Researchers have disclosed a novel technique by which malware on iOS can achieve persistence on an infected device by faking its shutdown process, making it impossible to physically determine if an iPhone is off or otherwise.
The discovery — dubbed “NoReboot” — comes courtesy of mobile security firm ZecOps, which found that it’s possible to block and then simulate an iOS rebooting operation, deceiving the user into believing that the phone has been powered off when, in reality, it’s still running.
The San Francisco-headquartered company called it the “ultimate persistence bug […] that cannot be patched because it’s not exploiting any persistence bugs at all — only playing tricks with the human mind.”
NoReboot works by interfering with the routines used in iOS to shutdown and restart the device, effectively preventing them from ever happening in the first place and allowing a trojan to achieve persistence without persistence as the device is never actually turned off.
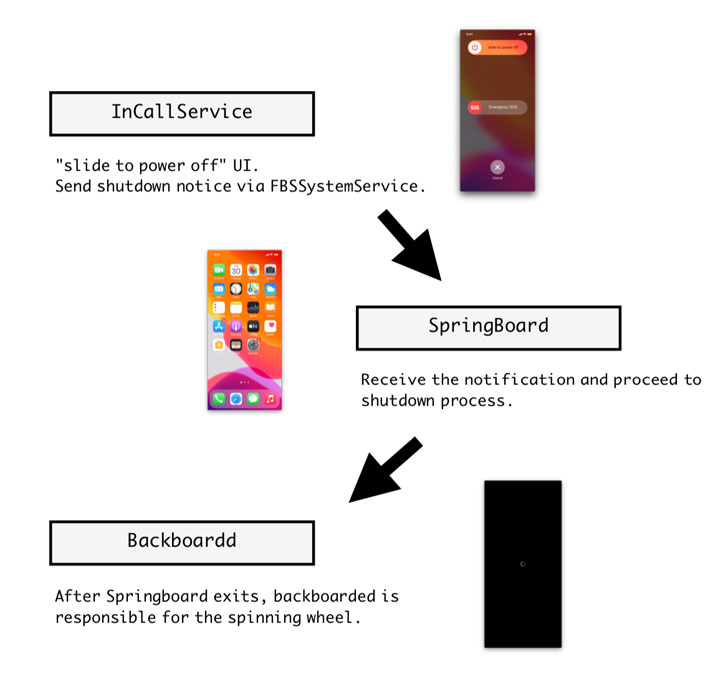
This is accomplished by injecting specially crafted code onto three iOS daemons, namely the InCallService, SpringBoard, and Backboardd, to feign a shut down by disabling all audio-visual cues associated with a powered-on device, including the screen, sounds, vibration, the camera indicator, and touch feedback.
Put differently, the idea is to give the impression that the device has been shut down without really shutting it down by hijacking the event that’s activated when the user simultaneously presses and holds the side button and one of the volume buttons, and drags the “slide to power off” slider.
“Despite that we disabled all physical feedback, the phone still remains fully functional and is capable of maintaining an active internet connection,” the researchers explained. “The malicious actor could remotely manipulate the phone in a blatant way without worrying about being caught because the user is tricked into thinking that the phone is off, either being turned off by the victim or by malicious actors using ‘low battery’ as an excuse.”
The malware strain then forces the SpingBoard, which refers to iOS’s graphical user interface, to exit (as opposed to the entire OS), followed by commanding the BackBoardd, the daemon that handles all touch and physical button click events, to display the Apple logo effect should the user opt to turn the running phone back on, while the malicious code continues to persist.
What’s more, this technique could be theoretically extended to manipulate a force restart associated with an iPhone by deliberately causing the Apple logo to appear a few seconds earlier when such an event is recorded via the Backboardd, fooling the victim into releasing the side button without genuinely triggering a force restart.
Although no malware to date has been detected or publicly documented using a method resembling NoReboot, the findings highlight that even the iOS restart process isn’t immune to being hijacked once an adversary has gained access to a target device, something that’s well within the reach of nation-state groups and cyber mercenaries alike.
“Non-persistent threats achieved ‘persistency’ without persistence exploits,” the researchers concluded. A proof-of-concept (PoC) exploit demonstrating NoReboot can be accessed via GitHub here.