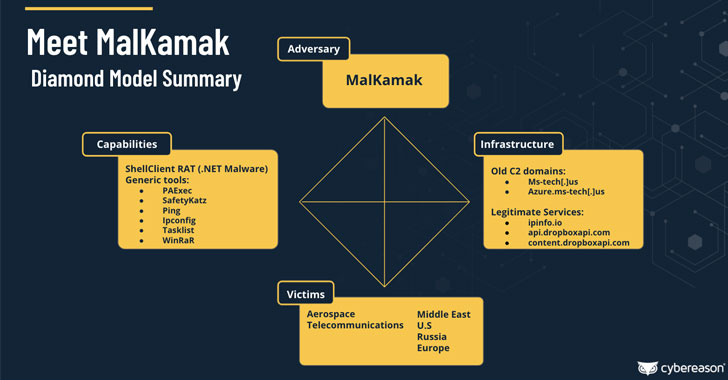
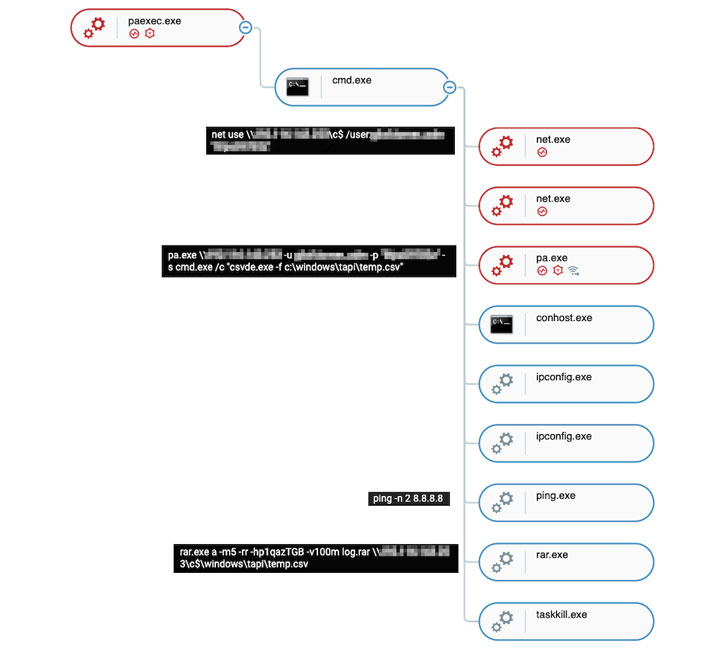
Details have emerged about a new cyber espionage campaign directed against the aerospace and telecommunications industries, primarily in the Middle East, with the goal of stealing sensitive information about critical assets, organizations’ infrastructure, and technology while remaining in the dark and successfully evading security solutions.
Boston-based cybersecurity company Cybereason dubbed the attacks “Operation Ghostshell,” pointing out the use of a previously undocumented and stealthy remote access trojan (RAT) called ShellClient that’s deployed as the main spy tool of choice. The first sign of the attacks was observed in July 2021 against a handpicked set of victims, indicating a highly targeted approach.
“The ShellClient RAT has been under ongoing development since at least 2018, with several iterations that introduced new functionalities, while it evaded antivirus tools and managed to remain undetected and publicly unknown,” researchers Tom Fakterman, Daniel Frank, Chen Erlich, and Assaf Dahan said in a technical deep dive published today.
Cybereason traced the roots of this threat back to at least November 6, 2018, previously operating as a standalone reverse shell before evolving to a sophisticated backdoor, highlighting that the malware has been under continuous development with new features and capabilities added by its authors. What’s more, the adversary behind the attacks is also said to have deployed an unknown executable named “lsa.exe” to perform credential dumping.
Investigation into the attribution of the cyber-attacks has also yielded an entirely new Iranian threat actor named MalKamak that has been operating since around the same time period and has eluded discovery and analysis thus far, with possible connections to other Iranian state-sponsored APT threat actors such as Chafer APT (aka APT39) and Agrius APT, the latter of which was found posing as ransomware operators in an effort to conceal the origin of a series of data-wiping hacks against Israeli entities.
Besides carrying out reconnaissance and the exfiltration of sensitive data, ShellClient is engineered as a modular portable executable that’s capable of performing fingerprinting and registry operations. Also of note is the RAT’s abuse of cloud storage services such as Dropbox for command-and-control (C2) communications in an attempt to stay under the radar by blending in with legitimate network traffic originating from the compromised systems.
The Dropbox storage contains three folders, each storing information about the infected machines, the commands to be executed by the ShellClient RAT, and the results of those commands. “Every two seconds, the victim machine checks the commands folder, retrieves files that represent commands, parses their content, then deletes them from the remote folder and enables them for execution,” the researchers said.
The aforementioned modus operandi mirrors a tactic adopted by another threat actor called IndigoZebra, which was uncovered as relying on Dropbox API to store commands in a victim-specific sub-folder that’s retrieved by the malware prior to execution.
The findings also arrive days after a new advanced persistent threat dubbed “ChamelGang” was identified as behind a string of attacks targeting fuel, energy, and aviation production industries in Russia, the U.S., India, Nepal, Taiwan, and Japan with the goal of stealing data from compromised networks.