Multiple security vulnerabilities have been disclosed in softphone software from Linphone and MicroSIP that could be exploited by an unauthenticated remote adversary to crash the client and even extract sensitive information like password hashes by simply making a malicious call.
The vulnerabilities, which were discovered by Moritz Abrell of German pen-testing firm SySS GmbH, have since been addressed by the respective manufacturers following responsible disclosure.
Softphones are essentially software-based phones that mimic desk phones and allow for making telephone calls over the Internet without the need for using dedicated hardware. At the core of the issues are the SIP services offered by the clients to connect two peers to facilitate telephony services in IP-based mobile networks.
SIP aka Session Initiation Protocol is a signaling protocol that’s used to control interactive communication sessions, such as voice, video, chat and instant messaging, as well as games and virtual reality, between endpoints, in addition to defining rules that govern the establishment and termination of each session.
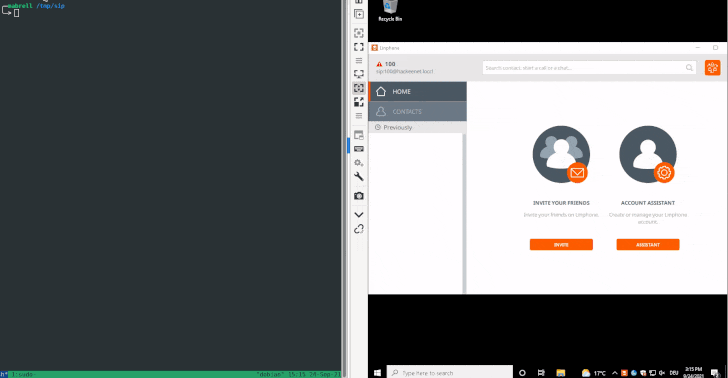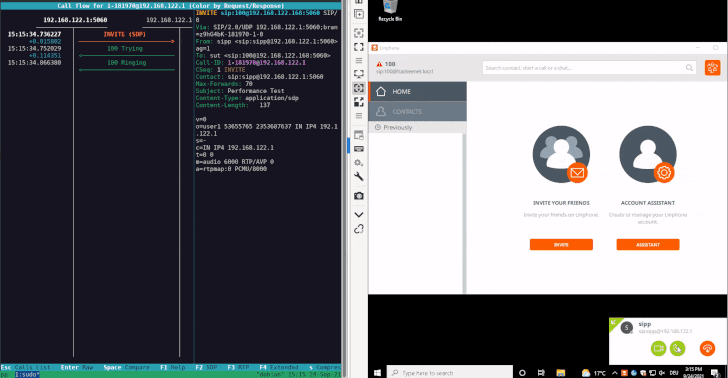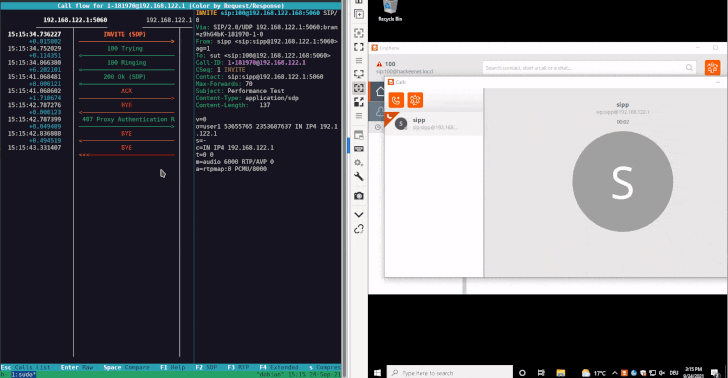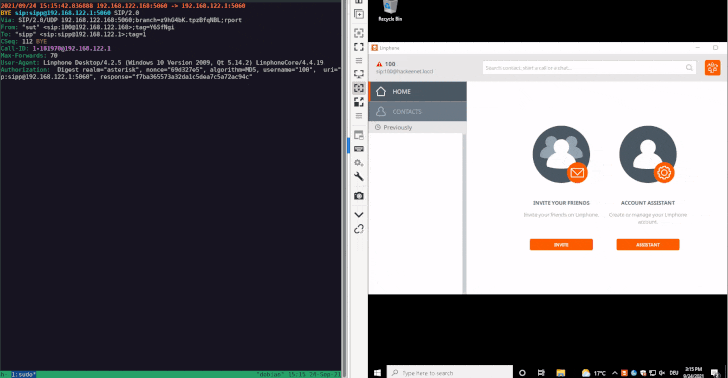
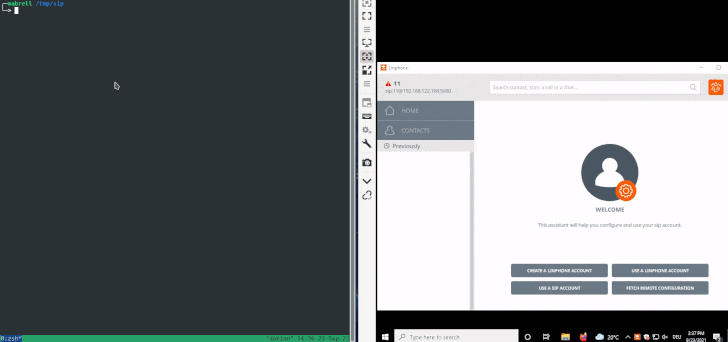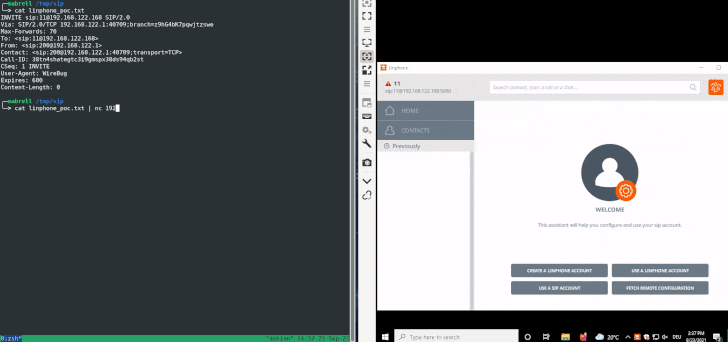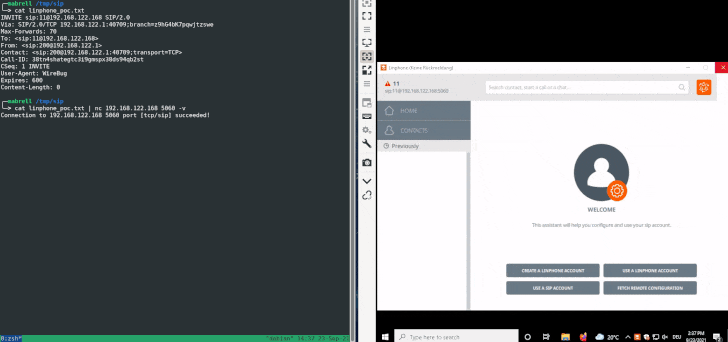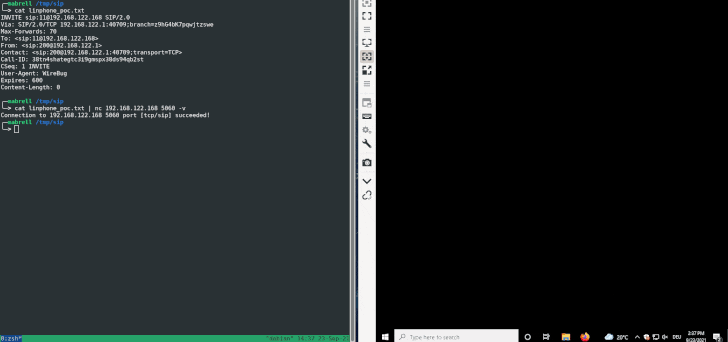
A typical session in SIP commences with a user agent (aka endpoint) sending an INVITE message to a peer through SIP proxies — which are used to route requests — that, when accepted on the other end by the recipient, results in the call initiator being notified, followed by the actual data flow. SIP invitations carry session parameters that allow participants to agree on a set of compatible media types.
