Cisco Systems has released security updates to address vulnerabilities in multiple Cisco products that could be exploited by an attacker to log in as a root user and take control of vulnerable systems.
Tracked as CVE-2021-40119, the vulnerability has been rated 9.8 in severity out of a maximum of 10 on the CVSS scoring system and stems from a weakness in the SSH authentication mechanism of Cisco Policy Suite.
“An attacker could exploit this vulnerability by connecting to an affected device through SSH,” the networking major explained in an advisory, adding “A successful exploit could allow the attacker to log in to an affected system as the root user.” Cisco said the bug was discovered during internal security testing.
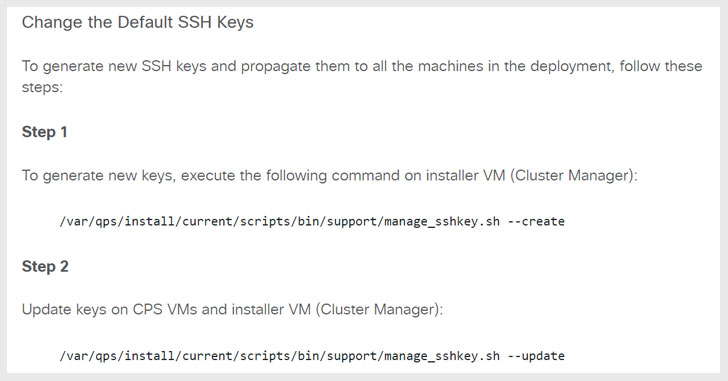
Cisco Policy Suite Releases 21.2.0 and later will also automatically create new SSH keys during installation, while requiring a manual process to change the default SSH keys for devices being upgraded from 21.1.0.
Also addressed by Cisco are multiple critical vulnerabilities affecting web-based management interface of the Cisco Catalyst Passive Optical Network (PON) Series Switches Optical Network Terminal (ONT) that could enable an unauthenticated, remote attacker to log in using an inadvertent debugging account existing in the device and take over control, perform a command injection, and modify the configuration of the device.
The vulnerabilities impact the following devices —
- Catalyst PON Switch CGP-ONT-1P
- Catalyst PON Switch CGP-ONT-4P
- Catalyst PON Switch CGP-ONT-4PV
- Catalyst PON Switch CGP-ONT-4PVC
- Catalyst PON Switch CGP-ONT-4TVCW
Marco Wiorek of Hotzone GmbH has been credited with reporting the three vulnerabilities that have been assigned the identifiers CVE-2021-34795 (CVSS score: 10.0), CVE-2021-40113 (CVSS score: 10.0), and CVE-2021-40112 (CVSS score: 8.6).
Lastly, Cisco has remediated two more high-severity flaws in Cisco Small Business Series Switches and Cisco AsyncOS that could allow unauthenticated, remote adversaries to gain unauthorized access to the web-based management interface of the switches and carry out a denial of service (DoS) attack —
- CVE-2021-34739 (CVSS score: 8.1) – Cisco Small Business Series Switches session credentials replay vulnerability
- CVE-2021-34741 (CVSS score: 7.5) – Cisco Email Security Appliance (ESA) denial of service vulnerability