Three distinct clusters of malicious activities operating on behalf of Chinese state interests have staged a series of attacks to target networks belonging to at least five major telecommunications companies located in Southeast Asian countries since 2017.
“The goal of the attackers behind these intrusions was to gain and maintain continuous access to telecommunication providers and to facilitate cyber espionage by collecting sensitive information, compromising high-profile business assets such as the billing servers that contain Call Detail Record (CDR) data, as well as key network components such as the Domain Controllers, Web Servers and Microsoft Exchange servers,” Cybereason’s Lior Rochberger, Tom Fakterman, Daniel Frank, and Assaf Dahan revealed in a technical analysis published Tuesday.
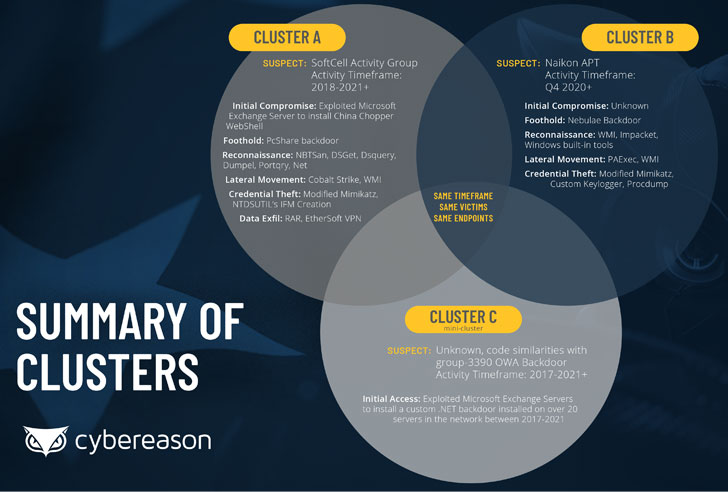
The Boston-based cybersecurity firm linked the campaigns to three different Chinese threat actors, namely Gallium (aka Soft Cell), Naikon APT (aka APT30 or Lotus Panda), and TG-3390 (aka APT27 or Emissary Panda).
The activity surrounding the latter of the three clusters started in 2017, while Gallium-related attacks were first observed in Q4 2020, with the Naikon group jumping on the exploitation bandwagon last in Q4 2020. All three espionage operations are believed to have continued all the way to mid-2021.
Calling the attackers “highly adaptive,” the researchers called out their diligent efforts to stay under the radar and maintain persistence on the infected endpoints, while simultaneously shifting tactics and updating their defensive measures to compromise and backdoor unpatched Microsoft Exchange email servers using the ProxyLogon exploits that came to light earlier this March.
“Each phase of the operation demonstrates the attackers’ adaptiveness in how they responded to various mitigation efforts, changing infrastructure, toolsets, and techniques while attempting to become more stealthy,” the researchers noted.
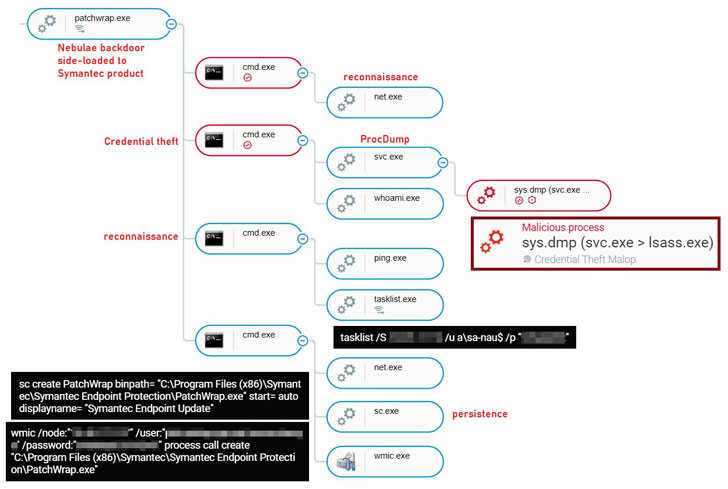
Naikon, on the other hand, was found to leverage a backdoor named “Nebulae” as well as a previously undocumented keylogger dubbed “EnrollLoger” on selected high-profile assets. It’s worth pointing out that Naikon’s use of Nebulae first emerged in April 2021 when the adversary was attributed as behind a wide-ranging cyber-espionage campaign targeting military organizations in Southeast Asia.
Regardless of the attack chain, a successful compromise triggered a sequence of steps, enabling the threat actors to perform network reconnaissance, credential theft, lateral movement, and data exfiltration.
The Emissary Panda cluster is the oldest of the three, primarily involving the deployment of a custom .NET-based OWA (Outlook Web Access) backdoor, which is used to pilfer credentials of users logging into Microsoft OWA services, granting the attackers the ability to access the environment stealthily.
Also of note is the overlap among the clusters in terms of the victimology and the use of generic tools like Mimikatz, with the three groups detected in the same target environment, around the same timeframe, and even on the same systems.
“At this point, there is not enough information to determine with certainty the nature of this overlap — namely, whether these clusters represent the work of three different threat actors working independently, or whether these clusters represent the work of three different teams operating on behalf of a single threat actor,” the researchers said.
“A second hypothesis is that there are two or more Chinese threat actors with different agendas / tasks that are aware of each other’s work and potentially even working in tandem.”