REvil, the infamous ransomware cartel behind some of the biggest cyberattacks targeting JBS and Kaseya, has mysteriously disappeared from the dark web, leading to speculations that the criminal enterprise may have been taken down.
Multiple darknet and clearnet sites maintained by the Russia-linked cybercrime syndicate, including the data leak, extortion, and payment portals, remained inaccessible, displaying an error message “Onionsite not found.”
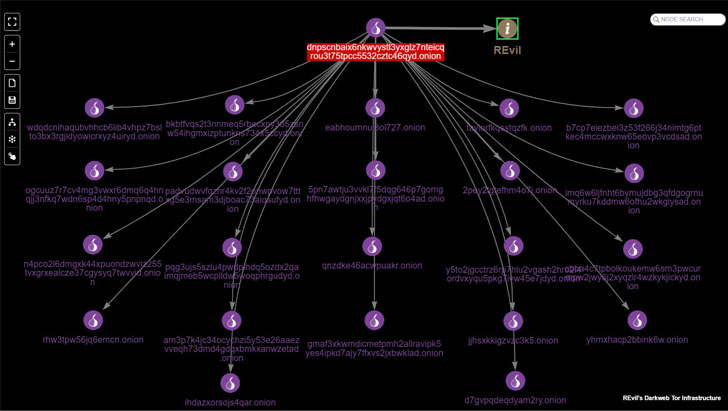
The group’s Tor network infrastructure on the dark web consists of one data leak blog site and 22 data hosting sites. It’s not immediately clear what prompted the infrastructure to be knocked offline.
REvil is one of the most prolific ransomware-as-a-service (RaaS) groups that first appeared on the threat landscape in April 2019. It’s an evolution of the GandCrab ransomware, which hit the underground markets in early 2018.
“If REvil has been permanently disrupted, it’ll mark the end of a group which has been responsible for >360 attacks on the U.S. public and private sectors this year alone,” Emsisoft’s Brett Callow tweeted.
The sudden development comes close on the heels of a wide-scale supply chain ransomware attack aimed at technology services provider Kaseya, for which REvil (aka Sodinokibi) took responsibility for and demanded a $70 million ransom to unlock access to encrypted systems in exchange for a universal decryption key that would unlock all victims data.
The disastrous attack saw the ransomware gang encrypting approximately 60 managed service providers (MSPs) and over 1,500 downstream businesses using a zero-day vulnerability in the Kaseya VSA remote management software. In late May, REvil also masterminded the attack on the world’s largest meat producer JBS, which ended up paying $11 million to the extortionists to recover from the incident.
The outage also coincides with U.S. President Joe Biden’s phone call with Russian President Vladimir Putin last week, pressing the latter to take steps to disrupt ransomware groups operating in the country, while warning of retaliatory action to defend critical infrastructure.
“The situation is still unfolding, but evidence suggests REvil has suffered a planned, concurrent takedown of their infrastructure, either by the operators themselves or via industry or law enforcement action,” FireEye Mandiant’s John Hultquist told CNBC.
It appears that REvil’s Happy Blog was taken offline around 1 AM EST on Tuesday, with vx-underground noting that the group’s public-facing representative, Unknown, has not posted on popular hacking forums such as Exploit and XSS since July 8.
Subsequently, a representative for LockBit ransomware posted to the XSS Russian-speaking hacking forum that REvil’s attack infrastructure received a government legal request, causing the servers to be dismantled. “REvil is banned from XSS,” vx-underground later added.
It’s not uncommon for ransomware groups to go under the ground after highly publicized incidents. After the DarkSide gang targeted Colonial Pipeline in May, the operators announced plans to wind up its RaaS affiliate program for good, claiming that its servers had been seized by an unknown law enforcement agency, raising questions as to whether the group actually retired, or rebranded under a new name.
This theory was eventually validated when the U.S. Department of Justice revealed last month that it was able to recover most of the money paid by Colonial Pipeline to the DarkSide group through an analysis of the bitcoin trails.
REvil’s unexplained shutdown, in a similar fashion, may as well be a case of planned retirement, or a temporary setback, forcing it to seemingly disband only to eventually reassemble under a new identity so as to attract less attention, or may have been the consequence of increased international scrutiny in the wake of a global ransomware crisis.
If it indeed turns out that the group has permanently shuttered operations, the move is bound to leave the group’s targets in the lurch, with no viable means to negotiate ransoms and get hold of the decryption keys necessary to regain control of their systems, thus permanently locking them out of their data.
“I don’t know what this means, but regardless, I’m happy!” tweeted Katie Nickels, director of intelligence at Red Canary. “If it’s a government takedown – awesome, they’re taking action. If the actors voluntarily went quiet – excellent, maybe they’re scared.”