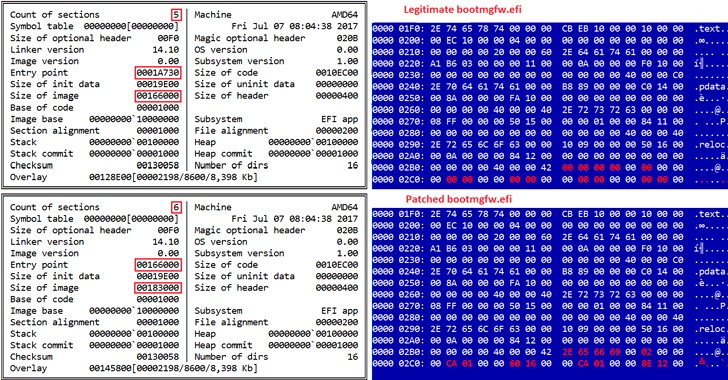
Cybersecurity researchers on Tuesday revealed details of a previously undocumented UEFI (Unified Extensible Firmware Interface) bootkit that has been put to use by threat actors to backdoor Windows systems as early as 2012 by modifying a legitimate Windows Boot Manager binary to achieve persistence, once again demonstrating how technology meant to secure the environment prior to loading the operating system is increasingly becoming a “tempting target.”
Slovak cybersecurity firm ESET codenamed the new malware “ESPecter” for its ability to persist on the EFI System Partition (ESP), in addition to circumventing Microsoft Windows Driver Signature Enforcement to load its own unsigned driver that can be used to facilitate espionage activities such as document theft, keylogging, and screen monitoring by periodically capturing screenshots.
“ESPecter shows that threat actors are relying not only on UEFI firmware implants when it comes to pre-OS persistence and, despite the existing security mechanisms like UEFI Secure Boot, invest their time into creating malware that would be easily blocked by such mechanisms, if enabled and configured correctly,” ESET researchers Martin Smolár and Anton Cherepanov said in a technical write-up published Tuesday.
The development marks the fourth time real-world cases of UEFI malware have been discovered so far, following LoJax, MosaicRegressor, and most recently FinFisher, the last of which was found leveraging the same method of compromise to persist on the ESP in the form of a patched Windows Boot Manager.
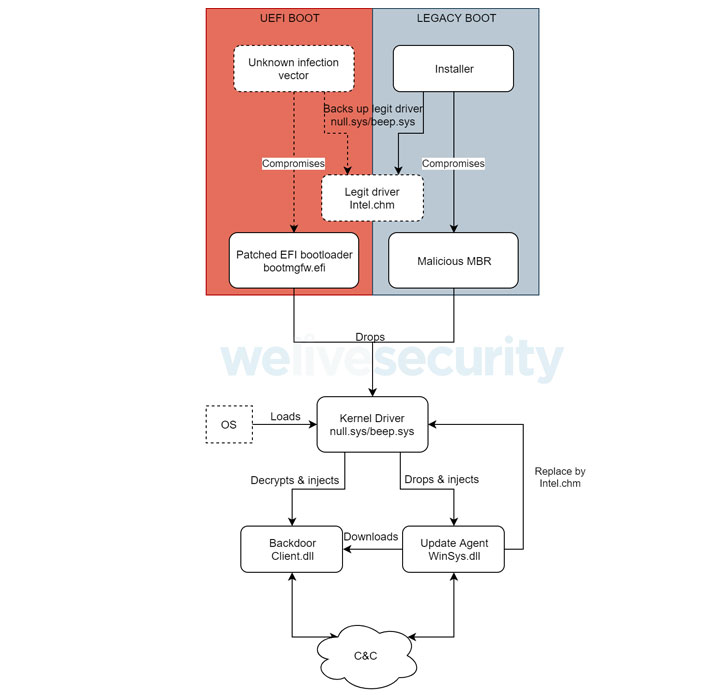
“By patching the Windows Boot Manager, attackers achieve execution in the early stages of the system boot process, before the operating system is fully loaded,” the researchers said. “This allows ESPecter to bypass Windows Driver Signature Enforcement (DSE) in order to execute its own unsigned driver at system startup.”
However, on systems that support Legacy BIOS Boot Mode, ESPecter gains persistence by altering the master boot record (MBR) code located in the first physical sector of the disk drive to interfere with the loading of the boot manager and load the malicious kernel driver, which is designed to load additional user-mode payloads and set up the keylogger, before erasing its own traces from the machine.
In the final phase, the driver is used to inject next-stage user-mode components into specific system processes to establish communications with a remote server, thereby enabling an attacker to commandeer the compromised machine and take over control, not to mention download and execute more malware or commands fetched from the server.
ESET did not attribute the bootkit to a particular nation-state or hacking group, but the use of Chinese debug messages in the user-mode client payload has raised the possibility that it could be the work of an unknown Chinese-speaking threat actor.
“Even though Secure Boot stands in the way of executing untrusted UEFI binaries from the ESP, over the last few years we have been witness to various UEFI firmware vulnerabilities affecting thousands of devices that allow disabling or bypassing Secure Boot,” the researchers noted. “This shows that securing UEFI firmware is a challenging task and that the way various vendors apply security policies and use UEFI services is not always ideal.”