One of the great resources available to businesses today is the large ecosystem of value-added services and solutions. Especially in technology solutions, there is no end to the services of which organizations can avail themselves.
In addition, if a business needs a particular solution or service they don’t handle in-house, there is most likely a third-party vendor that can take care of that for them.
It is highly beneficial for businesses today to access these large pools of third-party resources. However, there can be security challenges for companies using third-party vendors and their services despite the benefits. Let’s look at navigating vendor risk management as IT professionals and see how businesses can accomplish this in a highly complex cybersecurity world.
How can third-party vendors introduce cybersecurity risks?
As mentioned, third-party vendors can be highly beneficial to organizations doing business today. They allow companies to avoid building out technology and other solutions in-house and consume these as a service. These services are crucial for small organizations that may not have the resources or technical expertise to build out the infrastructure and software solutions needed.
However, when companies interact with technology solutions that integrate with their business-critical and sensitive systems, they must consider the potential cybersecurity risks involved.
As the proverbial “weakest link in the chain,” if the cybersecurity practices and posture of a third-party vendor are poor, if their solutions integrate with your systems, the resulting cybersecurity risks now affect your systems. What are the real-world consequences of a vendor-related data breach?
Take note of the following. In 2013, Target Corporation, known as one of the giant retailers in the U.S., fell victim to a data breach due to the hack of a third-party company possessing network credentials for Target’s network.
Attackers first hacked the network of Fazio Mechanical Services, a provider of refrigeration and HVAC services for Target. As a result, attackers compromised 40 million accounts, and Target agreed to pay $10 million in damages to customers who had data stolen.
What is Vendor Risk Management (VRM)?
To meet the cybersecurity challenges in working with third-party vendors, organizations must focus on vendor risk management (VRM). What is VRM? Vendor risk management (VRM) allows organizations to focus on discovering and mitigating risks associated with third-party vendors.
With VRM, businesses have visibility into the vendors they have established relationships with and the security controls they have implemented to ensure their systems and processes are safe and secure.
With the significant risks and compliance regulations that have evolved for businesses today, VRM is a discipline that must be given due attention and have the buy-in from IT professionals and board members alike.
Navigating Vendor Risk Management as IT Professionals
Primarily, the responsibility to discover, understand, and mitigate vendor risk management related to overall cybersecurity falls on the IT department and SecOps. In addition, IT is often responsible for forming the VRM strategy for the business and ensuring the organization’s overall cybersecurity is not sacrificed working with third-party solutions.
To implement a VRM successfully, organizations need to have a framework for managing vendor risk. Here are the seven steps we recommend taking to make sure your organization is safe from vendor risk:
- Identify all vendors providing services for your organization
- Define the acceptable level of risk for your organization
- Identify the most critical risks
- Classify the vendors who provide services for your business
- Conduct regular vendor risk assessments
- Have valid contracts with vendors and proactively track the terms
- Monitor vendor risks over time
1 — Identify all vendors providing services for your organization
Before you can effectively understand the risk to your business, you need to know all vendors used by your organization. A thorough inventory may include everything from lawn care to credit card services.
However, having a thorough understanding and inventory of all vendors helps to ensure risk is calculated appropriately.
2 — Define the acceptable level of risk for your organization
Different types of businesses may have different expectations and risk areas that differ. For example, what is defined as important to a healthcare organization may vary from a financial institution. Whatever the case, determining the acceptable levels of risks helps ensure the appropriate mitigations are put in place, and the risk is acceptable to business stakeholders.
3 — Identify the most critical risks
The risk posed by certain vendors is most likely going to be greater than others. For example, a lawn care company with no access to your technical infrastructure will probably be less risky than a third-party vendor with network-level access to certain business-critical systems. Therefore, ranking your risk levels related to specific vendors is vital to understanding your overall risk.
4 — Classify the vendors who provide services for your business
After vendors are identified who provide services for your business, these should be classified according to what services they offer and the risks they pose to your business.
5 — Conduct regular vendor risk assessments
Even if a business poses a slight risk at one point, this may change later. Like your business, the state of vendor infrastructure, services, software, and cybersecurity posture is constantly in flux. Therefore, perform regular vendor assessments to quickly identify a sudden change in the risk to your organization.
6 — Have valid contracts with vendors and proactively track the terms
Ensure you have valid contracts with all vendors. A contractual agreement legally establishes the expectations across all fronts, including security and risk assessment. Track the contracts and terms over time. It allows identifying any deviation from the contract terms as expressed.
