high privileges, and even extract database credentials. The attacks themselves were launched with the help of TOR nodes and distributed virtual private servers (VPS).
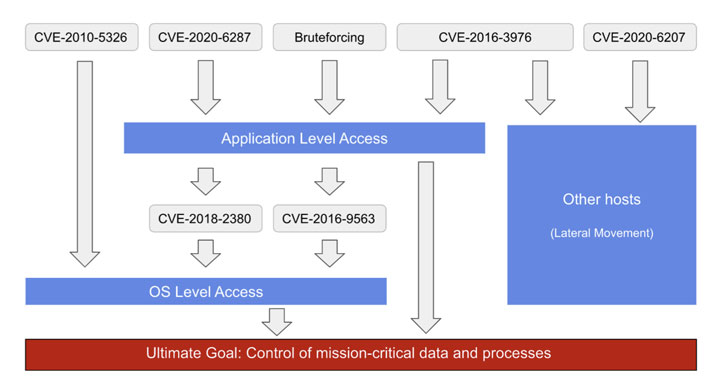
The six flaws exploited by threat actors include —
- CVE-2010-5326 (CVSS score: 10) – Remote code execution flaw in SAP NetWeaver Application Server (AS) Java
- CVE-2016-3976 (CVSS score: 7.5) – Directory traversal vulnerability in SAP NetWeaver AS Java
- CVE-2016-9563 (CVSS score: 6.4) – XML External Entity (XXE) expansion vulnerability in BC-BMT-BPM-DSK component of SAP NetWeaver AS Java
- CVE-2018-2380 (CVSS score: 6.6) – Directory traversal vulnerability in Internet Sales component in SAP CRM
- CVE-2020-6207 (CVSS score: 9.8) – Missing authentication check in SAP Solution Manager
- CVE-2020-6287 (CVSS score: 10) – RECON (aka Remotely Exploitable Code On NetWeaver) flaw in LM Configuration Wizard component
First disclosed in July 2020, successful exploitation of CVE-2020-6287 could give an unauthenticated attacker full access to the affected SAP system, counting the “ability to modify financial records, steal personally identifiable information (PII) from employees, customers and suppliers, corrupt data, delete or modify logs and traces and other actions that put essential business operations, cybersecurity and regulatory compliance at risk.”
Onapsis also said it was able to detect scanning activity for CVE-2020-6207 dating back to October 19, 2020, almost three months before the public release of a fully-working exploit on January 14, 2021, implying that threat actors had knowledge of the exploit prior to the public disclosure.
Furthermore, a separate attack observed on December 9 was found to chain exploits for three of the flaws, namely CVE-2020-6287 for creating an admin user and logging in to the SAP system, CVE-2018-2380 for privilege escalation, and CVE-2016-3976 for access to high-privileged accounts and the database.
“This all happened within 90 minutes,” Onapsis researchers noted.
While no customer breaches have been uncovered, both SAP and Onapsis are urging businesses to perform a compromise assessment of applications, apply relevant patches, and address misconfigurations to prevent unauthorized access.
“The critical findings […] describe attacks on vulnerabilities with patches and secure configuration guidelines available for months and even years,” Onapsis CEO Mariano Nunez said. “Unfortunately, too many organizations still operate with a major governance gap in terms of the cybersecurity and compliance of their mission-critical applications, allowing external and internal threat actors to access, exfiltrate and gain full control of their most sensitive and regulated information and processes.”
“Companies that have not prioritized rapid mitigation for these known risks should consider their systems compromised and take immediate and appropriate action,” Nunez added.