Microsoft 365 (M365), formerly called Office 365 (O365), is Microsoft’s cloud strategy flagship product with major changes ahead, such as the deprecation of their legacy authentication protocols.
Often stored on or saved to the device, Basic Authentication protocols rely on sending usernames and passwords with every request, increasing the risk of attackers capturing users’ credentials, particularly if not TLS protected. Basic Authentication, while necessary for companies using legacy software, is unable to enforce MFA and is superseded by Modern Authentication.
The legacy settings have been on Microsoft’s radar to fix for years. In 2018, Microsoft announced it would introduce a series of changes — and ultimately deprecation — to its authentication controls as a means to help organizations mitigate the risk. These changes were set to take place over a number of years, and in September 2021, they announced that they will begin to permanently disable Basic Auth in all tenants, regardless of usage, with the exception of SMTP Auth by late 2022.
In order to enable a smooth transition from these legacy protocols to a modern environment, Adaptive Shield has created a step-by-step guide to help you reduce risk and reinforce your organization’s M365 security.
Adaptive Shield has also developed and released a PowerShell script that creates a unified report to map out the organization’s posture to know which users have legacy protocols enabled — for you to copy-paste. This article covers the broad strokes of the guide from the discovery techniques and blocking access processes while showing you how to handle special exclusions.
To download the full guide with all the scripts, click here.
List of Basic Authentication Protocols
To secure the organization’s deployment, the first step is knowing what types of basic authentication protocols exist. Within Microsoft, the considered basic/legacy protocols include:
- Authenticated SMTP – Used by POP and IMAP clients to send email messages
- Autodiscover – Used by Outlook and EAS clients to find and connect to mailboxes in Exchange Online
- Exchange ActiveSync (EAS) – Used to connect to mailboxes in Exchange Online
- Exchange Online PowerShell – Used to connect to Exchange Online with remote PowerShell
- Exchange Web Services – A programming interface that’s used by Outlook, Outlook for Mac, and third-party apps
- IMAP – Used by IMAP email clients, allowing users to access email from anywhere and any device
- MAPI over HTTP – Used by Outlook 2010 and later
- OAB (Offline Address Book) – A copy of address list collections that are downloaded and used by Outlook
- Outlook Service – Used by the Mail and Calendar app for Windows 10
- POP3 – Used by POP email clients to download new messages and delete them from the email serverReporting Web Services
- Other clients – Any other protocols identified as utilizing legacy authentication
These authentication protocols do not support modern authentication mechanisms like multi-factor authentication (MFA), which means that enabling MFA won’t suffice.
To enhance security and mitigate risk, organizations must find all the users and services that use the legacy protocols, migrate to use modern protocols, and block the basic ones.
This whitepaper will take you through the discovery and blocking process, in addition to sharing instructions for additional controls, like Mailbox services and Conditional Access policies, that can reinforce your Microsoft 365 security posture.
Discovery: Know Your Posture
Before shutting down all legacy protocols within the organization, it is important to identify users and services that are using basic authentication. Rather than reduce productivity and generate user frustration, it is important to let users know that the system is being upgraded, which will help avoid business interruptions and promote a painless transition to modern protocols.
The are a few ways to learn about your organization’s posture using these methods:
- Powershell script – shows which users have the exchange legacy protocols enabled
- Conditional Access Report – shows actual usage of the basic authentication protocols
- Azure AD Sign-In Logs – shows sign-ins performed with legacy authentication clients
PowerShell Script
Running the PowerShell script acts as a good starting point to map out the user and service landscape that needs to be mitigated.
