State-sponsored hackers affiliated with North Korea have been behind a slew of attacks on cryptocurrency exchanges over the past three years, new evidence has revealed.
Attributing the attack with “medium-high” likelihood to the Lazarus Group (aka APT38 or Hidden Cobra), researchers from Israeli cybersecurity firm ClearSky said the campaign, dubbed “CryptoCore,” targeted crypto exchanges in Israel, Japan, Europe, and the U.S., resulting in the theft of millions of dollars worth of virtual currencies.
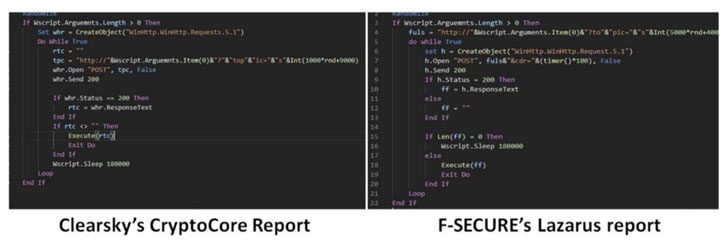
The findings are a consequence of piecing together artifacts from a series of isolated but similar reports detailed by F-Secure, Japanese CERT JPCERT/CC, and NTT Security over the past few months.
Since emerging on the scene in 2009, Hidden Cobra actors have used their offensive cyber capabilities to carry out espionage and cyber cryptocurrency heists against businesses and critical infrastructure. The adversary’s targeting aligns with North Korean economic and geopolitical interests, which are primarily motivated by financial gain as a means to circumvent international sanctions. In recent years, Lazarus Group has further expanded its attacks to target the defense and aerospace industries.
CryptoCore, also called CryptoMimic, Dangerous Password, CageyChameleon, and Leery Turtle, is no different from other Lazarus Group operations in that it’s primarily focused on the theft of cryptocurrency wallets.
Believed to have commenced in 2018, the campaign’s modus operandi involves leveraging spear-phishing as an intrusion route to get hold of the victim’s password manager account, using it to plunder the wallet keys and transfer the currencies to an attacker-owned wallet.
The group is said to have stolen an estimated $200 million, according to a ClearSky report published in June 2020, which linked CryptoCore to five victims located in the U.S., Japan, and the Middle East. In connecting the dots, the latest research shows that the operations have been more widespread than previously documented, while simultaneously evolving several parts of its attack vector.
A comparison of the indicators of compromise (IoCs) from the four public disclosures not only found enough behavioral and code-level overlaps, but has also raised the possibility that each of the reports touched upon different aspects of what appears to be a large-scale attack.
In addition, ClearSky said it reaffirmed the attribution by comparing the malware deployed in the CryptoCore campaign to other Lazarus campaigns and found strong similarities.
“This group has successfully hacked into numerous companies and organizations around the world for many years,” ClearSky researchers said. “Until recently this group was not known to attack Israeli targets.”