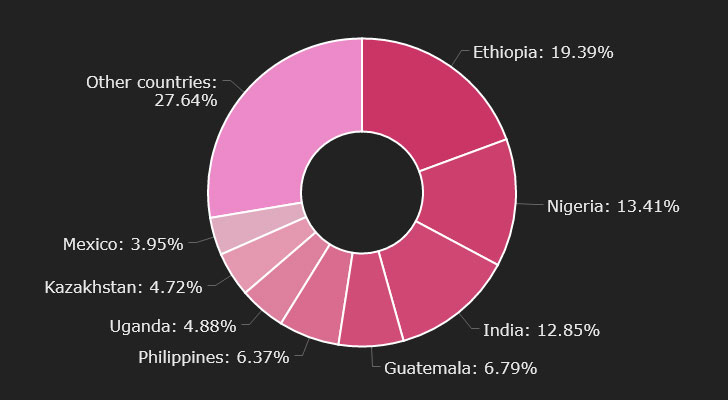
Cryptocurrency users in Ethiopia, Nigeria, India, Guatemala, and the Philippines are being targeted by a new variant of the Phorpiex botnet called Twizt that has resulted in the theft of virtual coins amounting to $500,000 over the last one year.
Israeli security firm Check Point Research, which detailed the attacks, said the latest evolutionary version “enables the botnet to operate successfully without active [command-and-control] servers,” adding it supports no less than 35 wallets associated with different blockchains, including Bitcoin, Ethereum, Dash, Dogecoin, Litecoin, Monero, Ripple, and Zilliqa, to facilitate crypto theft.
Phorpiex, otherwise known as Trik, is known for its sextortion spam and ransomware campaigns as well as cryptojacking, a scheme that leverages the targets’ devices such as computers, smartphones, and servers to secretly mine cryptocurrency without their consent or knowledge.
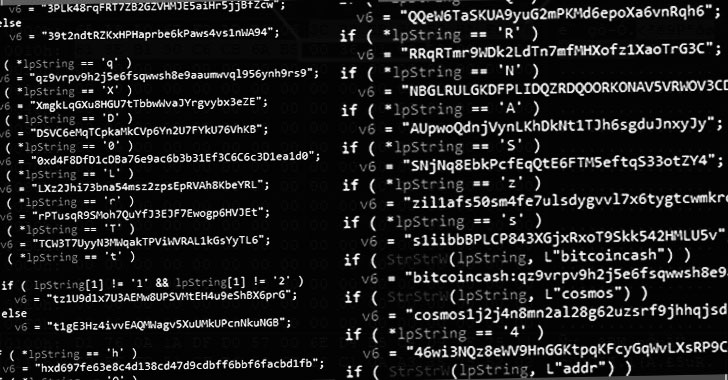
It’s also infamous for its use of a technique called cryptocurrency clipping, which involves stealing cryptocurrency in the process of a transaction by deploying malware that automatically substitutes the intended wallet address with the threat actor’s wallet address. Check Point said it identified 60 unique Bitcoin wallets and 37 Ethereum wallets used by Phorpiex.
While the botnet operators shut down and put its source code for sale on a dark web cybercrime forum in August 2021, the command-and-control (C&C) servers resurfaced a mere two weeks later to distribute Twizt, a previously undiscovered payload that can deploy additional malware and function in peer-to-peer mode, thus eliminating the need for a centralized C&C server.
The clipping feature also comes with an added advantage in that, once deployed, it can work even in the absence of any C&C servers and siphon money from victims’ wallets. “This means that each of the infected computers can act as a server and send commands to other bots in a chain,” Check Point’s Alexey Bukhteyev said in a report. “The emergence of such features suggests that the botnet may become even more stable and therefore, more dangerous.”
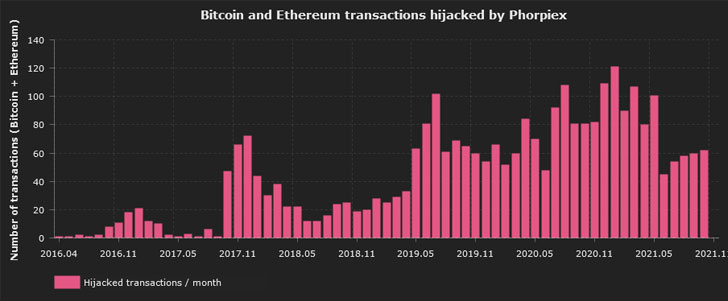
Phorpiex-infected bots have been spotted in 96 countries, topped by Ethiopia, Nigeria, and India. The botnet is also estimated to have hijacked roughly 3,000 transactions with a total value of approximately 38 Bitcoin and 133 Ether. It’s, however, worth noting that the botnet is designed to halt its execution should the infected system’s locale be defaulted to Ukraine, suggesting that the botnet operators are from the East European nation.
“Malware with the functionality of a worm or a virus can continue to spread autonomously for a long time without any further involvement by its creators,” Bukhteyev said. “In the past year, Phorpiex received a significant update that transformed it into a peer-to-peer botnet, allowing it to be managed without having a centralized infrastructure. The C&C servers can now change their IP addresses and issue commands, hiding among the botnet victims.”