Microsoft on Thursday warned of a “massive email campaign” that’s pushing a Java-based STRRAT malware to steal confidential data from infected systems while disguising itself as a ransomware infection.
“This RAT is infamous for its ransomware-like behavior of appending the file name extension .crimson to files without actually encrypting them,” the Microsoft Security Intelligence team said in a series of tweets.
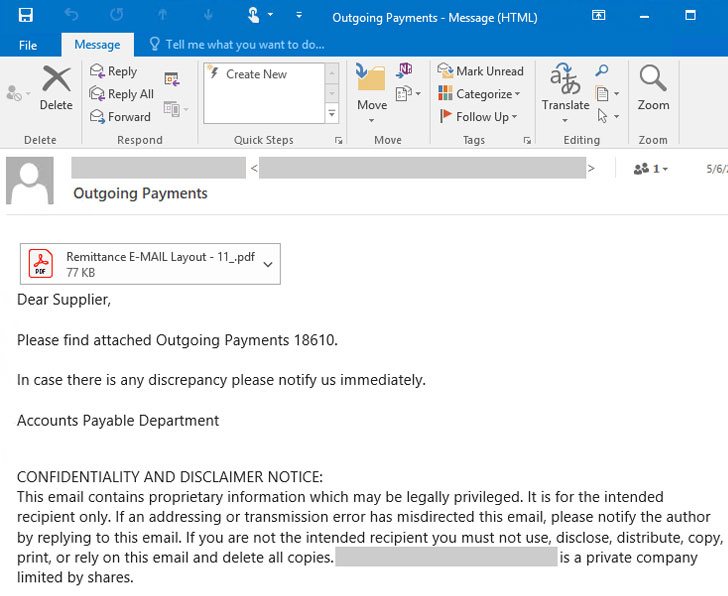
The new wave of attacks, which the company spotted last week, commences with spam emails sent from compromised email accounts with “Outgoing Payments” in the subject line, luring the recipients into opening malicious PDF documents that claim to be remittances, but in reality, connect to a rogue domain to download the STRRAT malware.
Besides establishing connections to a command-and-control server during execution, the malware comes with a range of features that allow it to collect browser passwords, log keystrokes, and run remote commands and PowerShell scripts.
STRRAT first emerged in the threat landscape in June 2020, with German cybersecurity firm G Data observing the Windows malware (version 1.2) in phishing emails containing malicious Jar (or Java Archive) attachments.
“The RAT has a focus on stealing credentials of browsers and email clients, and passwords via keylogging,” G Data malware analyst Karsten Hahn detailed. “It supports the following browsers and email clients: Firefox, Internet Explorer, Chrome, Foxmail, Outlook, Thunderbird.”
Its ransomware capabilities are at best rudimentary in that the “encryption” stage only renames files by suffixing the “.crimson” extension. “If the extension is removed, the files can be opened as usual,” Kahn added.
Microsoft also notes that version 1.5 is more obfuscated and modular than previous versions, suggesting that the attackers behind the operation are actively working to improvise their toolset. But the fact that the bogus encryption behavior remains unchanged signals that the group may be aiming to make quick money off unsuspecting users by means of extortion.
The indicators of compromise (IoCs) associated with the campaign can be accessed via GitHub here.