An unknown threat actor with the capabilities to evolve and tailor its toolset to target environments infiltrated high-profile organizations in Asia and Africa with an evasive Windows rootkit since at least 2018.
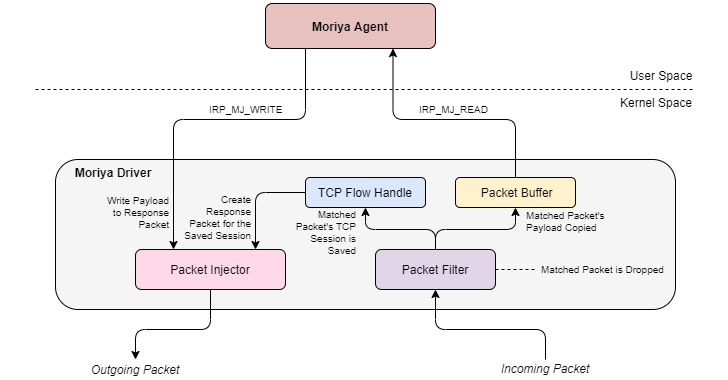
Called ‘Moriya,’ the malware is a “passive backdoor which allows attackers to inspect all incoming traffic to the infected machine, filter out packets that are marked as designated for the malware and respond to them,” said Kaspersky researchers Mark Lechtik and Giampaolo Dedola in a Thursday deep-dive.
The Russian cybersecurity firm termed the ongoing espionage campaign ‘TunnelSnake.’ Based on telemetry analysis, less than 10 victims around the world have been targeted to date, with the most prominent victims being two large diplomatic entities in Southeast Asia and Africa. All the other victims were located in South Asia.
The first reports of Moriya emerged last November when Kaspersky said it discovered the stealthy implant in the networks of regional inter-governmental organizations in Asia and Africa. Malicious activity associated with the operation is said to have dated back to November 2019, with the rootkit persisting in the victim networks for several months following the initial infection.
“This tool was used to control public facing servers in those organizations by establishing a covert channel with a C2 server and passing shell commands and their outputs to the C2,” the company said in its APT trends report for Q3 2020. “This capability is facilitated using a Windows kernel mode driver.”
Rootkits are particularly dangerous as they allow attackers to gain high privileges in the system, enabling them to intercept core input/output operations conducted by the underlying operating system and better blend with the landscape, thus making it difficult to trace the attacker’s digital footprints.
Microsoft, for its part, has implemented several protections into Windows over the years to prevent successful deployment and execution of rootkits, which makes Moriya all the more noteworthy.
Bulk of the toolset, apart from the backdoor, consists of both proprietary and well-known pieces of malware such as China Chopper web shell, BOUNCER, Earthworm, and Termite that have been previously used by Chinese-speaking threat actors, giving an insight into the attacker’s origins. The tactics, techniques, and procedures (TTPs) used in the attacks also show that the targeted entities fit the victimology pattern associated with Chinese-speaking adversaries.
The revelations come as advanced persistent threats (APTs) continue to ramp up highly-targeted data-stealing missions, while simultaneously going to great lengths to stay under the radar for as long as possible, rebuild their malware arsenal, making them more tailored, complex, and harder to detect.
“The TunnelSnake campaign demonstrates the activity of a sophisticated actor that invests significant resources in designing an evasive toolset and infiltrating networks of high-profile organizations,” Lechtik and Dedola said. “By leveraging Windows drivers, covert communications channels and proprietary malware, the group behind it maintains a considerable level of stealth.”