A previously undocumented malware downloader has been spotted in the wild in phishing attacks to deploy credential stealers and other malicious payloads.
Dubbed “Saint Bot,” the malware is said to have first appeared on the scene in January 2021, with indications that it’s under active development.
“Saint Bot is a downloader that appeared quite recently, and slowly is getting momentum. It was seen dropping stealers (i.e. Taurus Stealer) or further loaders (example), yet its design allows [it] to utilize it for distributing any kind of malware,” said Aleksandra “Hasherezade” Doniec, a threat intelligence analyst at Malwarebytes.
“Furthermore, Saint Bot employs a wide variety of techniques which, although not novel, indicate some level of sophistication considering its relatively new appearance.”
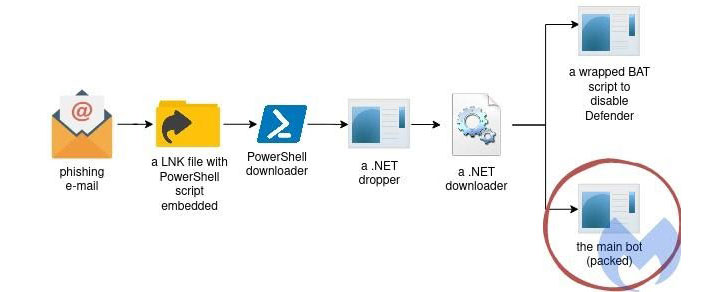
The infection chain analyzed by the cybersecurity firm begins with a phishing email containing an embedded ZIP file (“bitcoin.zip”) that claims to be a bitcoin wallet when, in fact, it’s a PowerShell script under the guise of .LNK shortcut file. This PowerShell script then downloads the next stage malware, a WindowsUpdate.exe executable, which, in turn, drops a second executable (InstallUtil.exe) that takes care of downloading two more executables named def.exe and putty.exe.
While the former is a batch script responsible for disabling Windows Defender, putty.exe contains the malicious payload that eventually connects to a command-and-control (C2) server for further exploitation.
The obfuscation present in each stage of the infection, coupled with the anti-analysis techniques adopted by the malware, allows the malware operators to exploit the devices they were installed on without attracting attention.
Besides performing “self defense checks” to verify the presence of a debugger or a virtual environment, Saint Bot is designed to not execute in Romania and select countries within the Commonwealth of Independent States (CIS), which includes Armenia, Belarus, Kazakhstan, Moldova, Russia, and Ukraine.
The list of commands supported by the malware include —
- downloading and executing other payloads retrieved from the C2 server
- updating the bot malware, and
- uninstalling itself from the compromised machine
While these capabilities may seem very small, the fact that Saint Bot serves as a downloader for other malware makes it dangerous enough.
Interestingly, the payloads are themselves fetched from files hosted on Discord, a tactic that has become increasingly common among threat actors, who are abusing legitimate functions of such platforms for C2 communications, evade security, and deliver malware.
“When files are uploaded and stored within the Discord CDN, they can be accessed using the hardcoded CDN URL by any system, regardless of whether Discord has been installed, simply by browsing to the CDN URL where the content is hosted,” researchers from Cisco Talos disclosed in an analysis earlier this week, thus turning software like Discord and Slack into lucrative targets for hosting malicious content.
“Saint Bot is yet another tiny downloader,” Hasherezade said. “”[It is] not as mature as SmokeLoader, but it is quite new and currently actively developed. The author seems to have some knowledge of malware design, which is visible by the wide range of techniques used. Yet, all the deployed techniques are well-known and pretty standard, [and] not showing much creativity so far.”