Google on Tuesday said it took steps to disrupt the operations of a sophisticated “multi-component” botnet called Glupteba that approximately infected more than one million Windows computers across the globe and stored its command-and-control server addresses on Bitcoin’s blockchain as a resilience mechanism.
As part of the efforts, Google’s Threat Analysis Group (TAG) said it partnered with the CyberCrime Investigation Group over the past year to terminate around 63 million Google Docs that were observed to have distributed the malware, alongside 1,183 Google Accounts, 908 Cloud Projects, and 870 Google Ads accounts that were associated with its distribution.
Google TAG said it worked with internet infrastructure providers and hosting providers, such as CloudFlare, to dismantle the malware by taking down servers and placing interstitial warning pages in front of the malicious domains.
In tandem, the internet giant also announced a lawsuit against two Russian individuals, Dmitry Starovikov and Alexander Filippov, who are alleged to be responsible for managing the botnet alongside 15 unnamed defendants, calling the enterprise a “modern technological and borderless incarnation of organized crime.”
“Glupteba is known to steal user credentials and cookies, mine cryptocurrencies on infected hosts, deploy and operate proxy components targeting Windows systems and IoT devices,” TAG researchers Shane Huntley and Luca Nagy said, with the botnet observed targeting victims worldwide, including the U.S., India, Brazil, and Southeast Asia.
Glupteba was first publicly documented by Slovak internet security company ESET in 2011. Last year, cybersecurity firm Sophos published a report on the dropper, noting it “was able to continuously thwart efforts at removing it from an infected machine,” adding “Glupteba also takes a variety of approaches to lay low and avoid being noticed.”
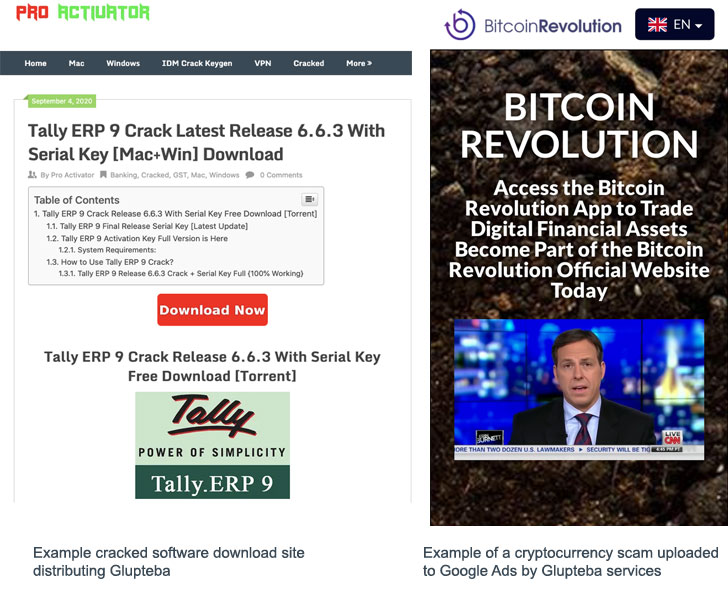
Primarily disseminated through sketchy third-party software and online movie streaming sites, the modular botnet camouflages as free software and YouTube videos that, post-installation, can be orchestrated to take advantage of its illicit access to the devices to retrieve additional components and further a number of criminal schemes, including —
- Stealing personal account information and selling the access to third-parties on a portal called “Dont[.]farm”
- Vending credit cards to facilitate fraudulent purchases from Google Ads and other Google services
- Selling unauthorized access to the devices for use as residential proxies via “AWMProxy[.]net” to conceal the activities of bad actors
- Serving disruptive pop-up ads on the compromised machines, and
- Hijacking the computing power of the devices to mine cryptocurrency
But in an interesting twist, rather than selling those stolen credentials directly to other criminal customers, the Glupteba operators pawned the access through virtual machines that were preloaded with those accounts by logging in using the siphoned usernames and passwords on a web browser.
“Dont.farm’s customers pay the Glupteba Enterprise in exchange for the ability to access a browser that is already logged into a victim’s stolen Google account,” the company alleged. “Once granted access to the account, the Dont[.]farm customer has free rein to use that account however they desire, including buying advertisements and launching fraudulent ad campaigns, all without the true account owner’s knowledge or authorization.”
The downloaded modules, besides incorporating measures to keep it invisible to detection by antivirus solutions, are designed to execute arbitrary commands pushed by an attacker-controlled server. Glupteba is also notable for the fact that unlike other traditional botnets, the malware leverages the Bitcoin blockchain as a backup command-and-control (C2) system.
Specifically, instead of relying solely on a list of predetermined and disposable domains either hard-coded in the malware or obtained using a domain generation algorithm (DGA), the malware is programmed to search the public Bitcoin blockchain for transactions involving three wallet addresses owned by the threat actor so as to fetch the encrypted C2 server address.
“Unfortunately, Glupteba’s use of blockchain technology as a resiliency mechanism is notable here and is becoming a more common practice among cyber crime organizations,” Google’s Royal Hansen and Halimah DeLaine Prado said. “The decentralized nature of blockchain allows the botnet to recover more quickly from disruptions, making them that much harder to shutdown.”
What’s more, the tech giant explained in its lawsuit that the cybercriminal gang maintained an online presence at “Voltronwork[.]com” to actively recruit developers by means of job openings on Google Ads to “support its websites, transactions, and overall operation.”
The legal move also comes a day after Microsoft disclosed it had seized 42 domains used by the China-based Nickel hacking group (aka APT15, Bronze Palace, Ke3Chang, Mirage, Playful Dragon, and Vixen Panda) to target servers belonging to government agencies, think tanks, and human rights organizations in the U.S. and 28 other countries worldwide.