An ongoing mobile spyware campaign has been uncovered snooping on South Korean residents using a family of 23 malicious Android apps to siphon sensitive information and gain remote control of the devices.
“With more than a thousand South Korean victims, the malicious group behind this invasive campaign has had access to all the data, communications, and services on their devices,” Zimperium researcher Aazim Yaswant said. “The victims were broadcasting their private information to the malicious actors with zero indication that something was amiss.”
The Dallas-based mobile security company dubbed the campaign “PhoneSpy.”
Zimperium did not attribute the spyware to a known threat actor. “The evidence surrounding PhoneSpy shows a familiar framework that has been passed around for years, updated by individuals and shared within private communities and back channels until assembled into what we see in this variation today,” Richard Melick, the company’s director of product strategy for endpoint security, told The Hacker News.
The rogue apps have been found to masquerade as seemingly innocuous lifestyle utilities with purposes ranging from learning Yoga and browsing photos to watching TV and videos, with the malware artifacts not relying on Google Play Store or other third-party unofficial app marketplaces, implying a social engineering or web traffic redirection method to trick users into downloading the apps.
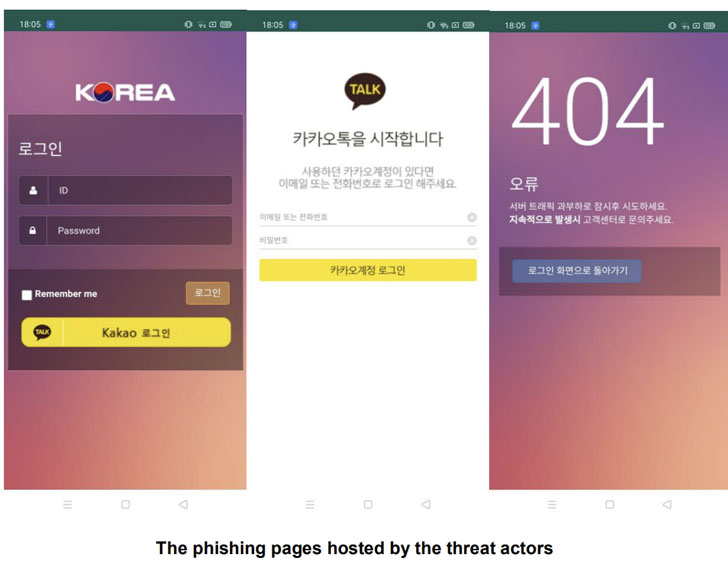
Post installation, the application requests for a wide range of permissions before opening a phishing site that’s designed to resemble the login pages of popular apps such as Facebook, Instagram, Google, and Kakao Talk. Users who attempt to sign in, however, are greeted by a HTTP 404 Not Found message, but in reality, have their credentials stolen and exfiltrated to a remote command-and-control (C2) server.
“Many of the applications are facades of a real app with none of the advertised user-based functionality,” Yaswant explained. “In a few other cases, like simpler apps that advertise as photo viewers, the app will work as advertised all while the PhoneSpy spyware is working in the background.”
Like other trojans, PhoneSpy abuses its entrenched permissions, enabling the threat actor to access the camera to take pictures, record video and audio, get precise GPS location, view pictures from the device, as well as extract SMS messages, contacts, call logs, and even send SMS messages to the phone with attacker-controlled text. The amassed data is then shared with the C2 server.
“Mobile spyware is an incredibly powerful and effective weapon against the data we hold in our hands. As our phones and tablets continue to become the digital wallets and IDs, forms of multi factor authentication, and the keys to the data kingdom for our professional and personal lives, the malicious actors wanting that exact data will find new ways to steal it,” Melick said.
“PhoneSpy and other examples of mobile spyware show that these toolsets and frameworks can be broken down and rebuilt over and over again with updated code and capabilities, giving the attackers the upper hand. And it’s only increasing in popularity for everyone from nation states targeting dissidents to corporations spying on competition due to the lack of advanced security surrounding most of these critical devices.”