Networking equipment major Cisco Systems has said it does not plan to fix a critical security vulnerability affecting some of its Small Business routers, instead urging users to replace the devices.
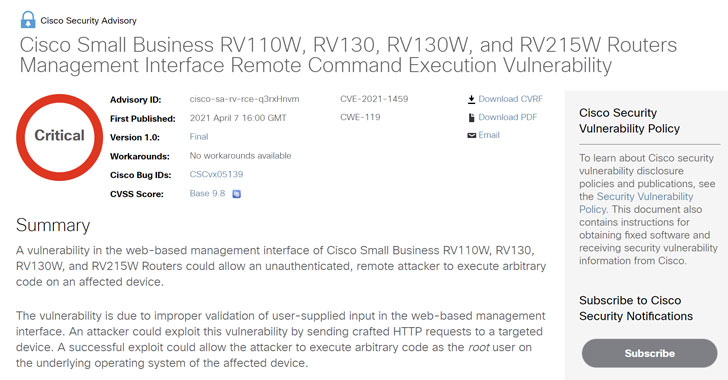
The bug, tracked as CVE-2021-1459, is rated with a CVSS score of 9.8 out of 10, and affects RV110W VPN firewall and Small Business RV130, RV130W, and RV215W routers, allowing an unauthenticated, remote attacker to execute arbitrary code on an affected appliance.
The flaw, which stems from improper validation of user-supplied input in the web-based management interface, could be exploited by a malicious actor to send specially-crafted HTTP requests to the targeted device and achieve remote code execution.
” A successful exploit could allow the attacker to execute arbitrary code as the root user on the underlying operating system of the affected device,” Cisco said in its advisory.
Security researcher Treck Zhou has been credited with reporting the vulnerability. Although the company noted there’s been no evidence of active exploitation attempts in the wild, it doesn’t intend to release a patch or make any workarounds available, citing that the products have reached end-of-life.
“The Cisco Small Business RV110W, RV130, RV130W, and RV215W Routers have entered the end-of-life process,” the firm said. “Customers are encouraged to migrate to the Cisco Small Business RV132W, RV160, or RV160W Routers.”
Separately, Cisco has also released software updates to address multiple vulnerabilities in Cisco SD-WAN vManage Software (CVE-2021-1137, CVE-2021-1479, and CVE-2021-1480) that could permit an unauthenticated, remote attacker to execute arbitrary code or allow an authenticated, local attacker to gain escalated privileges on an affected system.
As a result of a buffer overflow condition, CVE-2021-1479 is rated 9.8 in severity, successful exploitation of which “could allow the attacker to execute arbitrary code on the underlying operating system with root privileges.”