Microsoft’s Active Directory is said to be used by 95% of Fortune 500. As a result, it is a prime target for attackers as they look to gain access to credentials in the organization, as compromised credentials provide one of the easiest ways for hackers to access your data.
A key authentication technology that underpins Microsoft Active Directory is Kerberos. Unfortunately, hackers use many different attacks against Active Directory’s implementation of the Kerberos authentication protocol. One of those is AS-REP Roasting. So what is AS-REP Roasting, and how can businesses protect themselves?
What is Active Directory Kerberos?
Kerberos was originally developed by the Massachusetts Institute of Technology (MIT) and centered around using tickets to establish trust. Microsoft’s implementation of Kerberos found in Active Directory is based on Kerberos Network Authentication Service (V5) as defined in RFC 4120. However, Microsoft has added to and enhanced Kerberos with its protocol specifications and several extensions.
There are three different components found in Kerberos authentication as found in Microsoft Active Directory. These include:
- Client – The client is the entity that is looking to obtain tickets from the KDC
- Application Server – The resource that needs the issued tickets presented for authentication
- Key Distribution Center (KDC) – The KDC is the trusted third-party that issues the authentication tickets. In Microsoft Active Directory, the KDC is each domain controller servicing the Active Directory domain.
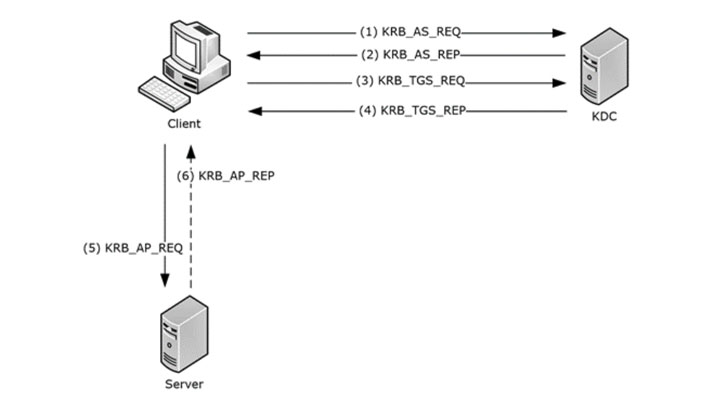 |
| Overview of the Kerberos authentication protocol ticket exchange |
Essential for understanding the risks associated with Active Directory credential theft, Kerberos is the default protocol used when logging into a Windows machine part of an Active Directory domain. It has been the default authentication protocol, replacing NTLM since Windows 2000 and later. What are the differences between the two?
The two protocols manage authentication differently. The NTLM authentication protocol relies on a three-way handshake. The authentication information is exchanged between the client and server to authenticate a user. Conversely, Kerberos uses a two-way process that relies on a ticket-granting service using a key distribution center (KDC).
NTLM uses password hashing, whereas Kerberos uses encryption. While Kerberos is the default authentication method, NTLM is still used as a fallback authentication protocol. If authentication can’t happen using Kerberos, the system will use NTLM instead.
What is AS-REP Roasting?
Even though Kerberos is a much more secure authentication protocol than NTLM, it is not without its own set of vulnerabilities, some of which can stem from the specific user account settings configured for the account in Active Directory.
One of the first steps in Kerberos authentication is preauthentication. Pre-authentication uses the user’s password to encrypt a timestamp. The domain controller (DC) will decrypt this to validate the correct password and not have a previous request replayed. A vulnerability can result when preauthentication is disabled.
Once this is disabled, a hacker can request authentication data for any user, and the DC will return an encrypted ticket-granting ticket (TGT). It can then be used to brute force in an offline environment to crack the password.
Preauthentication can be disabled on any user account in Active Directory on the Account tab under the Account options. Look for the checkbox “Do not require Kerberos preauthentication.”
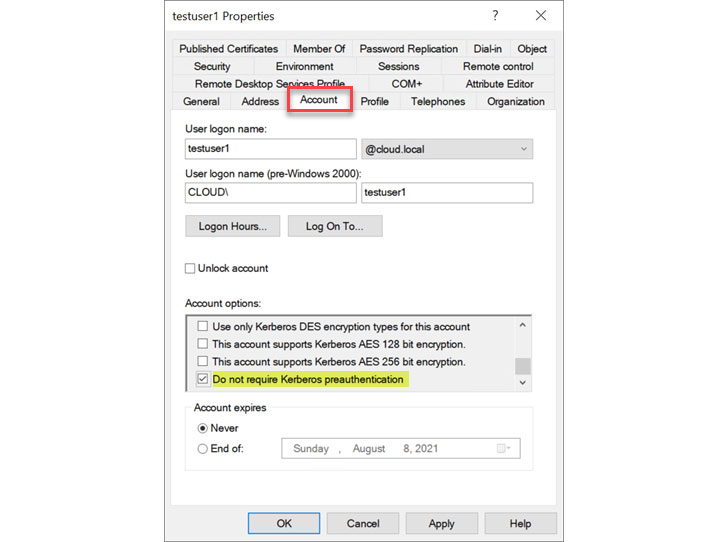 |
| Setting the do not require Kerberos preauthentication flag in Active Directory |
AS-REP Roasting is the technique that allows retrieving password hashes for users that have this flag set in Active Directory. Additionally, various cybersecurity and hacking tools allow cracking the TGTs harvested from Active Directory. These include Rubeus and Hashcat.
