WhatsApp on Friday announced it will roll out support for end-to-end encrypted chat backups on the cloud for Android and iOS users, paving the way for storing information such as chat messages and photos in Apple iCloud or Google Drive in a cryptographically secure manner.
The feature, which will go live to all of its two billion users in the coming weeks, is expected to only work on the primary devices tied to their accounts, and not companion devices such as desktops or laptops that simply mirror the content of WhatsApp on the phones.
While the Facebook-owned messaging platform flipped the switch on end-to-end encryption (E2EE) for personal messages, calls, video chats, and media between senders and recipients as far back as April 2016, the content — should a user opt to back up on the cloud to enable the transfer of chat history to a new device — wasn’t subjected to the same security protections until now.
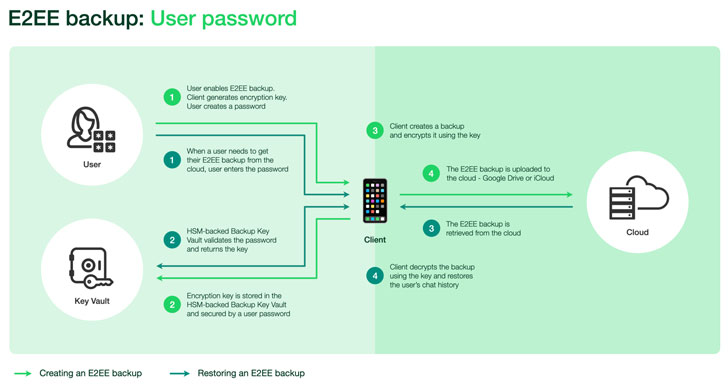
“With the introduction of end-to-end encrypted backups, WhatsApp has created an HSM (Hardware Security Module) based Backup Key Vault to securely store per-user encryption keys for user backups in tamper-resistant storage, thus ensuring stronger security of users’ message history,” the company said in a whitepaper.
“With end-to-end encrypted backups enabled, before storing backups in the cloud, the client encrypts the chat messages and all the messaging data (i e text, photos, videos, etc) that is being backed up using a random key that’s generated on the user’s device,” it added.
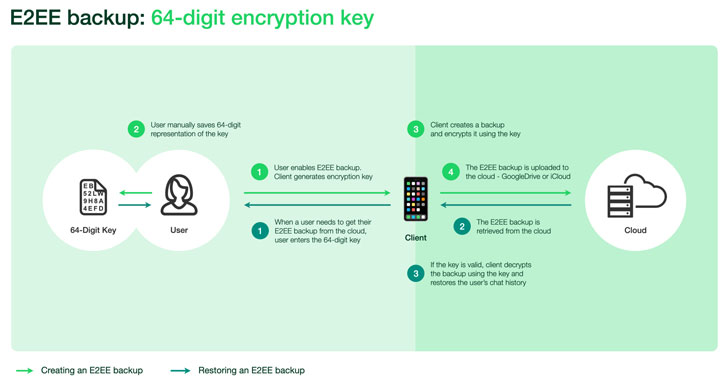
To that end, the key to encrypt the backup is secured with a user-furnished password, which is stored in the vault to permit easy recovery in the event the device gets stolen. Alternatively, users have the option of providing a 64-digit encryption key instead of a password — but in this scenario, the encryption key will have to be stored manually given that it will no longer be sent to the HSM Backup Key Vault.
Thus when an account owner needs access to their backup, it can be done so with the help of the password or the 64-digit key, which, subsequently, is employed to retrieve the encryption key from the backup key vault and decrypt their backups.
The vault, in itself, is geographically distributed across five data centers and is also responsible for enforcing password verification as well as rendering the key permanently inaccessible after a set threshold for the number of unsuccessful attempts is crossed so as to safeguard against brute-force attacks to retrieve the key by malicious actors.
Unencrypted cloud backups have been a major security loophole using which law enforcement agencies have been able to access WhatsApp chats to gather incriminating evidence pertaining to criminal investigations. In addressing this escape outlet, the company is once again setting itself on the warpath with governments across the world, who have decried Facebook’s decision to introduce E2EE across all of its services.
Facebook has since adopted E2EE for Secret Conversations on Messenger and recently extended the feature for voice calls and video calls. In addition, the social media giant is planning a limited test of E2EE for Instagram direct messages.
“WhatsApp is the first global messaging service at this scale to offer end-to-end encrypted messaging and backups, and getting there was a really hard technical challenge that required an entirely new framework for key storage and cloud storage across operating systems,” said Facebook’s chief executive Mark Zuckerberg in a post.