The attack devised by SySS is what’s called a SIP Digest Leak, which involves sending a SIP INVITE message to the target softphone to negotiate a session followed by sending a “407 proxy authentication required” HTTP response status code, indicating the inability to complete the request because of a lack of valid authentication credentials, prompting the softphone to respond back with the necessary authentication data.
“With this information, the attacker is able to perform an offline password guessing attack, and, if the guessing attack is successful, obtain the plaintext password of the targeted SIP account,” Abrell explained. “Therefore, this vulnerability in combination with weak passwords is a significant security issue.”
Also discovered is a NULL pointer dereference vulnerability in the Linphone SIP stack that could be triggered by an unauthenticated remote attacker by sending a specially crafted SIP INVITE request that could crash the softphone. “A missing tag parameter in the From header causes a crash of the SIP stack of Linphone,” Abrell said.
The disclosure is the second time a NULL pointer dereference vulnerability has been discovered in the Linphone SIP client. In September 2021, Claroty made public details of a zero-click flaw in the protocol stack (CVE-2021-33056) that could be remotely exploited without any action from a victim to crash the SIP client and cause a denial-of-service (DoS) condition.
“The security level of SIP stacks still needs improvement,” Abrell said, calling the need for a defense-in-depth approach that entails “defining and implementing appropriate security measures for the secure operation of unified communication systems.”