Cybersecurity researchers on Tuesday took the wraps off a mass volume email attack staged by a prolific cybercriminal gang affecting a wide range of industries, with one of its region-specific operations notably targeting Germany and Austria.
Enterprise security firm Proofpoint tied the malware campaign with high confidence to TA505, which is the name assigned to the financially motivated threat group that’s been active in the cybercrime business since at least 2014, and is behind the infamous Dridex banking trojan and other arsenals of malicious tools such as FlawedAmmyy, FlawedGrace, Neutrino botnet, and Locky ransomware, among others.
The attacks are said to have started as a series of low-volume email waves, delivering only several thousand messages in each phase, before ramping up in late September and as recently as October 13, resulting in tens to hundreds of thousands of emails.
“Many of the campaigns, especially the large volume ones, strongly resemble the historic TA505 activity from 2019 and 2020,” the researchers said. “The commonalities include similar domain naming conventions, email lures, Excel file lures, and the delivery of the FlawedGrace remote access trojan (RAT).”
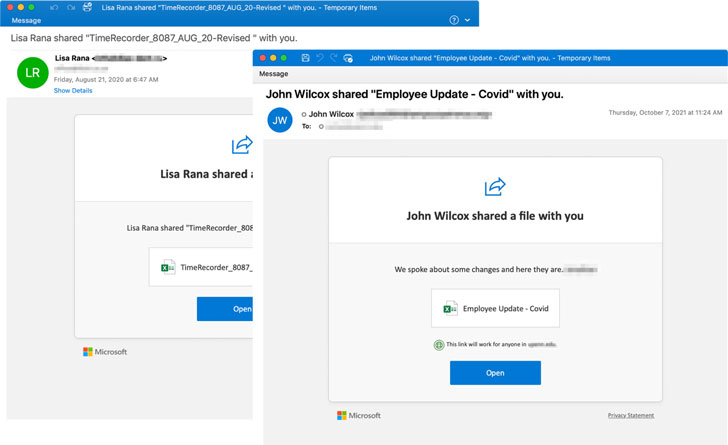
The group has a track record of striking research institutes, banks, retail businesses, energy companies, healthcare institutions, airlines, and government agencies for profit-seeking motives, with the malicious activities typically commencing upon opening malware-laced attachments in phishing messages purported to be related to COVID-19 updates, insurance claims, or notifications about Microsoft OneDrive shared files.
“Over time, TA505 evolved from a lesser partner to a mature, self-subsisting and versatile crime operation with a broad spectrum of targets,” NCC Group said in an analysis published in November 2020. “Throughout the years the group heavily relied on third party services and tooling to support its fraudulent activities, however, the group now mostly operates independently from initial infection until monetization.”
The success of the latest campaign, however, hinges on users enabling macros after opening the malicious Excel attachments, post which an obfuscated MSI file is downloaded to fetch next-stage loaders before the delivery of an updated version of the FlawedGrace RAT that incorporates support for encrypted strings and obfuscated API calls.
FlawedGrace — first observed in November 2017 — is a fully-featured remote access trojan (RAT) written in C++ that’s deliberately designed to thwart reverse-engineering and analysis. It comes with a roster of capabilities that allow it to establish communications with a command-and-control server to receive instructions and exfiltrate the results of those commands back to the server.
The actor’s October attack wave is also significant for its shift in tactics, which include the use of retooled intermediate loaders scripted in unusual languages like Rebol and KiXtart in place of Get2, a downloader previously deployed by the group to perform reconnaissance, and download and install final-stage RAT payloads.
“TA505 is an established threat actor that is financially motivated and known for conducting malicious email campaigns on a previously unprecedented scale,” Proofpoint said. “The group regularly changes their TTPs and are considered trendsetters in the world of cybercrime. This threat actor does not limit its target set, and is, in fact, an equal opportunist with the geographies and verticals it chooses to attack.”
“This combined with TA505’s ability to be flexible, focusing on what is the most lucrative and shifting its TTPs as necessary, make the actor a continued threat,” the cybersecurity firm added.