Cybersecurity researchers on Monday disclosed a new Android trojan that hijacks users’ credentials and SMS messages to facilitate fraudulent activities against banks in Spain, Germany, Italy, Belgium, and the Netherlands.
Called “TeaBot” (or Anatsa), the malware is said to be in its early stages of development, with malicious attacks targeting financial apps commencing in late March 2021, followed by a rash of infections in the first week of May against Belgium and the Netherlands banks. The first signs of TeaBot activity occurred in January.
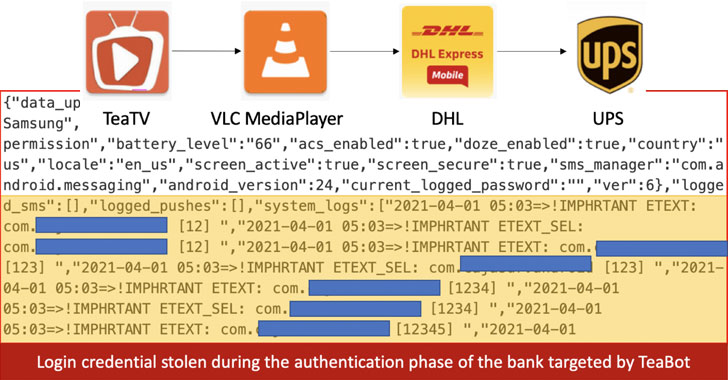
“The main goal of TeaBot is stealing victim’s credentials and SMS messages for enabling frauds scenarios against a predefined list of banks,” Italian cybersecurity, and online fraud prevention firm Cleafy said in a Monday write-up. “Once TeaBot is successfully installed in the victim’s device, attackers can obtain a live streaming of the device screen (on demand) and also interact with it via Accessibility Services.”
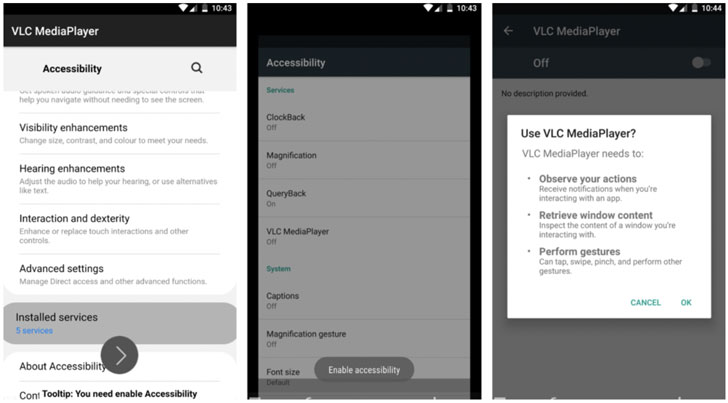
The rogue Android application, which masquerades as media and package delivery services like TeaTV, VLC Media Player, DHL, and UPS, acts as a dropper that not only loads a second-stage payload but also forces the victim into granting it accessibility service permissions.
In the last link of the attack chain, TeaBot exploits the access to achieve real-time interaction with the compromised device, enabling the adversary to record keystrokes, in addition to taking screenshots and injecting malicious overlays on top of login screens of banking apps to steal credentials and credit card information.
Other capabilities of TeaBot include disabling Google Play Protect, intercepting SMS messages, and accessing Google Authenticator 2FA codes. The collected information is then exfiltrated every 10 seconds to a remote server controlled by the attacker.
Android malware abusing accessibility services as a stepping stone for perpetrating data theft has witnessed a surge in recent months. Since the start of the year, at least three different malware families — Oscorp, BRATA, and FluBot — have banked on the feature to gain total control of the infected devices.
Interestingly, the fact that TeaBot employs the same decoy as that of Flubot by posing as innocuous shipment apps could be an attempt to mislead attribution and stay under the radar. The heightened FluBot infections prompted Germany and the U.K. to issue alerts last month warning of ongoing attacks via fraudulent SMS messages that trick users into installing “spyware that steals passwords and other sensitive data.”