7 — Monitor vendor risks over time
Monitor the risks posed by vendors over time. As discussed above, conducting regular vendor risk assessments and monitoring the risk over time helps to gain visibility into the risk that may continue to grow with a particular vendor. It may signal the need to look for another vendor.
Track credential security for third-party vendors
An area of concern working with a vendor or if you are a third-party vendor used by an organization is credentials. How do you ensure that credentials used by third-party vendors are secure? How do you prove you are on top of password security in your environment if a business requests proof of your credential security?
Specops Password Policy is a solution that allows businesses to bolster their password security and overall cybersecurity posture by:
- Breached password protection
- Implementing strong password policies
- Allowing the use of multiple password dictionaries
- Clear and intuitive client messaging
- Real-time dynamic feedback to the client
- Length-based password expiration
- Blocking of common password components such as usernames in passwords
- Easily implement passphrases
- Regular expressions
Specops Breached Password Protection now includes Live Attack Data as part of the Specops Breached Password Protection module. It allows Specops Password Policy with Breached Password Protection to protect your organization from breached passwords from both billions of breached passwords in the Specops database as well as from live attack data.
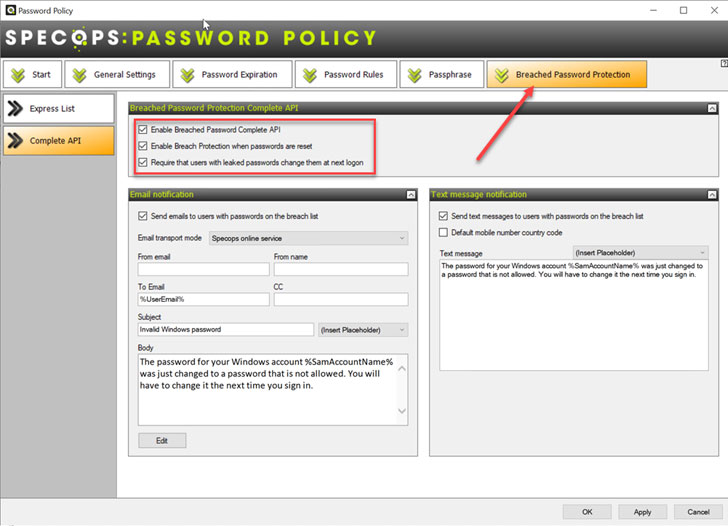 |
| Protect vendor passwords with Specops Breached Password Protection |
If third-party vendor credentials in use in your environment become breached, you will be able to remediate the risk as soon as possible. Also, in conjunction with Specops Password Auditor, you can quickly and easily produce reports of the password standards you have in place in your organization.
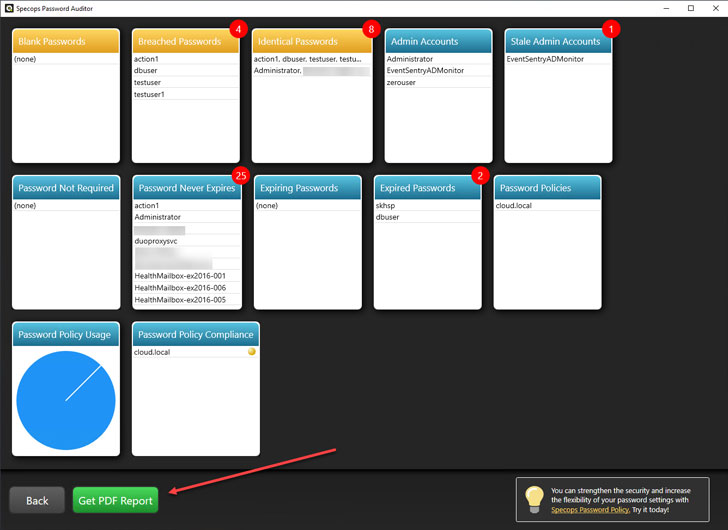 |
| Produce audit reports using Specops Password Auditor |
Wrapping it Up
Vendor Risk Management (VRM) is an essential part of the overall cybersecurity processes of organizations today. It allows managing the risks associated with third-party vendors and how these interact with your organization. Businesses must implement a framework to evaluate vendor risk and ensure these risks are tracked, documented, and monitored as needed.
Specops Password Policy and Specops Password Auditor allow businesses to bolster password security in their environment. It helps mitigate any risks associated with vendor passwords and easily monitors passwords to know if these become breached. In addition, Password Auditor can produce reports if you provide third-party services to organizations requesting you provide information regarding your password settings and policies.
