Cybersecurity researchers on Thursday took the wraps off a new, ongoing espionage campaign targeting corporate networks in Spanish-speaking countries, specifically Venezuela, to spy on its victims.
Dubbed “Bandidos” by ESET owing to the use of an upgraded variant of Bandook malware, the primary targets of the threat actor are corporate networks in the South American country spanning across manufacturing, construction, healthcare, software services, and retail sectors.
Written in both Delphi and C++, Bandook has a history of being sold as a commercial remote access trojan (RAT) dating all the way back to 2005. Since then, numerous variants have emerged on the threat landscape and put to use in different surveillance campaigns in 2015 and 2017, allegedly by a cyber-mercenary group known as Dark Caracal on behalf of government interests in Kazakhstan and Lebanon.
In a continuing resurgence of the Bandook Trojan, Check Point last year disclosed three new samples — one of which supported 120 commands — that were utilized by the same adversary to hit government, financial, energy, food industry, healthcare, education, IT, and legal institutions located in Chile, Cyprus, Germany, Indonesia, Italy, Singapore, Switzerland, Turkey, and the U.S.
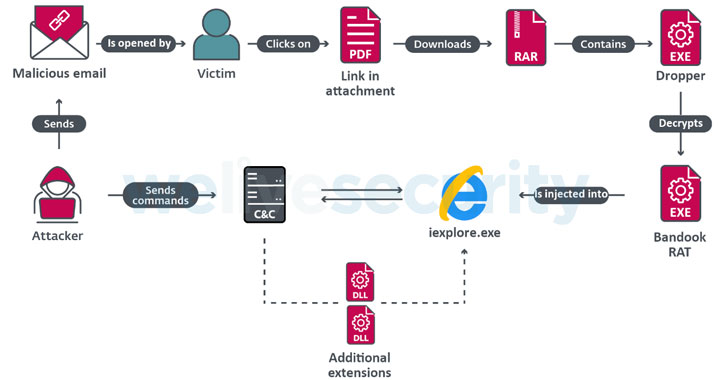
The latest attack chain commences with prospective victims receiving malicious emails with a PDF attachment, which contains a shortened URL to download a compressed archive hosted on Google Cloud, SpiderOak, or pCloud and the password to extract it. Extracting the archive reveals a malware dropper that decodes and injects Bandook into an Internet Explorer process.
Interestingly, the latest variant of Bandook analyzed by ESET contains 132 commands, up from the 120 commands reported by Check Point, implying that the criminal group behind the malware are advancing their malicious tools with improved capabilities and striking power.
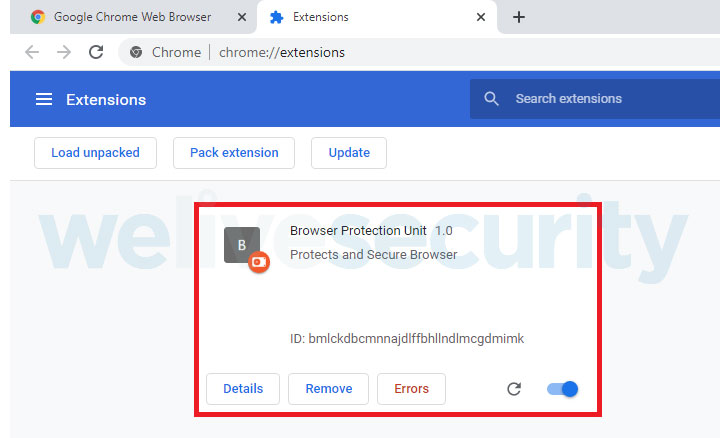
“Especially interesting is the ChromeInject functionality,” said ESET researcher Fernando Tavella. “When the communication with the attacker’s command and control server is established, the payload downloads a DLL file, which has an exported method that creates a malicious Chrome extension. The malicious extension tries to retrieve any credentials that the victim submits to a URL. These credentials are stored in Chrome’s local storage.”
Some of the main commands that the payload is capable of processing include listing directory contents, manipulating files, taking screenshots, controlling the cursor on the victim’s machine, installing malicious DLLs, terminating running processes, downloading files from a specific URL, exfiltrating the results of the operations to a remote server, and even uninstalling itself from the infected machines.
If anything, the development is yet another sign that adversaries can still leverage old crimeware solutions to facilitate attacks.
“[Bandook’s] involvement in different espionage campaigns […] shows us that it is still a relevant tool for cybercriminals,” the researchers opined. “Also, if we consider the modifications made to the malware over the years, it shows us the interest of cybercriminals to keep using this piece of malware in malicious campaigns, making it more sophisticated and more difficult to detect.”