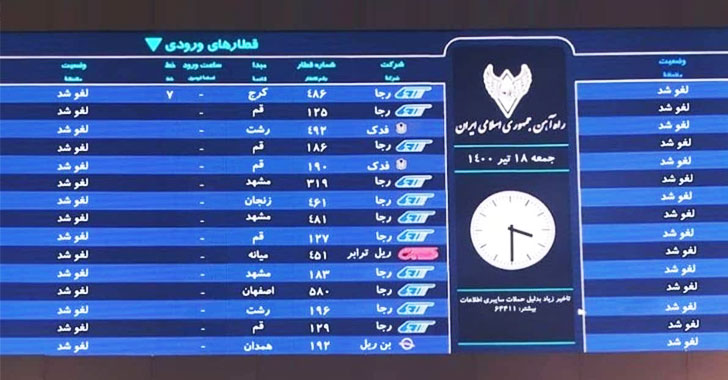
A cyber attack that derailed websites of Iran’s transport ministry and its national railway system earlier this month, causing widespread disruptions in train services, was the result of a never-before-seen reusable wiper malware called “Meteor.”
The campaign — dubbed “MeteorExpress” — has not been linked to any previously identified threat group or to additional attacks, making it the first incident involving the deployment of this malware, according to researchers from Iranian antivirus firm Amn Pardaz and SentinelOne. Meteor is believed to have been in the works over the past three years.
“Despite a lack of specific indicators of compromise, we were able to recover most of the attack components,” SentinelOne’s Principal Threat Researcher, Juan Andres Guerrero-Saade, noted. “Behind this outlandish tale of stopped trains and glib trolls, we found the fingerprints of an unfamiliar attacker,” adding the offensive is “designed to cripple the victim’s systems, leaving no recourse to simple remediation via domain administration or recovery of shadow copies.”
On July 9, the Iranian train system was left paralyzed in the wake of a major attack, with the hackers defacing electronic displays to instruct passengers to direct their complaints to the phone number of the Iranian Supreme Leader Ayatollah Ali Khamenei’s office. The incident is said to have reportedly caused “unprecedented chaos” at stations with hundreds of trains delayed or canceled.
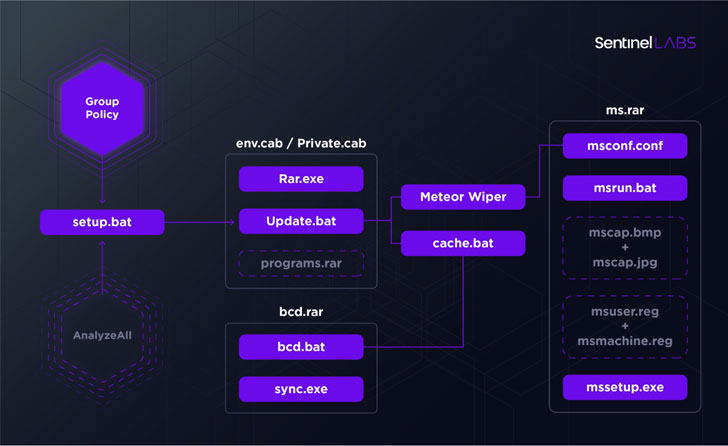
Now according to SentinelOne, the infection chain commenced with the abuse of Group Policy to deploy a toolkit that consisted of a combination of batch files orchestrating different components, which are extracted from multiple RAR archives and are chained together to facilitate the encryption of the filesystem, corruption of the master boot record (MBR), and locking of the system in question.
Other batch script files dropped during the attack were found to take charge of disconnecting the infected device from the network and creating Windows Defender exclusions for all of the components, a tactic that’s becoming increasingly prevalent among threat actors to hide their malicious activities from antimalware solutions installed on the machine.
Meteor, for its part, is an externally configurable wiper with an extensive set of features, including the ability to delete shadow copies as well as a “wealth of additional functionality” such as changing user passwords, terminating arbitrary processes, disabling recovery mode, and executing malicious commands.
The wiper has been characterized as “a bizarre amalgam of custom code” that blends open-source components with ancient software that’s “rife with sanity checks, error checking, and redundancy in accomplishing its goals,” suggesting a fragmented approach and a lack of coordination across different teams involved in the development.
“Conflict in cyberspace is overpopulated with increasingly brazen threat actors. Behind the artistry of this epic troll lies an uncomfortable reality where a previously unknown threat actor is willing to leverage wiper malware against public railways systems,” Guerrero-Saade said. “The attacker is an intermediate level player whose different operational components sharply oscillate from clunky and rudimentary to slick and well-developed.”
“We should keep in mind that the attackers were already familiar with the general setup of their target, features of the domain controller, and the target’s choice of backup system (Veeam). That implies a reconnaissance phase that flew entirely under the radar and a wealth of espionage tooling that we’ve yet to uncover.”