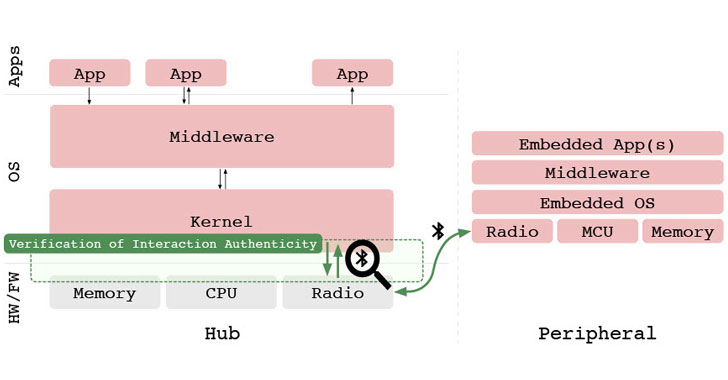
A group of academics has proposed a machine learning approach that uses authentic interactions between devices in Bluetooth networks as a foundation to handle device-to-device authentication reliably.
Called “Verification of Interaction Authenticity” (aka VIA), the recurring authentication scheme aims to solve the problem of passive, continuous authentication and automatic deauthentication once two devices are paired with one another, which remain authenticated until an explicit deauthentication action is taken, or the authenticated session expires.
“Consider devices that pair via Bluetooth, which commonly follow the pattern of pair once, trust indefinitely. After two devices connect, those devices are bonded until a user explicitly removes the bond. This bond is likely to remain intact as long as the devices exist, or until they transfer ownership,” Travis Peters, one of the co-authors of the study, said.
“The increased adoption of (Bluetooth-enabled) IoT devices and reports of the inadequacy of their security makes indefinite trust of devices problematic. The reality of ubiquitous connectivity and frequent mobility gives rise to a myriad of opportunities for devices to be compromised,” Peters added.
Authentication is a process to verify that an individual or a system is, in fact, who or what it claims to be. While authentication can also be achieved by identification — something who you are — the latest research approaches it from a verification perspective in that it aims to validate that apps and devices interact in a manner that’s consistent with their prior observations. In other words, the device’s interaction patterns act as a barometer of its overall behavior.
To this end, the recurring validation of interaction patterns allows for authenticating the device by cross-checking the device’s behavior against a previously learned machine learning model that represents typical, trustworthy interactions, with the first authentication factor being the use of traditional Bluetooth identifiers and credentials.
“For example, a user that has a blood-pressure device may really only care if a blood-pressure monitor device is ‘hooked up’ to the measurement app, and is operating in a way that is consistent with how a blood-pressure monitor should operate,” the researchers outlined.
“Presumably, so long as these properties hold, there is no immediate or obvious threat. If, however, a device connects as a blood-pressure monitor and then goes on to interact in a way that is inconsistent with typical interactions for this type of device, then there may be cause for concern.”
VIA works by extracting features from packet headers and payloads and comparing them to a verification model to corroborate whether the ongoing interactions are consistent with this known authentic behavioral model, and if so, permit the devices to continue communicating with each other. As a consequence, any deviation from authentic interactions will result in failed verification, allowing devices to take steps to mitigate any future threat.
The model is constructed using a combination of features, such as n-grams built from deep packet inspection, protocol identifiers and packet types, packet lengths, and packet directionality. The dataset consists of a collection of 300 Bluetooth HCI network traces that capture interactions between 20 distinct smart health and smart home devices and 13 different smartphone apps installed on a Nexus 5 smartphone running Android 6.0.1.
“We see VIA’s recurring verification of interaction patterns as a sort of second factor for authenticating the device,” the researchers said. “As a result of this scheme, we introduce the notion of recurring behavioral authentication for Bluetooth connections, which can be integrated into a Bluetooth gateway device, such as a smartphone.”