An unidentified threat actor has been exploiting a now-patched zero-day flaw in Internet Explorer browser to deliver a fully-featured VBA-based remote access trojan (RAT) capable of accessing files stored in compromised Windows systems, and downloading and executing malicious payloads as part of an “unusual” campaign.
The backdoor is distributed via a decoy document named “Manifest.docx” that loads the exploit code for the vulnerability from an embedded template, which, in turn, executes shellcode to deploy the RAT, according to cybersecurity firm Malwarebytes, which spotted the suspicious Word file on July 21, 2021.
The malware-laced document claims to be a “Manifesto of the inhabitants of Crimea” calling on the citizens to oppose Russian President Vladimir Putin and “create a unified platform called ‘People’s Resistance.'”
The Internet Explorer flaw, tracked as CVE-2021-26411, is notable for the fact that it was abused by the North Korea-backed Lazarus Group to target security researchers working on vulnerability research and development.
Earlier this February, South Korean cybersecurity firm ENKI revealed the state-aligned hacking collective had made an unsuccessful attempt at targeting its security researchers with malicious MHTML files that, when opened, downloaded two payloads from a remote server, one of which contained a zero-day against Internet Explorer. Microsoft addressed the issue as part of its Patch Tuesday updates for March.
The Internet Explorer exploit is one of the two ways that’s used to deploy the RAT, with the other method relying on a social engineering component that involves downloading and executing a remote macro-weaponized template containing the implant. Regardless of the infection chain, the use of double attack vectors is likely an attempt to increase the likelihood of finding a path into the targeted machines.
“While both techniques rely on template injection to drop a full-featured remote access trojan, the IE exploit (CVE-2021-26411) previously used by the Lazarus APT is an unusual discovery,” Malwarebytes researcher Hossein Jazi said in a report shared with The Hacker News. “The attackers may have wanted to combine social engineering and exploit to maximize their chances of infecting targets.”
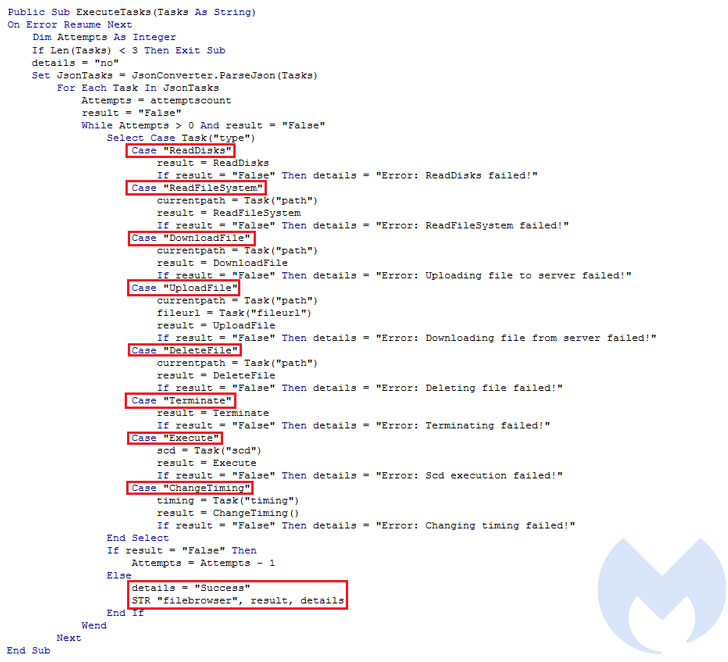
Besides collecting system metadata, the VBA RAT is orchestrated to identify antivirus products running on the infected host and execute commands it receives from an attacker-controlled server, including reading, deleting, and downloading arbitrary files, and exfiltrate the results of those commands back to the server.
Also discovered by Malwarebytes is a PHP-based panel nicknamed “Ekipa” that’s used by the adversary to track victims and view information about the modus operandi that led to the successful breach, highlighting successful exploitation using the IE zero-day and the execution of the RAT.
“As the conflict between Russia and Ukraine over Crimea continues, cyber attacks have been increasing as well,” Jazi said. “The decoy document contains a manifesto that shows a possible motive (Crimea) and target (Russian and pro-Russian individuals) behind this attack. However, it could also have been used as a false flag.”