The Uyghur community located in China and Pakistan has been the subject of an ongoing espionage campaign aiming to trick the targets into downloading a Windows backdoor to amass sensitive information from their systems.
“Considerable effort was put into disguising the payloads, whether by creating delivery documents that appear to be originating from the United Nations using up to date related themes, or by setting up websites for non-existing organizations claiming to fund charity groups,” according to joint research published by Check Point Research and Kaspersky today.
The Uyghurs are a Turkic ethnic minority group originating from Central and East Asia and are recognized as native to the Xinjiang Uyghur Autonomous Region in Northwest China. At least since 2015, government authorities have placed the region under tight surveillance, putting hundreds of thousands into prisons and internment camps that the government calls “Vocational Education and Training Centers.”
Over the years, the community has also been at the receiving end of a series of sustained cyberattacks that have leveraged exploit chains and watering holes to install spyware designed to harvest and exfiltrate sensitive data from email and messaging apps as well as plunder photos and login credentials.
Earlier this March, Facebook disclosed that it disrupted a network of bad actors using its platform to target the Uyghur community and lure them into downloading malicious software that would allow surveillance of their devices, attributing the “persistent operation” to a China-based threat actor known as Evil Eye.
The latest cyber offensive follows a similar modus operandi in that the attacks involve sending UN-themed decoy documents (“UgyhurApplicationList.docx”) to the targets under the pretext of discussing human rights violations. The goal of the phishing message is to lure the recipients into installing a backdoor on the Windows machines.
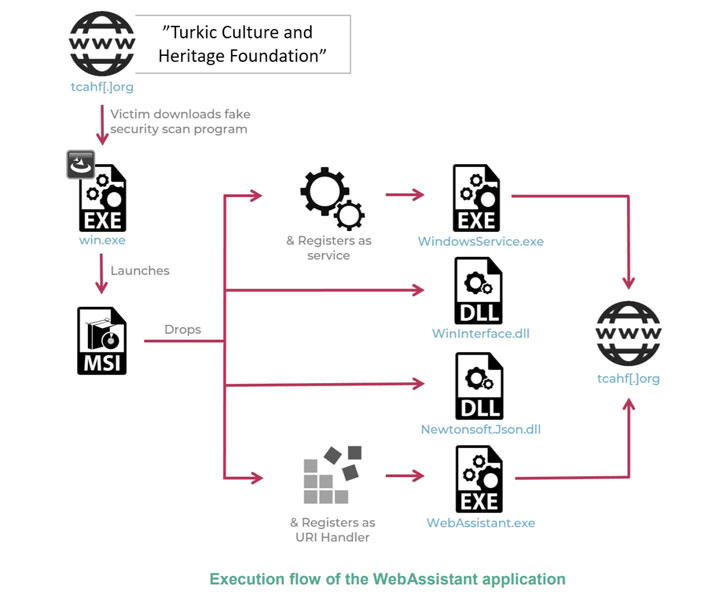
In an alternative infection vector observed by the researchers, a fake human rights foundation called the “Turkic Culture and Heritage Foundation” (“tcahf[.]org”) — with its content copied from George Soros-founded Open Society Foundations — was used as a bait to download a .NET backdoor that purports to be a security scanner, only to connect to a remote server and transmit the gathered data, which includes system metadata and a list of installed apps and running processes.
“The malicious functionality of the TCAHF website is well disguised and only appears when the victim attempts to apply for a grant,” the researchers said. “The website then claims it must make sure the operating system is safe before entering sensitive information for the transaction, and therefore asks the victims to download a program to scan their environments.”
At least two different versions of the Windows implants have been detected to date, one called “WebAssistant” that was available for download from the rogue website in May 2020 and a second variant dubbed “TcahfUpdate” that was available in October 2020.
The two cybersecurity firms did not attribute the attacks to a known threat group but pinned the intrusions on a Chinese-speaking adversary with low to medium confidence based on overlaps in the VBA code embedded in the Word document. Only a handful of victims in China and Pakistan have been identified so far, based on telemetry data compiled during the analysis.
Unsurprisingly, the attackers behind the campaign continue to remain active and evolve its infrastructure, with the group registering two new domains in 2021, both of which redirect to the website of a Malaysian government body called the “Terengganu Islamic Foundation,” suggesting the threat actor may have set its sights on targets in Malaysia and Turkey.
“We believe that these cyber-attacks are motivated by espionage, with the end-game of the operation being the installation of a backdoor into the computers of high-profile targets in the Uyghur community,” said Lotem Finkelsteen, Check Point’s head of threat intelligence. “The attacks are designed to fingerprint infected devices … [and] from what we can tell, these attacks are ongoing, and new infrastructure is being created for what looks like future attacks.”