Two newly discovered malicious Android applications on Google Play Store have been used to target users of Brazil’s instant payment ecosystem in a likely attempt to lure victims into fraudulently transferring their entire account balances into another bank account under cybercriminals’ control.
“The attackers distributed two different variants of banking malware, named PixStealer and MalRhino, through two separate malicious applications […] to carry out their attacks,” Check Point Research said in an analysis shared with The Hacker News. “Both malicious applications were designed to steal money of victims through user interaction and the original PIX application.”
The two apps in question, which were uncovered in April 2021, have since been removed from the app store.
Launched in November 2020 by the Central Bank of Brazil, the country’s monetary authority, Pix is a state-owned payments platform that enables consumers and companies to make money transfers from their bank accounts without requiring debit or credit cards.
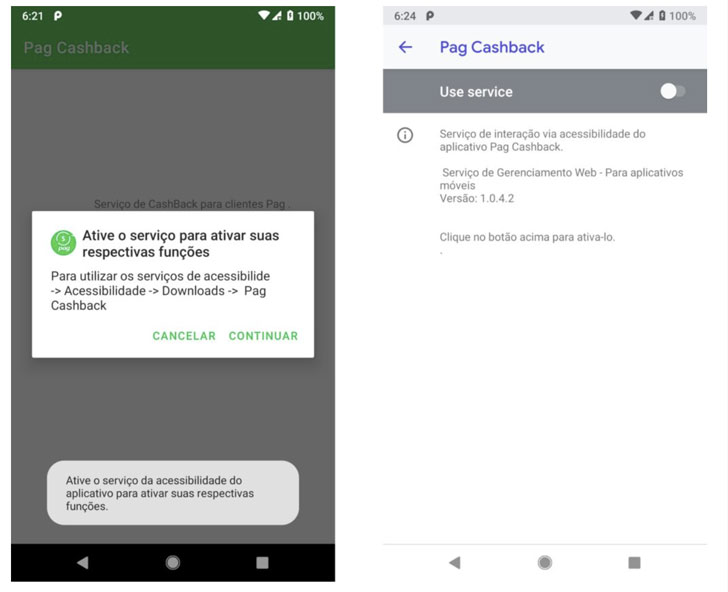
PixStealer, which was found distributed on Google Play as a fake PagBank Cashback service app, is designed to empty a victim’s funds to an actor-controlled account, while MalRhino — masquerading as a mobile token app for Brazil’s Inter bank — comes with advanced features necessary to collect the list of installed apps and retrieve PIN for specific banks.
“When a user opens their PIX bank application, Pixstealer shows the victim an overlay window, where the user can’t see the attacker’s moves,” the researchers said. “Behind the overlay window, the attacker retrieves the available amount of money and transfers the money, often the entire account balance, to another account.”
What unites PixStealer and MalRhino is that both the apps abuse Android’s accessibility service to perform malicious actions on the compromised devices, making them the latest addition to a long list of mobile malware that leverages the permission to perpetrate data theft.
Specifically, the fake overlay comes with a message “Synchronizing your access… Do not turn off your mobile screen” when, in reality, the malware searches for the “Transfer” button to perform the transfer using a series of accessibility APIs.
The MalRhino variant also stands out for its use of Mozilla’s Java-based Rhino JS framework to run JavaScript commands inside targeted banking applications, but not before convincing the user to turn on accessibility services.
“This technique is not commonly used on mobile malware and shows how malicious actors are getting innovative to avoid detection and get inside Google Play,” the researchers said. “With the increasing abuse of the Accessibility Service by mobile banking malware, users should be wary of enabling the relevant permissions even in the applications distributed via known app stores such as Google Play.”