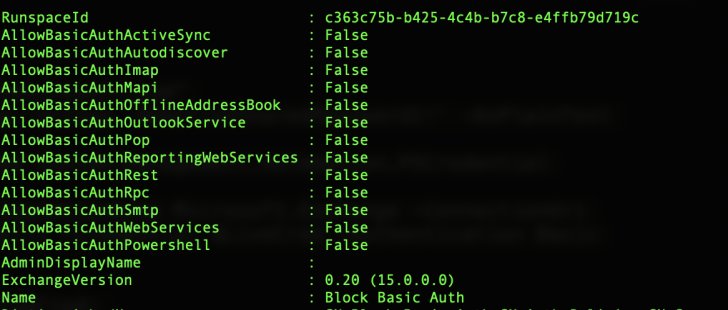
After running a few Powershell cmdlets, the Adaptive Shield team created this PowerShell script (See complete guide for the script ) to merge them all into one unified report. The script generates a file: BasicProtocolsReport.csv. This file will show users and their legacy protocol statuses. Each protocols’ status is tested against Authentication Policy, Mailbox services, and Transport config. Below is the list of the full payload:
- user
- has_mailbox – Indicates if the user has a mailbox licensed
- blocked – Account status (enabled/disabled)
- mfa – Multi Factor Authentication enrollment status
- auth_policy – Name of effective authentication policy (if set)
- is_ap_def – Indicates whether the effective authentication policy is an organization default or specifically assigned to the user
- protocol columns (activesync, imap, mapi, pop, smtp, outlookservice, powershell, ExchangeWebServices, autodiscover, OfflineAddressBook, rpc, ReportingWebServices) – Status (TRUE – enabled; FALSE – blocked)
- protocl_method columns (activesync, imap, mapi, pop, smtp, outlookservice) – Each of these protocols can be blocked using mailbox services settings, authentication policy, and transport config (global settings for SMTP) this column’s details which methods are in place to block these protocols.
Conditional Access – Report-Only
Create a report with Conditional Access (see figure 1) which simulates the users and services that would be affected if you were to block basic authentication protocols. This report gives you visibility into the users and services actually using the legacy protocols.
The suggested run time for this report is three months, over a business quarter, to catch any idle users, and sporadic or time-scheduled services.
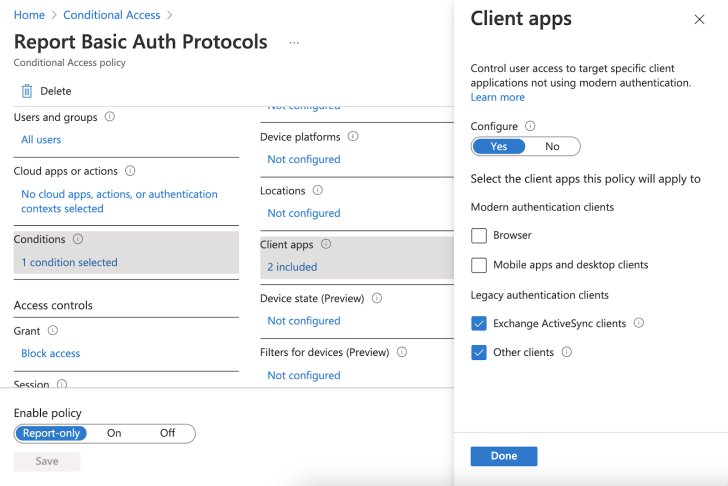 |
| Figure 1: Generate a user and services report over a 3-month period |
Reviewing the report and cross referencing it with the PowerShell script results will help you to have a better picture of legacy protocols in use, lowering the possibility of missing services or users that still have basic authentication protocols in play.
Azure AD Sign-In Logs
The Azure AD sign-in logs are another useful way to know your posture. Diving into the logs and filtering “Client app” can reveal sign-ins performed with legacy authentication clients.
