Cybersecurity researchers on Tuesday disclosed “distinctive” tactics, techniques, and procedures (TTPs) adopted by operators of Hades ransomware that set it apart from the rest of the pack, attributing it to a financially motivated threat group called GOLD WINTER.
“In many ways, the GOLD WINTER threat group is a typical post-intrusion ransomware threat group that pursues high-value targets to maximize how much money it can extort from its victims,” researchers from SecureWorks Counter Threat Unit (CTU) said in an analysis shared with The Hacker News. “However, GOLD WINTER’s operations have quirks that distinguish it from other groups.”
The findings come from a study of incident response efforts the Atlanta-based cybersecurity firm engaged in the first quarter of 2021.
Since first emerging in the threat landscape in December 2020, Hades has been classified as INDRIK SPIDER’s successor to WastedLocker ransomware with “additional code obfuscation and minor feature changes,” per Crowdstrike. INDRIK SPIDER, also known as GOLD DRAKE and Evil Corp, is a sophisticated eCrime group infamous for operating a banking trojan called Dridex as well as distributing BitPaymer ransomware between 2017 and 2020.
The WastedLocker-derived ransomware strain has been found to have impacted at least three victims as of late March 2021, according to research by Accenture’s Cyber Investigation and Forensic Response (CIFR) and Cyber Threat Intelligence (ACTI) teams, including a U.S. transportation and logistics organization, a U.S. consumer products organization, and a global manufacturing organization. Trucking giant Forward Air was revealed to be a target back in December 2020.
Then a subsequent analysis published by Awake Security raised the possibility that an advanced threat actor may be operating under the guise of Hades, citing a Hafnium domain that was identified as an indicator of compromise within the timeline of the Hades attack. Hafnium is the name assigned by Microsoft to a Chinese nation-state actor that the company has said is behind the ProxyLogon attacks on vulnerable Exchange Servers earlier this year.
Stating that the threat group uses TTPs not associated with other ransomware operators, Secureworks said the absence of Hades from underground forums and marketplaces could mean that Hades is operated as private ransomware rather than ransomware-as-a-service (RaaS).
GOLD WINTER targets virtual private networks and remote desktop protocols to gain an initial foothold and maintain access to victim environments, using it to achieve persistence via tools such as Cobalt Strike. In one instance, the adversary disguised the Cobalt Strike executable as a CorelDRAW graphics editor application to mask the true nature of the file, the researchers said.
In a second case, Hades was found to leverage SocGholish malware — usually associated with the GOLD DRAKE group — as an initial access vector. SocGholish refers to a drive-by attack in which a user is tricked into visiting an infected website using social engineering themes that impersonate browser updates to trigger a malicious download without user intervention.
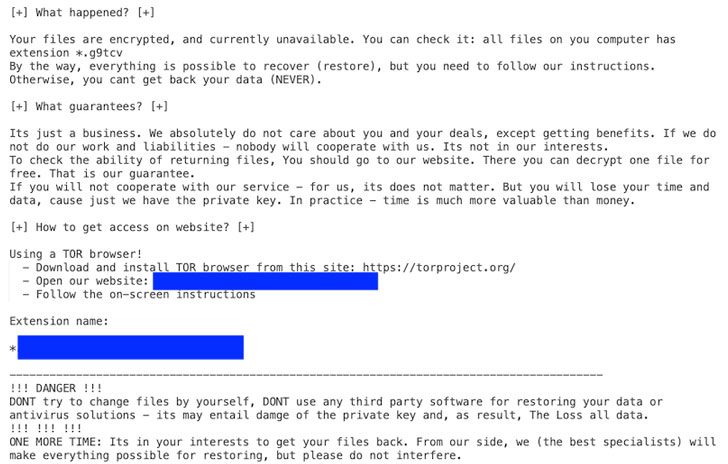
Interestingly, in what appears to be an attempt to mislead attribution or “pay homage to admired ransomware families,” Hades has exhibited a pattern of duplicating ransom notes from other rival groups like REvil and Conti.
Another novel technique involves the use of Tox instant messaging service for communications, not to mention the use of Tor-based websites tailored to each victim as opposed to utilizing a centralized leak site to expose data stolen from its victims. “Each website includes a victim-specific Tox chat ID for communications,” the researchers said.
“Ransomware groups are typically opportunistic: they target any organization that could be susceptible to extortion and will likely pay the ransom,” the researchers noted. “However, GOLD WINTER’s attacks on large North America-based manufacturers indicates that the group is a ‘big game hunter’ that specifically seeks high-value targets.”