An unpatched design flaw in the implementation of Microsoft Exchange’s Autodiscover protocol has resulted in the leak of approximately 100,000 login names and passwords for Windows domains worldwide.
“This is a severe security issue, since if an attacker can control such domains or has the ability to ‘sniff’ traffic in the same network, they can capture domain credentials in plain text (HTTP basic authentication) that are being transferred over the wire,” Guardicore’s Amit Serper said in a technical report.
“Moreover, if the attacker has DNS-poisoning capabilities on a large scale (such as a nation-state attacker), they could systematically syphon out leaky passwords through a large-scale DNS poisoning campaign based on these Autodiscover TLDs [top-level domains].”
The Exchange Autodiscover service enables users to configure applications such as Microsoft Outlook with minimal user input, allowing just a combination of email addresses and passwords to be utilized to retrieve other predefined settings required to set up their email clients.
The weakness discovered by Guardicore resides in a specific implementation of Autodiscover based on the POX (aka “plain old XML”) XML protocol that causes the web requests to Autodiscover domains to be leaked outside of the user’s domain but in the same top-level domain.
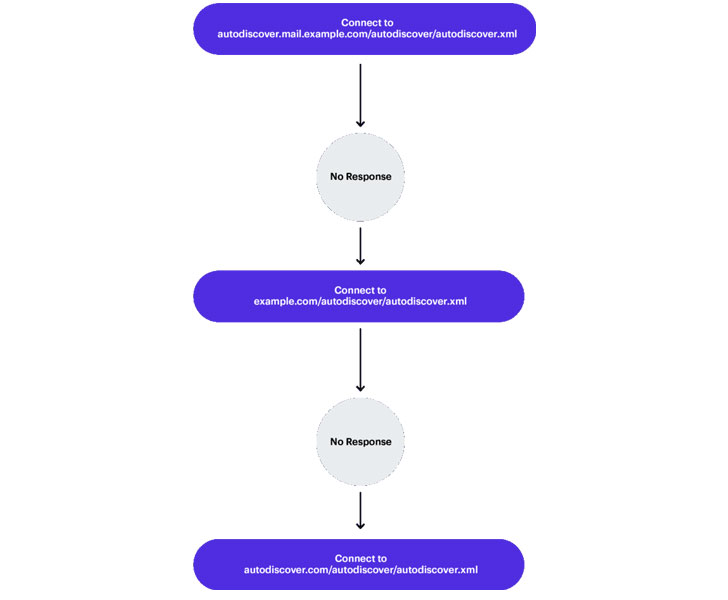
In a hypothetical example where a user’s email address is “user@example.com,” the email client leverages the Autodiscover service to construct a URL to fetch the configuration data using any of the below combinations of the email domain, a subdomain, and a path string, failing which it instantiates a “back-off” algorithm —
- https://Autodiscover.example.com/Autodiscover/Autodiscover.xml
- https://Autodiscover.example.com/Autodiscover/Autodiscover.xml
- https://example.com/Autodiscover/Autodiscover.xml
- https://example.com/Autodiscover/Autodiscover.xml
“This ‘back-off’ mechanism is the culprit of this leak because it is always trying to resolve the Autodiscover portion of the domain and it will always try to ‘fail up,’ so to speak,” Serper explained. “Meaning, the result of the next attempt to build an Autodiscover URL would be: ‘https://Autodiscover.com/Autodiscover/Autodiscover.xml.’ This means that whoever owns Autodiscover.com will receive all of the requests that cannot reach the original domain.”
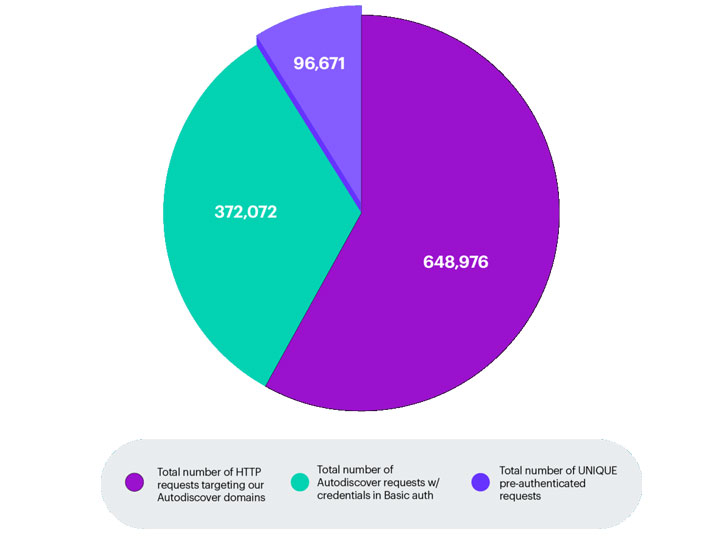
Armed with this discovery and by registering a number of Autodiscover top-level domains (e.g., Autodiscover.com[.]br, Autodiscover.com[.]cn, Autodiscover[.]in, etc.) as honeypots, Guardicore said it was able to access requests to Autodiscover endpoints from different domains, IP addresses, and clients, netting 96,671 unique credentials sent from Outlook, mobile email clients, and other applications interfacing with Microsoft’s Exchange server over a four-month period between April 16, 2021, and August 25, 2021.
The domains of those leaked credentials belonged to several entities from multiple verticals spanning publicly traded corporations in China, investment banks, food manufacturers, power plants, and real estate firms, the Boston-based cybersecurity company noted.
To make matters worse, the researchers developed an “ol’ switcheroo” attack that involved sending a request to the client to downgrade to a weaker authentication scheme (i.e., HTTP Basic authentication) in place of secure methods like OAuth or NTLM, prompting the email application to send the domain credentials in cleartext.
“Oftentimes, attackers will try to cause users to send them their credentials by applying various techniques, whether technical or through social engineering,” Serper said. “However, this incident shows us that passwords can be leaked outside of the organization’s perimeter by a protocol that was meant to streamline the IT department’s operations with regards to email client configuration without anyone from the IT or security department even being aware of it, which emphasises the importance of proper segmentation and Zero Trust.”