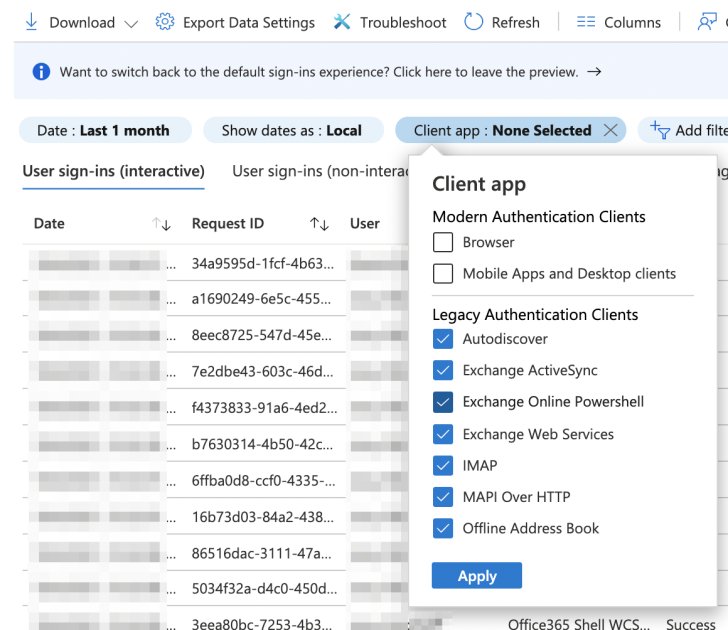 |
| Figure 2: Reveal sign-ins performed with legacy authentication clients |
Just note that the Azure sign-in logs’ retention is up to 30 days and you may end up missing users and services if this is the only tactic used.
Learn how an SSPM solution can automate this process for you.
Blocking Access
After carefully investigating and discovering all of the usage of basic authentication protocols, it is time to block them.
There are a few well-known approaches to blocking authentication protocols, a popular one being using the Conditional Access policies.
However, there are drawbacks to using Conditional Access as the first line of defense.
Conditional Access policies are processed post first-factor authentication. This means that the credentials can be compromised (as feedback will still be provided to the client, an advantage in a brute force attack for instance), so the mailbox might not have been breached but the attacker can try the validated password on other systems.
Authentication Policies
Start at the source. Microsoft has a dedicated feature for blocking basic authentication protocols, making it easy to control using the Admin console.
Go to the Office Admin center -> Settings -> Org Settings -> Modern authentication and uncheck all of the basic authentication protocols (make sure that modern authentication is checked). See Figure 3.
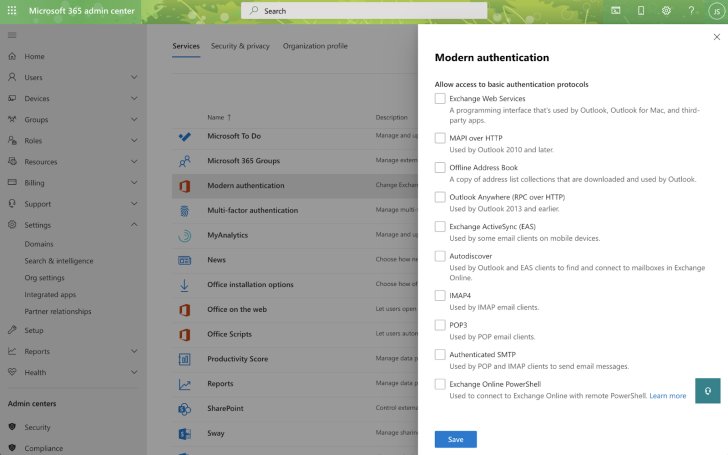 |
| Figure 3: All basic authentication protocols are unchecked |
Changing settings in the admin center creates a new authentication policy and sets it as the organization’s default policy.
Use PowerShell to validate:
$default_policy = Get-OrganizationConfig | Select DefaultAuthenticationPolicy;
Get-AuthenticationPolicy $default_policy.DefaultAuthenticationPolicy;
You can set exceptions and assign different authentication policies to specific users using PowerShell commands:
New-AuthenticationPolicy -Name “Engineering Group” -AllowBasicAuthImap
Set-User -Identity <UserIdentity> -AuthenticationPolicy <PolicyIdentity>
This example creates a new authentication policy named Engineering Group that allows basic authentication with IMAP and assigns it to a user.
