Researchers on Tuesday disclosed a novel malware that uses a variety of tricks to stay under the radar and evade detection, while stealthily capable of executing arbitrary commands on infected systems.
Called ‘Pingback,’ the Windows malware leverages Internet Control Message Protocol (ICMP) tunneling for covert bot communications, allowing the adversary to utilize ICMP packets to piggyback attack code, according to an analysis published today by Trustwave.
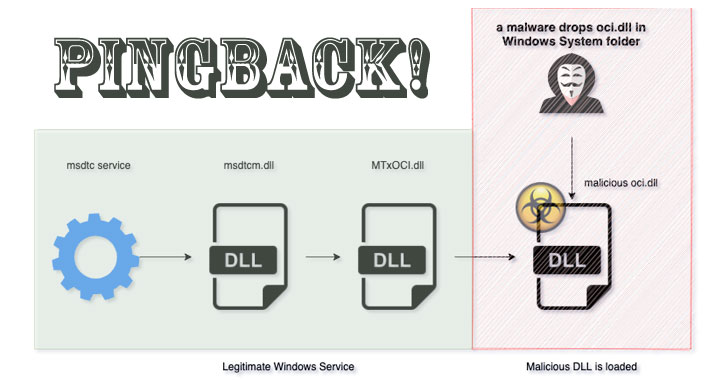
Pingback (“oci.dll“) achieves this by getting loaded through a legitimate service called MSDTC (Microsoft Distributed Transaction Coordinator) — a component responsible for handling database operations that are distributed over multiple machines — by taking advantage of a method called DLL search order hijacking, which involves using a genuine application to preload a malicious DLL file.
Naming the malware as one of the plugins required for supporting Oracle ODBC interface in MSDTC is key to the attack, the researchers noted. While MSDTC isn’t configured to run automatically on startup, a VirusTotal sample submitted in July 2020 was found to install the DLL file into the Windows System directory and start the MSDTC service to achieve persistence, raising the possibility that a separate executable is crucial to installing the malware.
Upon successful execution, Pingback resorts to using the ICMP protocol for its main communication. ICMP is a network layer protocol mainly used for sending error messages and operational information, say, a failure alert when another host becomes unreachable.
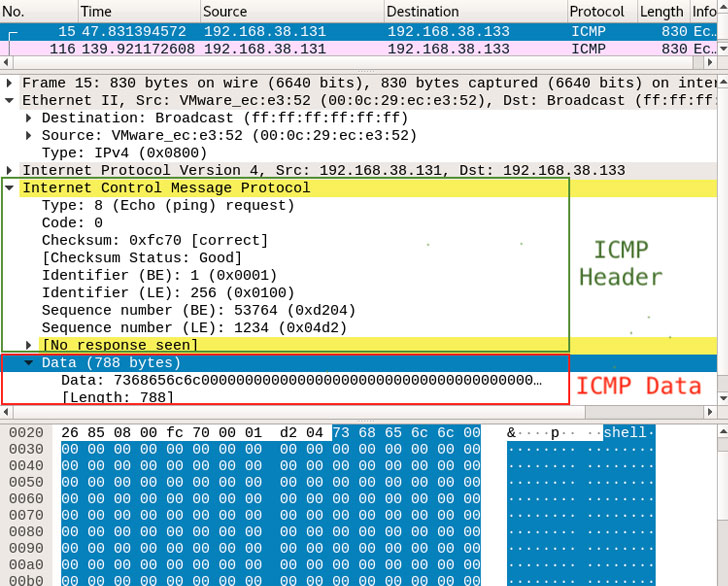
Specifically, Pingback takes advantage of an Echo request (ICMP message type 8), with the message sequence numbers 1234, 1235, and 1236 denoting the type of information contained in the packet — 1234 being a command or data, and 1235 and 1236 being the acknowledgment for receipt of data on the other end. Some of the commands supported by the malware include the capability to run arbitrary shell commands, download and upload files from and to the attacker’s host, and execute malicious commands on the infected machine.
An investigation into the malware’s initial intrusion route is ongoing.
“ICMP tunneling is not new, but this particular sample piqued our interest as a real-world example of malware using this technique to evade detection,” the researchers said. “ICMP is useful for diagnostics and performance of IP connections, [but] it can also be misused by malicious actors to scan and map a target’s network environment. While we are not suggesting that ICMP should be disabled, we do suggest putting in place monitoring to help detect such covert communications over ICMP.”