Cybersecurity researchers on Wednesday disclosed a previously undocumented backdoor likely designed and developed by the Nobelium advanced persistent threat (APT) behind last year’s SolarWinds supply chain attack, joining the threat actor’s ever-expanding arsenal of hacking tools.
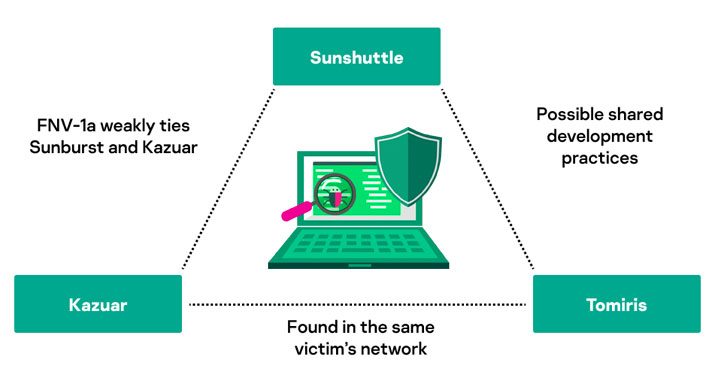
Moscow-headquartered firm Kaspersky codenamed the malware “Tomiris,” calling out its similarities to another second-stage malware used during the campaign, SUNSHUTTLE (aka GoldMax), targeting the IT management software provider’s Orion platform. Nobelium is also known by the monikers UNC2452, SolarStorm, StellarParticle, Dark Halo, and Iron Ritual.
“While supply-chain attacks were already a documented attack vector leveraged by a number of APT actors, this specific campaign stood out due to the extreme carefulness of the attackers and the high-profile nature of their victims,” Kaspersky researchers said. “Evidence gathered so far indicates that Dark Halo spent six months inside Orion IT’s networks to perfect their attack and make sure that their tampering of the build chain wouldn’t cause any adverse effects.”
Microsoft, which detailed SUNSHUTTLE in March 2021, described the strain as a Golang-based malware that acts as a command-and-control backdoor, establishing a secure connection with an attacker-controlled server to fetch and execute arbitrary commands on the compromised machine as well as exfiltrate files from the system to the server.
The new Tomiris backdoor, found by Kaspersky in June this year from samples dating back to February, is also written in Go and deployed via a successful DNS hijacking attack during which targets attempting to access the login page of a corporate email service were redirected to a fraudulent domain set up with a lookalike interface designed to trick the visitors into downloading the malware under the guise of a security update.
The attacks are believed to have been mounted against several government organizations in an unnamed CIS member state.
“The main purpose of the backdoor was to establish a foothold in the attacked system and to download other malicious components,” the researchers said, in addition to finding a number of similarities ranging from the encryption scheme to the same spelling mistakes that collectively hint at the “possibility of common authorship or shared development practices.”
This is not the first time overlaps have been discovered between different tools put to use by the threat actor. Earlier this year, Kaspersky’s analysis of Sunburst revealed a number of shared features between the malware and Kazuar, a .NET-based backdoor attributed to the Turla group. Interestingly, the cybersecurity company said it detected Tomiris in networks where other machines were infected with Kazuar, adding weight to prospects that the three malware families could be linked to each other.
Having said that, the researchers pointed out it could also be a case of a false flag attack, wherein threat actors deliberately reproduce the tactics and techniques adopted by a known adversary in an attempt to mislead attribution.
The revelation comes days after Microsoft took the wraps of a passive and highly targeted implant dubbed FoggyWeb that was employed by the Nobelium group to deliver additional payloads and steal sensitive information from Active Directory Federation Services (AD FS) servers.