In the classic children’s movie ‘The Princess Bride,’ one of the characters utters the phrase, “You keep using that word. I do not think it means what you think it means.”
It’s freely used as a response to someone’s misuse or misunderstanding of a word or phrase.
“Response Automation” is another one of those phrases that have different meanings to different people. It’s bantered around by the security vendor community so much that its precise meaning, when used, is unclear.
Many vendors throw the term out without explaining exactly what they mean by the phrase. One vendor’s response automation might, and often do, perform very differently from another vendor’s response automation capabilities. But, hey, they have “response automation!”
A recently published guide is meant to make sense of Response Automation (Download here). It discusses the evolution of response automation and distinguishes five increasingly capable levels of response automation available today. The guide will help you understand exactly what is meant when someone offers response automation, as well as the questions to ask to help clear up any confusion.
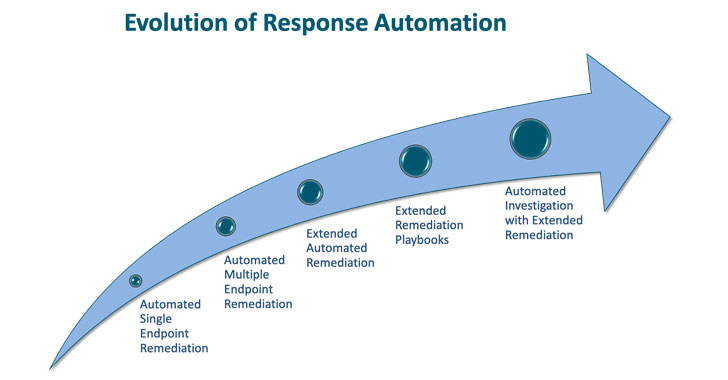 |
| The five progressive levels of response automation |
The guide also shares the types of security solutions that provide the varying levels of response automation, including Next-Generation Antivirus (NGAV), Endpoint Detection and Response (EDR), Extended Detection and Response (EDR) and Security Orchestration, Automation and Response (SOAR).
The capabilities of each solution category are quite different, which directly impacts each’s the ability to provide sophisticated response automation features.
The Five Levels of Response Automation
As depicted in the chart above, Cynet frames the five increasingly capable levels of response automation, along with the specific benefits provided by each. The most basic type of response automation involves remediating a specific threat in response to an alert on an endpoint. This, Cynet says, is table stakes for any threat detection and response (TDR) solution.
The ultimate level of response automation involves moving beyond remediation actions to include fully automated investigatory steps to determine if a detected threat actually part of a larger attack and, if so, uncovering related attack components. When a threat is detected, the automated investigation uncovers the root cause of the threat – how did the threat come to be in the environment.
As components of an attack are uncovered, an automated investigation can search the environment to expose the full scope of the attack. And, of course, appropriate remediation actions are taken at every step to eradicate all attack components.
The Real Meaning of Response Automation
The security community is very aware of the talent shortage and the ongoing pressures of “alert overload.” It only makes sense that the more we can take off the plate of security professionals, the better things would be. Better in what way?
First, automating repetitive and more pedestrian tasks would free up significant time for security staff to focus on more important items. And maybe reducing the time required to chase alerts precludes the need for additional staff.
Second, speeding up threat response to machine time reduces the likelihood that the threat may proliferate or cause immediate damage. Response automation at a minimum provides a healthy head start for security analysts in their threat response workflow.
For those of you that would welcome a tool to help improve security while reducing manual effort – let’s turn to another famous quote from The Princess Bride – “As you wish.”
Download the essential guide for Response Automation here