Authentication policies are a must but not enough to stop the threat risk of these legacy protocols alone. The authentication policy covers legacy clients, mailbox protocols such as IMAP and SMTP, and other clients such as PowerShell. However, like Conditional Access, even though the service is blocked, some clients will still provide feedback (allowing certain cyberattacks to succeed in gleaning a password for application in other SaaS apps). To avoid this incriminating feedback, completely turn off the service.
Shutting down a service can only be done for mailboxes, which covers six protocols out of the 13. Blocking the authentication policy covers the rest.
Mailbox Services and Transport Config
Disabling a mailbox service (or enabling in case of exclusion) can be done using the UI per user.
Go to the Office Admin center -> Users -> Active users -> select a user (with mailbox) -> Mail tab -> Manage email apps and uncheck the basic authentication protocols: POP, IMAP, SMTP. See figure 4.
Note that SMTP, MAPI over HTTP, and Mobile (Exchange ActiveSync) support both basic and modern authentication.
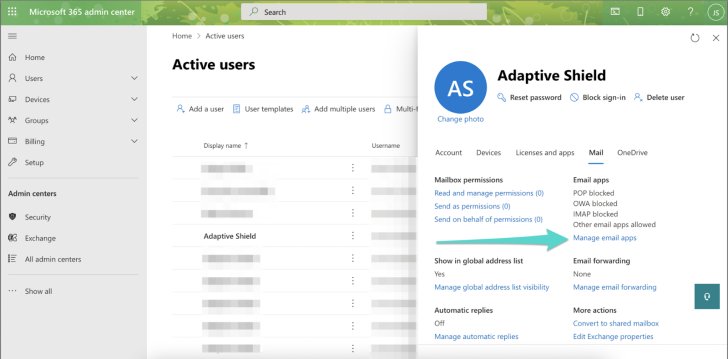 |
| Figure 4. Basic authentication protocols are unchecked |
There is no SMTP bulk edit multiple mailboxes (POP and IMAP bulk edit can be found in the classic Exchange Admin Center).
Transport config controls the entire Exchange organization, and one of its capabilities is to turn off the SMTP service (both basic and modern).
Use PowerShell command to disable SMTP globally.
Set-TransportConfig -SmtpClientAuthenticationDisabled $true
In order to block basic authentication protocols for all mailboxes or subset use Powershell cmdlets:
$Users = Get-CASMailbox -ResultSize unlimited
$Users | foreach {Set-CASMailbox -Identity $_ -SmtpClientAuthenticationDisabled $true -ActiveSyncEnabled $false -ImapEnabled $false -MapiEnabled $false -PopEnabled $false -OWAEnabled $false}
Exclusions
There are cases that you might consider excluding and allowing legacy protocols. For example, a manager who is using an older device or a script that was developed using the legacy protocols and now needs to be redeveloped might require an exclusion.
In these cases, it is strongly recommended to:
- Document: Have a procedure in place for requests and their reasoning
- Limit: Put in place a time period that will allow the requester time to resolve the issue that they need the legacy protocols, whether replacing the device or time to rewrite the code, etc.
- Conditional Access: Use compensating controls by allowing only specific devices, or put in place IP restrictions, geofencing, and more with the Conditional Access policies.
Conclusion
Managing SaaS configurations in an enterprise is complicated and this guide is meant to help ease the pain and smooth the transition from the M365 legacy protocols to a modern environment. The process has multiple steps and requires continuous oversight. From the discovery of the legacy authentication protocols opened and used by users and business processes to blocking access and implementing and managing the exclusions, security teams need to dive in, remediate and manage every problematic use of the authentication protocol.
In large-scale environments, where changes always happen and configurations are in the thousands, it is recommended to manage SaaS misconfigurations with an automated SaaS Security Posture Management solution (SSPM).