Using a tool like Rubeus, attackers can find the accounts that do not require preauthentication and then extract the ticket-granting ticket (TGT) data for cracking the password offline.
Data can be transformed into a format that can be cracked by an offline tool such as Hashcat, which can use brute force password cracking against the hashes. This process incorporates the use of a dictionary file for brute-force password guessing.
Preventing the AS-REP Roasting attack
An obvious way to prevent the AS-REP Roasting attack is to audit your Active Directory environment and ensure there are no accounts configured with the “Do not require Kerberos preauthentication.”
In addition to auditing your Active Directory settings for improperly configured preauthentication, you want to make sure users are required to use strong, complex passwords.
Also, it is vital to ensure passwords are not found in a breached password database as breached password lists are used to crack passwords extracted using the AS-REP Roasting attack. Breached password protection is not natively found in Active Directory. So, a third-party solution is required for this type of protection.
Breached password protection with Specops
Enforcing effective password policies and using a breached password protection solution for Active Directory is essential to ensure your environment is not vulnerable to Kerberos attacks such as AS-REP Roasting. In addition, effective password policies help ensure users are using strong passwords that are not easily guessed or otherwise easy to attack with brute force or other common password attacks.
Specops Password Policy takes password policies into the modern era with functionality and features not natively found in Active Directory. It prevents weak and even breached passwords from use in the environment using one of the most important features of Specops Password Policy, Breached Password Protection.
Recently, Specops released the next iteration of Breached Password Protection with Live Attack Data. The Live Attack Data comes from a global honeypot solution used by Specops to gather the passwords that are used in live brute force attacks. These are integrated with the current protection offered by Specops to customers using the Breached Password database and the solution is continuously updated with the most recent breached passwords.
In addition, with Breached Password Protection found in Specops Password Policy, organizations can quickly implement breached password protection to prevent users from using compromised passwords. For example, if users attempt to choose a password found in the extensive database of breached passwords maintained by Specops (over two billion), the password is not accepted. In addition, if a user’s password becomes breached after it has been defined in Active Directory, organizations can use Specops Password Policy to force their users to change the password at next login.
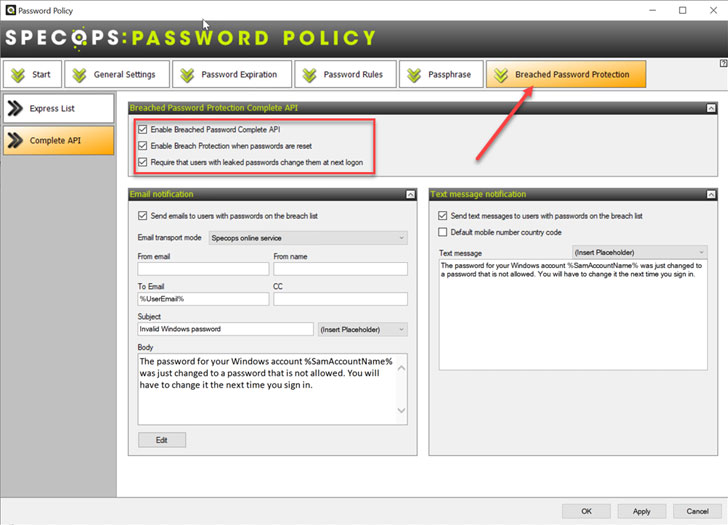 |
| Specops Password Policy Breached Password Protection |
On top of the Breached Password Protection in Specops Password Policy, it adds many other features and benefits to bolster your organization’s ability to tailor password policies to fit the business needs and maintain high levels of security in your environment. These include:
- Ability to add multiple custom password dictionaries
- Length-based password aging
- Built-in password expiration notifications
- Password content restrictions
- Regular expressions to further control password content
- Multiple password reset options
- Minimum number of characters that are required changed for a password reset
Considerations
Active Directory is the number one identity solution used in organizations today. Unfortunately, his means attackers heavily target Active Directory environments to find ways to steal credentials. Their attack methods include attacking the authentication protocols used by Active Directory, including Kerberos. AS-REP Roasting is a type of attack that looks to find accounts with the preauthentication flag for Kerberos unset for users.
Once found, hacking tools can be used to brute force user passwords. One of the best ways organizations can defend themselves is to have good password policies in place along with breached password protection, as attackers often use breached password databases in an AS-REP Roasting attack. Specops Password Policy helps businesses bolster their password security, including Breached Password Protection.
