Cybersecurity researchers have disclosed a critical unpatched vulnerability affecting Pling-based free and open-source software (FOSS) marketplaces for Linux platform that could be potentially abused to stage supply chain attacks and achieve remote code execution (RCE).
“Linux marketplaces that are based on the Pling platform are vulnerable to a wormable [cross-site scripting] with potential for a supply chain attack,” Positive Security co-founder Fabian Bräunlein said in a technical write-up published today. “The native PlingStore application is affected by an RCE vulnerability, which can be triggered from any website while the app is running.”
The Pling-based app stores impacted by the flaw include —
- appimagehub.com
- store.kde.org
- gnome-look.org
- xfce-look.org
- pling.com
PlingStore allows users to search and install Linux software, themes, icons, and other add-ons that may not be available for download through the distribution’s software center.
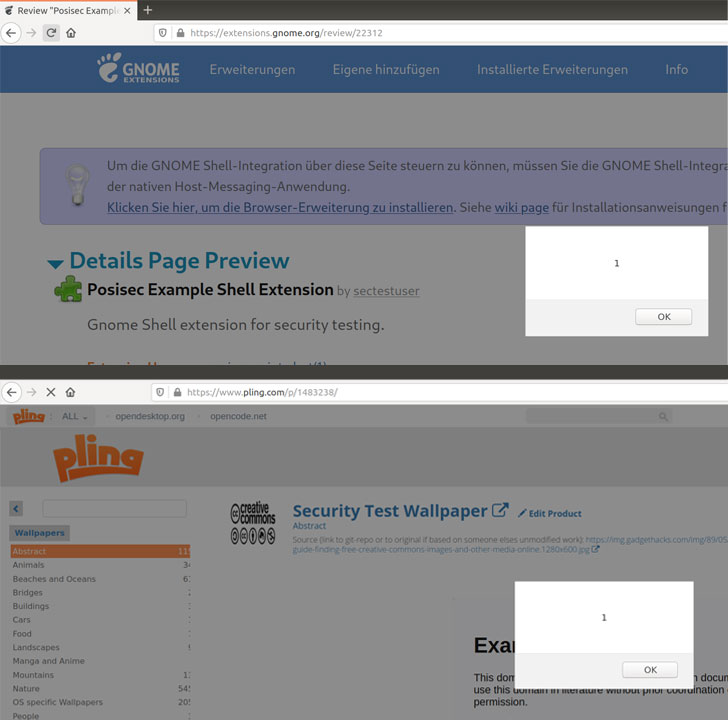
The vulnerability stems from the manner the store’s product listings page parses HTML or embedded media fields, thereby potentially allowing an attacker to inject malicious JavaScript code that could result in arbitrary code execution.
“This stored XSS could be used to modify active listings, or post new listings on the Pling store in the context of other users, resulting in a wormable XSS,” Bräunlein said.
More troublingly, this could allow for a supply-chain attack XSS worm wherein a JavaScript payload could be exploited by an adversary to upload trojanized versions of software and tweak the metadata of a victim’s listing to include and propagate the attack code.
With the PlingStore app acting as a single digital storefront for all the aforementioned app stores, Positive Security noted that the XSS exploit can be triggered from within the app that, when coupled with a sandbox bypass, could lead to remote code execution.
“As the application can install other applications, it has another built-in mechanism to execute code on the [operating system] level,” Bräunlein explained. “As it turns out, that mechanism can be exploited by any website to run arbitrary native code while the PlingStore app is open in the background.”
Put differently, when a user visits a malicious website via the browser, the XSS is triggered inside the Pling app while it’s running in the background. Not only can the JavaScript code in the website establish a connection to the local WebSocket server that’s used to listen to messages from the app, it also uses it to send messages to execute arbitrary native code by downloading and executing an .AppImage package file.
What’s more, a similar XSS flaw uncovered in the GNOME Shell Extensions marketplace could be leveraged to target the victim’s computer by issuing malicious commands to the Gnome Shell Integration browser extension and even backdoor published extensions.
The Berlin-based cybersecurity firm noted that the flaws were reported to the respective project maintainers on Feb. 24, with KDE Project and GNOME Security issuing patches for the flaws following disclosure. In light of the fact that the RCE flaw associated with the PlingStore remains unaddressed as yet, it’s recommended not to run the Electron application until a fix is in place.
The report comes less than a month after severe security weaknesses were uncovered in several popular Visual Studio Code extensions that could enable attackers to compromise local machines as well as build and deployment systems through a developer’s integrated development environment, ultimately paving the way for supply chain attacks.
“[The flaws] demonstrate the additional risk associated with such marketplaces,” Bräunlein said. “In this environment, even relatively small vulnerabilities (e.g. a missing origin check) can lead to severe consequences (drive-by RCE from any browser with the vulnerable application running in background). Developers of such applications must put in a high level of scrutiny to ensure their security.”