Most mobile app users tend to blindly trust that the apps they download from app stores are safe and secure. But that isn’t always the case.
To demonstrate the pitfalls and identify vulnerabilities on a large scale, cybersecurity and machine intelligence company CloudSEK recently provided a platform called BeVigil where individuals can search and check app security ratings and other security issues before installing an app.
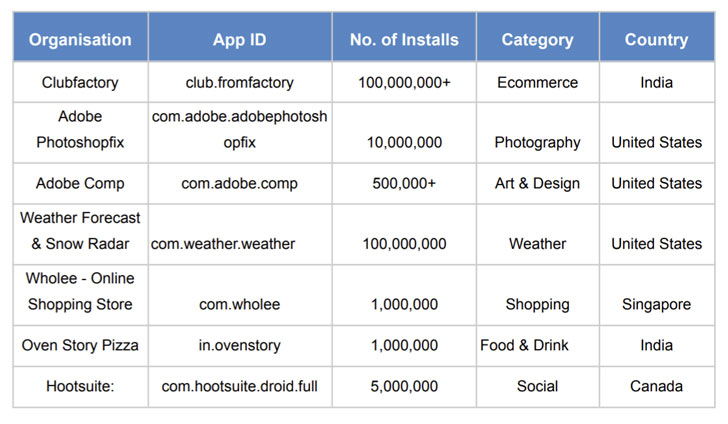
A latest report shared with The Hacker News detailed how the BeVigil search engine identified over 40 apps – with more than a cumulative 100 million downloads – that had hardcoded private Amazon Web Services (AWS) keys embedded within them, putting their internal networks and their users’ data at risk of cyberattacks.
BeVigil finds popular apps leaking AWS keys
The AWS key leakage was spotted in some of the major apps such as Adobe Photoshop Fix, Adobe Comp, Hootsuite, IBM’s Weather Channel, and online shopping services Club Factory and Wholee. The findings are the result of an analysis of over 10,000 apps submitted to CloudSEK’s BeVigil, a mobile app security search engine.
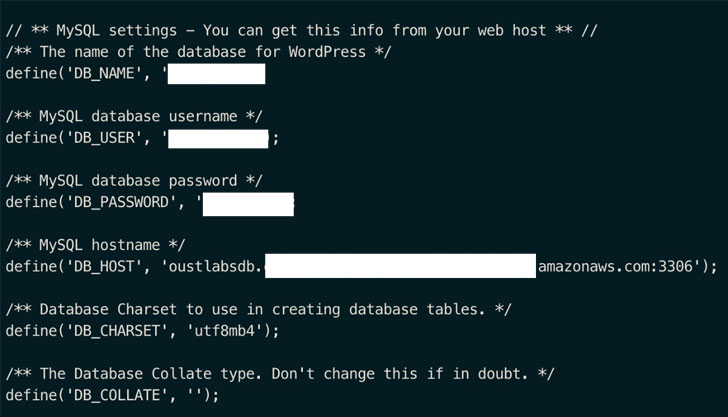
” AWS keys hardcoded in a mobile app source code can be a huge problem, especially if it’s [Identity and Access Management] role has wide scope and permissions,” CloudSEK researchers said. “The possibilities for misuse are endless here, since the attacks can be chained and the attacker can gain further access to the whole infrastructure, even the code base and configurations.”
CloudSEK said it responsibly disclosed these security concerns to AWS and the affected companies independently.
In an app analyzed by the Bengaluru-based cybersecurity firm, the exposed AWS key had access to multiple AWS services, including credentials for the S3 storage service, which in turn opened up access to 88 buckets containing 10,073,444 files and data amounting to 5.5 terabytes.
Also included in the buckets were source code, application backups, user reports, test artifacts, configuration and credential files which could be used to gain deeper access to the app’s infrastructure, including user databases.
Misconfigured AWS instances accessible from the internet have been the cause of many data breaches recently. In October 2019, cybersecurity firm Imperva disclosed that information from an unspecified subset of users of its Cloud Firewall product was accessible online after a botched cloud migration of its customer database that began in 2017.
Last month, India-based online trading and discount brokerage platform Upstox suffered a security incident after a notorious hacking group called ShinyHunters accessed its improperly configured AWS S3 bucket.
“Hardcoded API keys are like locking your house but leaving the key in an envelope labeled ‘Do not open,'” the researchers said. “These keys could easily be discovered by malicious hackers or competitors who could use them to compromise their data and networks.”
What is BeVigil, and how does it work?
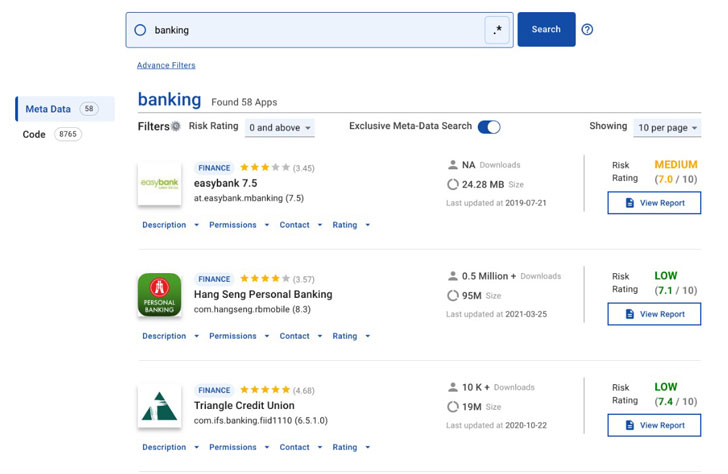
BeVigil is a mobile security search engine that allows researchers to search app metadata, review their code, view security reports and Risk Scores, and even scan new APKs.
Mobile apps have been the target of many recent supply chain attacks. Attackers inject malicious code into SDKs used by app developers. Security teams could rely on BeVigil to identify any malicious apps that use malicious SDKs.
An in-depth investigation of various apps that are on the web can be done by security researchers using metadata search. The scanning reports generated by BeVigil are available to the entire CloudSEK community. To sum it up, it’s a bit like VirusTotal for consumers and security researchers.
What can you search for in BeVigil?
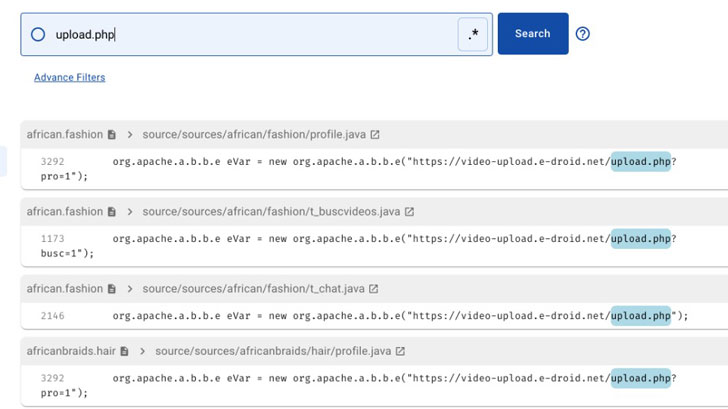
You can search millions of apps for vulnerable code snippets or keywords to learn which apps contain them. With this, researchers can easily analyze quality data, correlate threats, and deal with false positives.
Apart from searching for a specific app by simply typing in the name, one can also find an entire list of apps:
- from an organization,
- above or below a certain security score; e.g., credit apps with security score 7,
- released within a certain time period (select “from” and “to” dates); e.g., identify credit apps released in 2021,
- from 48 different categories such as finance, education, tools, health & fitness, etc.,
- from a specific developer by searching with the developer email address,
- developed in a specific country by searching; for example, identify banking apps from Germany,
- developed in a specific location by searching with the pin code or developer email address,
- that record audio in the background,
- that record location in the background,
- that can access the camera device,
- that can access specific permission on your device,
- with a specific target SDK version
Besides these, one can also use Regexes to find apps with security vulnerabilities by looking for code patterns.